Secure File Transfer Protocol (SSH File Transfer Protocol)
What is Secure File Transfer Protocol (SFTP)?
Secure File Transfer Protocol (SFTP) is a network protocol for securely accessing, transferring and managing large files and sensitive data.
Designed by the Internet Engineering Task Force as an extension of Secure Shell (SSH), SFTP enables access, transfer and management of files over a network. It's used for secure file transfers over Transport Layer Security and the transfer of data for virtual private network (VPN) applications.
SFTP helps enterprises meet regulations for file transfer compliance in accordance with HIPAA, GDPR and other regulatory rulings. SFTP also lets businesses securely transfer billing data, funds and data recovery files. Individuals may also use SFTP to encrypt their communications.
SFTP uses SSH to transfer files and requires that the client be authenticated by the server. Commands and data are encrypted to prevent passwords and other sensitive information from being exposed to the network in plain text.
How does SFTP work?
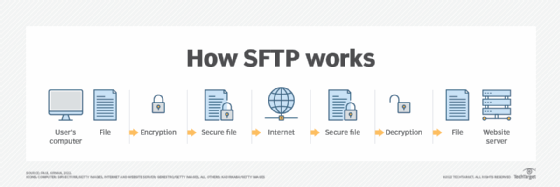
Secure File Transfer Protocol was developed to securely transfer and manage files over a TCP/IP network. SFTP uses the same commands as the standard File Transfer Protocol (FTP), and most SFTP commands are similar or identical to the Linux shell commands. SFTP performs numerous tasks, including transferring sensitive files, removing files and resuming paused transfers. To establish server connections, SFTP only needs to be connected to the normal SSH port 22.
SFTP also needs an SFTP client and server. An STFP client is software that lets users connect to a server and store files on the server. Files are stored and retrieved from the STFP server. When a user clicks on a file, the request travels through the network and ultimately reaches a server. This data is then sent to the requesting device. SFTP ensures all files are encrypted before transferring them.
SSH keys are typically used to automate access to servers and are often used in scripts, backup systems and configuration management tools. SSH keys in SFTP have half of the key stored on the client device, while the other half is on the server associated with a public key. Users are properly authenticated when SSH key pairs match.
SFTP works over an SSH data stream to establish a secure connection. Encryption algorithms securely move data to a server, keeping files unreadable during the process. To further prevent unauthorized file access, authentication is also enabled. Users can choose to be identified by a user ID and password, SSH keys or both.
What is SFTP used for?
SFTP is used to do the following:
- Comply with data standards. SFTP achieves file transfer compliance for industry regulations that protect how personal information is used.
- Keep data safe. SFTP provides security for data in transit to make sure hackers and unauthorized users can't access a user's data.
- Complement a VPN. VPNs are a service that creates a safe, encrypted online connection; they act as a secure and encrypted tunnel for data. Data can be sent using the SFTP protocol and a VPN, making the transfer more secure.
Advantages of SFTP
Advantages of SFTP include the following:
- Security. SFTP enables data security, encryption and public key authentication, which protect data in transit. The security makes SFTP a reliable file transfer option.
- Speed. SFTP supports large file transfers and transferring multiple files from one server to another simultaneously.
- Integration. SFTP integrates well with VPNs and firewalls.
- Management. SFTP can be managed through a web interface or an SFTP client.
Disadvantages of SFTP
Some disadvantages that come with SFTP include the following:
- Complexity. Even though SFTP is manageable, the process of creating and setting up an SFTP client is much more complicated than the process of creating an FTP client.
- Private key storage. SFTP private keys must be stored on the device that users want to transfer files from, and the device should also be protected.
- Possible compatibility problems. Standards around SFTP are described as optional and recommended, which may lead to compatibility issues in software developed by different vendors.
Examples of SFTP
Common SFTP commands include the following:
- sftp> put -- Upload a file
- sftp> get -- Download a file
- sftp> cd -- Change the active directory path
- sftp> pwd -- Display the remote working directory
- sftp> Icd -- Change the local system’s directory path
- sftp> lpwd -- Display the local working directory
- sftp> ls -- Display contents of the remote working directory
- sftp> lls -- Display content of the local working directory
- sftp> lmkdir -- Create a local directory
- sftp> lumask -- Change the umask value
- sftp> rename -- Rename a file on the remote host
- sftp> rm -- Delete a file on the remote host
What is the difference between SFTP vs. FTP?
FTP is a network protocol for transmitting files between computers over TCP/IP connections. FTP is considered an application layer protocol.
In an FTP transaction, the user's computer is called the local host. The second computer involved is the remote host, which is usually a server. Both devices must be connected by a network and configured properly to transfer files via FTP. FTP is used to transfer files behind the scenes for other applications. It's also sometimes used to download new applications via web browsers.
FTP differs from SFTP in the following ways:
- Security. While FTP isn't encrypted, SFTP encrypts the data before sending it to a host.
- Architecture. While FTP works in a client-server architecture, SFTP operates in an SSH architecture.
- Ports used. While FTP uses port 21 for inbound and outbound ports, SFTP enables incoming connections on port 22.
- Method of transfer. While FTP uses direct transfers, SFTP uses tunneling, which can protect all transmitted data and authentication credentials.
If keeping data secure is important or data security is needed for regulation, then use SFTP.
Learn more about FTP and 11 other common network protocols as well as their functions.







