
Getty Images
Create a private endpoint to secure Azure Functions apps
Don't overlook security and leave your functions exposed. Learn how private endpoints can add an extra layer of protection for your Azure Function apps.
Azure Functions enables developers to execute small pieces of code, or functions, in response to various events without the need to manage the underlying infrastructure. Multiple sources, such as HTTP requests, database operations and timer events, can trigger these functions.
With Azure Functions, developers can focus solely on their code, while Azure handles the scaling, maintenance and execution. This serverless architecture is ideal for building microservices, event-driven applications and automated tasks. It offers a cost-effective solution that charges only for the actual computing time used.
While there are numerous benefits, enterprises need to be proactive with security. Security is essential for Azure Functions for several reasons:
- Data protection. Azure Functions often interacts with sensitive data, whether its user information, transactional data or proprietary business information. Enterprises need to secure data to prevent unauthorized access and data breaches.
- Trustworthiness. For businesses and developers, the trustworthiness of an application or service is crucial. Malicious actors could exploit insecure Azure Functions, eroding trust among users and stakeholders.
- Compliance. Many industries have strict regulatory requirements regarding data handling and processing. Secure Azure Functions helps businesses maintain compliance and avoid legal repercussions and potential fines.
- Financial implications. A security breach can lead to financial losses, both directly through theft and indirectly through reputational damage, loss of customers and the cost of remediation.
- Integration concerns. Azure Functions often integrates with other services and applications. A security vulnerability in a function can expose or compromise these connected systems.
In this tip, learn the basics of a private endpoint, best practices, common mistakes to avoid and how to create a private endpoint.
What is a private endpoint?
Securing Azure Functions is not just about protecting a single function, but also safeguarding the entire ecosystem it interacts with, ensuring data integrity and maintaining trust.
A feature that helps protect Azure Functions is a private endpoint. This is a network interface that connects to a specific Azure service, such as Azure Functions, over a private link. It means the traffic between a virtual network and the Azure service is isolated from the public internet.
There are several benefits to using a private endpoint for Azure Functions:
- Increased security. Isolating traffic between a virtual network and Azure Functions helps protect data from unauthorized access.
- Improved performance. Private endpoints use Azure Private Link to route traffic directly between a virtual network and Azure Functions, which can improve performance.
- Reduced costs. With a private endpoint, enterprises can avoid paying for public internet egress traffic.
Private endpoint best practices
The key to using private endpoints is to ensure that the underlying network configuration exists as required. A few approaches and practices can help keep a private endpoint secure, controlled and easy to manage. A few of these are the following:
- Use a dedicated subnet for private endpoints. This helps to isolate private endpoints from other traffic in a virtual network.
- Enable Private Link on the Azure Functions app. Private Link must be enabled on the Azure Functions app to connect to the private endpoint.
- Use a service tag to control access to private endpoints. It helps to ensure that only authorized users can access private endpoints.
- Monitor private endpoints. Monitor private endpoints using Azure Monitor to ensure they are working correctly.
- Update private endpoints regularly. Update private endpoints regularly to ensure they are using the latest security features.
A few additional options are the following:
- Use a private DNS zone to resolve the private endpoint's IP address.
- Use a load balancer to distribute traffic to your Azure Functions app.
- Use a firewall to control access to your Azure Functions app.
Steps to create a private endpoint
To create a private endpoint for Azure Functions, you need the following:
- Azure subscription.
- Azure resource group.
- Virtual network.
- Subnet in the virtual network.
- Azure Functions app.
Step 1. Select a function template
Create an Azure function with one of the pre-built templates or use custom code. To do this, open Visual Studio, select New Project, choose Azure Function and then select the required template.
For this example, use the default Http trigger template, including all the sample code the template creates.
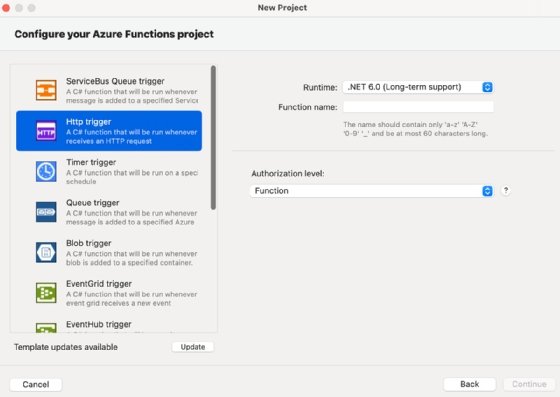
Complete the properties, and create the project. The following example code gets created by default when using the Microsoft Http trigger template -- the function name differs:
public static class funcAWZI0LK5
{
[FunctionName("funcAWZI0LK5")]
public static async Task<IActionResult> Run( [HttpTrigger(AuthorizationLevel.Anonymous, "get", "post", Route = null)] HttpRequest req,
ILogger log)
{
log.LogInformation("C# HTTP trigger function processed a request.");
string name = req.Query["name"];
string requestBody = await new StreamReader(req.Body).ReadToEndAsync();
dynamic data = JsonConvert.DeserializeObject(requestBody);
name = name ?? data?.name;
string responseMessage = string.IsNullOrEmpty(name) ? "This HTTP triggered function executed successfully. Pass a name in the query string or in the request body for a personalized response.": $"Hello, {name}. This HTTP triggered function executed successfully.";
return new OkObjectResult(responseMessage);
}
}
Step 2. Test the function
To test the function, navigate to the overview page to get the URL.
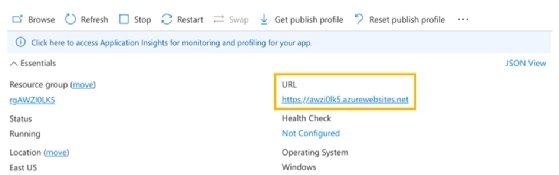
Browsing to the URL displays an Azure page saying the function works. To use the code for the function, append the URL with /API/function-name -- in the sample code, that is /API/HttpAWZI0LK5. Or, if you want to pass data to it, you can use something like /API/HttpAWZI0LK5?name=Liam Cleary.
The default configuration allows anyone to call the function because it makes the authorization method anonymous. It is best to change this to a more secure option unless you need anonymous access to the function. Modify the code to the desired setting, add any specific configuration to the function and republish to Azure.
Step 3. Add a private endpoint
To utilize the private endpoint for the Azure function, navigate into the function in Azure Portal, and choose Networking within the settings section.

There are various options available for networking within an Azure function. All these options are disabled, so you need to select the required option:
- Access restriction. This provides restrictions, allowing or denying access to specific IP addresses or subnets.
- App assigned address. It can be helpful if you need the app accessible online.
- Private endpoint. This ensures traffic between the virtual network and the Azure service is isolated from the public internet.
To utilize the private endpoint option, click on the link which takes you to the configuration options.
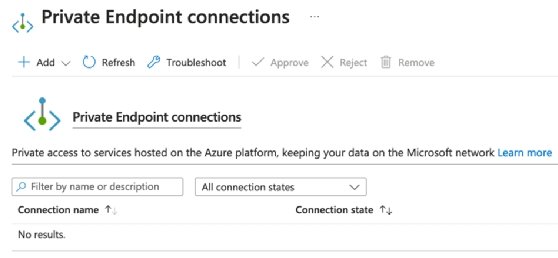
Click the Add option to add the private endpoint, and then choose either Express or Advanced. The express options require a few values and then create the private endpoint.
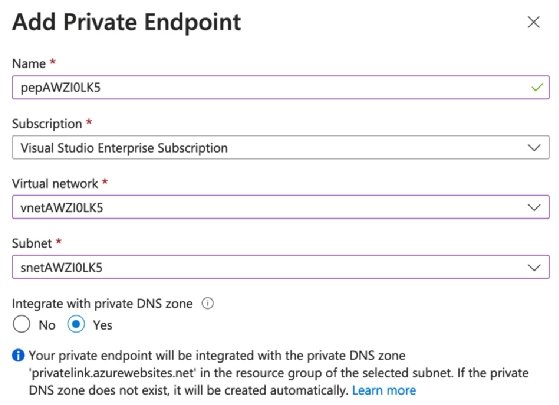
Once the private endpoint is created within the configuration, both the private endpoint and access restrictions options get enabled. When browsing to the original endpoint URL, you do not get a forbidden message.

It now blocks regular external access in favor of the new private endpoint link. Within the access restriction configuration, the Allow Public Access checkbox is now unchecked, which blocks access to the public endpoint for both the main and advanced tool sites. Add a local DNS entry that knows how to get to the assigned IP address for the private endpoint.
To further secure the function with the private endpoint, add an application gateway that controls the external routing back to the private endpoint. Or ensure you have a private link to the Azure tenant direct from the network that calls the function.
Common mistakes to avoid with private endpoints
There are a few common mistakes to avoid when creating private endpoints for Azure Functions:
- Wrong subscription or resource group. Use the correct subscription and resource group when creating the private endpoint. The private endpoint cannot connect to your Azure Functions app without the right selections.
- Private endpoint created in the wrong subnet. The private endpoint must be created in the same subnet as your Azure Functions app. If you create the private endpoint in the wrong subnet, the private endpoint is not able to connect to your Azure Functions app.
- Not enabling Private Link on the Azure Functions app. Enterprises need to enable Private Link on the Azure Functions app to connect to the private endpoint. If Private Link is not enabled, the Azure Functions app cannot connect to the private endpoint.
- Not using a dedicated subnet for your private endpoints. Using a dedicated subnet helps isolate private endpoints from other traffic in a virtual network.






