How do companies protect customer data?
Companies can protect customer data through various technical tools and strategies, like authentication and encryption. But some types of data need more protection than others.
Data breaches have become an everyday reality for many organizations, whose customers feel the effects of identity theft and other fraudulent activities.
Business operations require the exchange of customer information, but companies that take customer data security seriously can build trust between themselves and their customers. To protect customer data, organizations must maintain compliance and invest in technologies like AI and machine learning to boost security to benefit their operations and customer relationships.
What kind of customer information must be secured?
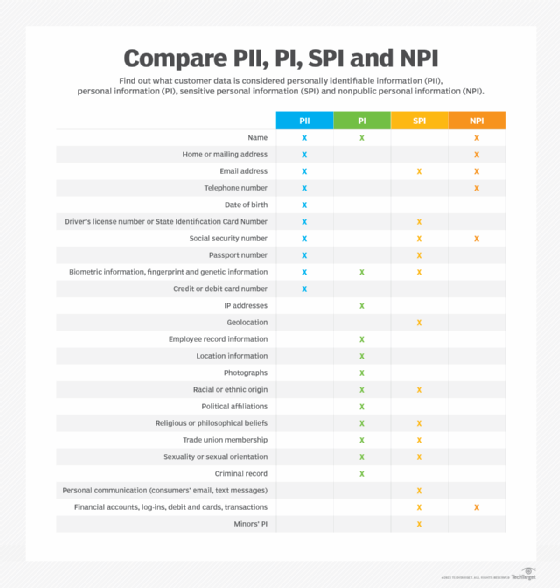
As companies prepare their data security policies, they should prioritize protecting the following types of customer information:
- Personally identifiable information. PII refers to information that can distinguish or trace a person's identity by itself or with other personal or identifying information linked to that individual.
- Personal information. PI can directly or indirectly identify, relate to or describe a person or household. PI is relatively broad and can include data associated with someone's identity, often overlapping with PII.
- Sensitive personal information. SPI came into the privacy lexicon under the California Privacy Rights Act -- an amendment to CCPA. SPI covers personal data that does not directly identify an individual but might cause harm if made public. It also protects minors and their PI.
- Nonpublic personal information. NPI is a type of sensitive information that the Gramm-Leach-Bliley Act introduced. It specifically regulates financial services institutions and includes information they obtain directly from customers or through transactions. NPI does not include publicly available information.
Policies and regulations for data protection
The two most well-known customer data protection policies are GDPR and CCPA. In addition, at least 15 states have data protection laws related to privately and publicly owned companies.
General Data Protection Regulation
GDPR sets guidelines for businesses that collect and process personal information from individuals who live in the European Union. GDPR applies regardless of where websites are based, meaning all sites that attract European visitors must follow these guidelines, even if they don't specifically market goods or services to EU residents.
California Consumer Privacy Act
CCPA became law on Jan. 1, 2020, and is the United States' strictest data privacy regulation for consumer rights. It aims to protect California-based consumers' rights related to how businesses collect, use, store and sell personal data -- primarily PII.
To protect customer data, organizations can take the following steps:
- Collect only data vital to doing business with customers.
- Limit who can access customer data.
- Boost cybersecurity and control access through password management tools.
- Implement a strong data management strategy, and store data in a centralized location.
- Set minimum security standards with which the organization complies. For example, any tool must comply with either ISO 27001 or System and Organization Controls 2.
Technology to protect customer data
Before organizations invest in security technologies, they should determine if they already have internal safeguards to protect data and properly assess the organization's unique cybersecurity needs to select the right technology -- especially when it comes to AI -- to ensure optimal protection against evolving cyberthreats. Safeguards might include the following:
- CRM tools to maintain customer data in a centralized location. CRM platforms can account for where data resides and avoid storing data in multiple areas.
- Two-factor authentication (2FA) requires customers to use short-term passwords or codes -- ranging from minutes to a few days -- in conjunction with long-term passwords. This authentication method can cut down on breaches associated with compromised passwords.
Beyond CRM tools and 2FA, organizations should look into the following technologies to protect customer data.
Encryption
Encryption is a common way to protect customer data from bad actors, and organizations have different types of encryption they can choose from:
- File-level encryption can protect data in transit and make it harder for hackers to access cloud-based software or resources. Providers include McAfee and Microsoft. Organizations with on-premises hardware should use a disk encryption offering, such as Apple FileVault 2.
- Advanced Encryption Standard (AES) using a 256-bit key to encrypt and decrypt data. Many experts consider AES-256 a gold standard for block ciphers. Providers include IBM and Microsoft.
- Portable mode encryption is a type of file-level encryption. Some employees use devices like key fobs and USB drives to store files, which can cause organizations to struggle to enforce security protocols on them. Portable mode protects against breaches in case a USB or portable hard drive is lost or stolen. Providers include TruPax and Kaspersky.
Integrated malware protection
Cybercriminals can steal data without a user's knowledge. Malware protection -- also known as antivirus protection -- acts as a firewall that organizations can integrate with existing software for additional device security. Providers include Bitdefender and McAfee.
Blockchain technology
Blockchain lets customers take ownership of their data without permissions, checks and authorizations. Further, blockchain is known for its ability to store data across a series of networks without needing a central location. Providers include IBM, Microsoft and Accubits.
AI and good customer data privacy practices
The rapid growth of AI across industries has driven the need to integrate privacy protection in AI models. AI, particularly machine learning, thrives on vast amounts of data, increasing the risk of data leakage. Businesses must account for this risk, especially when training models with large data sets, to respect privacy concerns and keep their models viable.
When implementing AI, organizations must consider whether the technology is necessary or if conventional methods can solve their problems. Introducing AI and generative AI into processes requires a comprehensive architecture to build, train and deploy models to process large amounts of data.
Choosing the type of AI technology most appropriate for integration into your organization's data security strategy should be based on compatibility, scalability and user-friendliness.
The three most commonly used AI technologies are as follows:
- Machine learning uses algorithms to empower systems to learn from data and make predictions or decisions.
- Deep learning uses multilayered artificial neural networks to examine intricate patterns and make decisions.
- Natural language processing lets machines comprehend, interpret and respond to human language.
Despite its potential, AI is not infallible. Users must constantly stay up to date regarding advancements in the technology, retest their AI models and retrain employees to keep up with those changes. The abundance of big data gathered by organizations and AI's evolving capabilities will continue to challenge data privacy norms, necessitating responsible AI development that respects privacy principles. While AI can help detect and address threats, the importance of human expertise shouldn't be overlooked. The combined strength of AI and human insight offers a robust defense in preserving sensitive private data.
Editor's note: This article was updated to reflect today's data protection environment, including the influence of generative AI, and to improve the reader experience.
Sandra Mathis has more than 15 years' experience in consumer and customer insights and currently serves as a connect customer experience strategy program manager at Microsoft.






