putilov_denis - stock.adobe.com
Explore the key features of Microsoft Defender for Cloud Apps
Monitoring and visibility are crucial when it comes to cloud security. Explore Microsoft Defender for Cloud Apps, and see how this cloud access security broker can mitigate threats.
As businesses increasingly rely on cloud services for their daily operations, it's paramount for them to ensure the security and compliance of these applications.
Enterprises have many cloud security tools at their disposal to manage cloud applications and provide security insights. One such tool is Microsoft Defender for Cloud Apps.
Microsoft Defender for Cloud Apps is a cloud access security broker designed to protect and monitor cloud applications within an organization. It provides organizations the tools to gain visibility into cloud usage, discover unauthorized applications -- often called shadow IT -- and enforce security policies across the entire cloud environment.
Defender for Cloud Apps enables IT teams to take control of their cloud environment. They can ensure the safety and compliance of their data and applications, while maintaining the flexibility and agility that modern businesses demand.
Features of Microsoft Defender for Cloud Apps
A key feature of Microsoft Defender for Cloud Apps is its ability to analyze user behavior and detect anomalies that might indicate potential security threats. It uses advanced machine learning algorithms to identify and alert IT teams about unusual or suspicious activities, helping them take appropriate action before significant damage occurs.
Defender for Cloud Apps integrates seamlessly with other Microsoft security products, such as Azure Active Directory (AD) and Microsoft Purview Information Protection. This integration creates a unified security ecosystem that simplifies management and enhances protection.
Microsoft Defender for Cloud Apps offers many security features to monitor an organization's cloud environment. The following are some main features:
- Visibility and control. Identify shadow IT, and enforce security policies across cloud environments.
- Anomaly detection and threat protection. Analyze user behavior, and alert IT teams to potential threats.
- Microsoft security integration. Seamlessly integrate with Azure AD and Microsoft Purview Information Protection.
- Customizable policies. Tailor prebuilt policies and templates to meet specific security requirements.
- Data protection and compliance. Enforce data loss prevention policies, and ensure regulatory adherence.
How to set up Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps is a security tool designed to help organizations discover and control cloud applications within their environments and mitigate shadow IT risks. To set up Microsoft Defender for Cloud Apps, follow these steps:
- Step 1. First, ensure you have an appropriate license for Microsoft Defender for Cloud Apps. You can purchase it as a standalone service or as part of the Microsoft 365 E5 or Microsoft 365 E5 Security plans.
- Step 2. Log in to the Microsoft 365 admin center with your credentials, expand Admin centers and then click Security. Alternatively, you can browse directly to the Defender portal using the following URL: https://security.microsoft.com.
- Step 3. Scroll down to the section labeled Cloud apps.
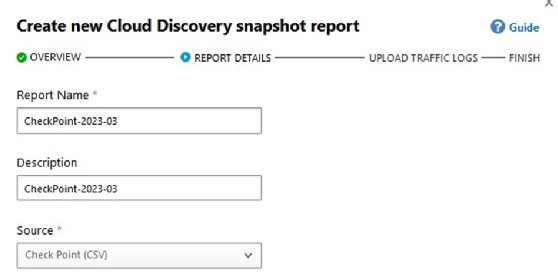
- Step 4. If this is your first time accessing Defender for Cloud Apps, click Actions > Create Cloud Discovery snapshot report.
![Screenshot showing how to create a Cloud Discovery snapshot report]()
Create a Cloud Discovery snapshot report. - Step 5. In the setup wizard, select the firewall device or the generic log formats of the files you want to upload.
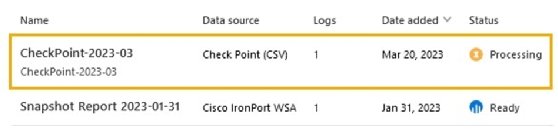
- Step 6. Set the report name and description, followed by the type.
![Screenshot showing Cloud Discovery report name and description]()
Set the report name, description and type. - Step 7. Next, browse for the firewall log to upload, and then complete the wizard. Processing starts once the wizard is complete.
![Screenshot showing Cloud Discovery processing log entries]()
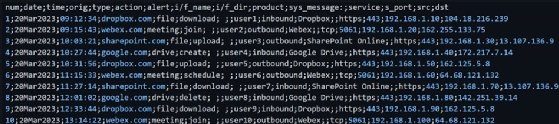
Once the setup is complete, Cloud Discovery begins processing.
The chosen log contains entries with information such as date, time, origin, action and alert, as seen here. It can take up to 24 hours to process the log, depending on the types and amount of log entries that need analysis.
Why use Microsoft Defender for Cloud Apps?
When Defender for Cloud Apps processes a firewall log, it examines the log data to detect security threats or policy violations that might have occurred within the cloud application or service. It analyzes the firewall log for various security events, such as unauthorized access attempts or compliance violations. It also tracks usage patterns to identify suspicious activity that indicates a potential threat.
Defender for Cloud Apps can also consolidate data from multiple sources to provide a comprehensive view of the cloud environment. For instance, it can merge firewall log data with other security events from the cloud application, network and endpoints to identify advanced threats that might have evaded traditional security controls.
By analyzing firewall logs, Defender for Cloud Apps enables security teams to monitor cloud application activity closely and respond swiftly to potential security risks or policy violations.