
Sergey Nivens - Fotolia
How to protect and manage Azure Pipelines secrets with Key Vault
Follow along with this Azure Key Vault tutorial to securely manage passwords and other sensitive information in an Azure DevOps pipeline.
Software developers and systems engineers use automated pipelines to save time and reduce errors while building a standardized workflow. One popular cloud service for automated build/release pipelines is Microsoft Azure Pipelines.
Security should be a top priority when building automated pipelines in this Azure DevOps service. Developers commonly use sensitive information -- or secrets -- like passwords, API keys and private identifiers during this process. They must obfuscate that information to ensure it isn't seen by the public or unauthorized personnel in their company.
This tutorial will demonstrate how to store secrets encrypted within Azure, and how to then use that information securely. Walk through the steps to set up Azure Key Vault to store sensitive information, rather than use plain text strings in pipelines. Then, learn how to decrypt secrets used within an Azure pipeline.
Prerequisites
To follow along with this tutorial, you must have:
- An Azure subscription.
- An Azure DevOps organization.
- A YAML-based Azure pipeline.
- The Azure CLI installed and authenticated to your Azure subscription. This tutorial uses the Azure CLI, rather than the web UI, to provision resources.
- An Azure resource group to hold the Azure Key Vault.
Once these prerequisites are met, open a PowerShell console, authenticated to Azure with az login.
1. Build an Azure Key Vault
You need a place to store secrets before they can be securely read in an Azure pipeline. Azure Key Vault is an Azure cloud service that enables you to store key/value pairs and small secrets, such as passwords, both encrypted and in plain text, for a wide variety of use cases.
Use the az keyvault create command, as shown below, to create the key vault in a resource group. Specify the location, key vault name and resource group, based on your environment.
az keyvault create --location [YourRegion] --name [YourKeyVaultName] --resource-group [YourResourceGroup]
Once this command completes, the key vault is built and ready to store secrets.
2. Create key vault secrets
Next, use the az keyvault secret set command to create the secrets that you will store in the key vault.
Let's say we have a pipeline that stores a password for a virtual machine. We can call it "VMPassword" and assign it a value of "MySuperSecretPassword!" as shown below:
az keyvault secret set --name VMPassword --value "*MySuperSecretPassword!*" --vault-name [YourKeyVaultName]
3. Enable the pipeline to access the key vault
For security reasons, only a select group can read the value of encrypted secrets in an Azure Key Vault. We must assign permissions to provide that access. Since the Azure Key Vault secret created above will be referenced in an Azure pipeline, give the pipeline access to the key vault.
In the Azure DevOps web UI, open the example Azure pipeline YAML definition. Under Tasks, type "key" and select Azure Key Vault.
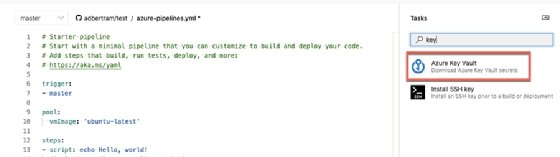
Next, provide your Azure subscription and authorize the pipeline to access the key vault. When it is authorized, select the key vault you'd like to use for this tutorial.
Once created, click Add to add the task into the pipeline. The task created should look like the following:
- task: AzureKeyVault@1
inputs:
azureSubscription: '[Subscription Name]([Subscription ID])'
KeyVaultName: '[YourKeyVaultName]'
SecretsFilter: '*'
4. Use pipeline variables
Once the pipeline has access to the key vault, use a pipeline variable in the form of $([SecretName]) to reference the value stored in any secrets. In this tutorial, we created a secret called VMPassword, so we can reference it anywhere in the pipeline via $(VMPassword), as shown below:
trigger:
- master
pool:
vmImage: 'ubuntu-latest'
steps:
- task: AzureKeyVault@1
inputs:
azureSubscription: '[Subscription Name]([Subscription ID])'
KeyVaultName: '[YourKeyVaultName]'
SecretsFilter: '*'
- script: '$(VMPassword)'
Note that you will not see the value if it's written to the pipeline log. However, the value will be passed to the appropriate task in the pipeline where defined.







