
Getty Images/iStockphoto
Compare AWS Cloudtrail vs. Config for resource monitoring
When your IT team needs more detailed info about resource activity in AWS, they have options. See how AWS Cloudtrail and Config resource monitoring tools compare.
The ability to successfully and reliably manage a cloud application depends on your ability to view the activity that runs against infrastructure resources.
Amazon Web Services has long provided Amazon CloudWatch to monitor a wide range of system metrics. However, there are many situations that demand a more detailed audit of activities that affect infrastructure components.
Let's compare AWS CloudTrail and AWS Config to see how both monitoring tools stack up against each other.
AWS CloudTrail
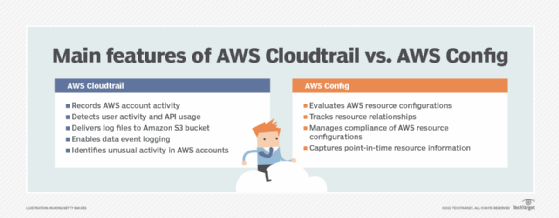
AWS CloudTrail lets IT teams track user activity and API usage. It logs AWS API calls that take place inside an AWS account. It records a history of AWS API events, including who initiated those events -- i.e., IAM Roles or IAM users. The monitoring tool also records the IPs where these requests originate, as well as API parameters and affected resources.
AWS CloudTrail can record activity for most AWS APIs and is essential when investigating disruptive or potentially malicious events. For example, it can help discover who deleted a specific AWS resource or find an entity that initiates activities that incur a high cost.
The Cloudtrail events are placed in Amazon Simple Storage Service (S3). Data analytic tools, such as Amazon Athena and EMR, access files in S3 and analyze the events. The CloudTrail console can also filter and visualize events. AWS Cloudtrail integrates with AWS Lambda, Amazon CloudWatch Logs and Amazon CloudWatch Events.
AWS Config
AWS Config offers a more focused history of events that are based on updates that affect resource configurations. While CloudTrail logs the majority of AWS API activity, AWS Config keeps track of specific updates that are relevant to configurations.
For example, AWS Config can find all RDS DB instances that run a particular DB engine or all Lambda functions with a particular runtime. Since events are also stored in S3, developers can run queries to keep track of configuration update history.
AWS Config introduces the concept of rules which define a set of desired configuration settings. The pre-built rules evaluate provisioning and configuring of AWS resources. For example, they:
- Ensure Lambda functions are deployed inside a VPC.
- Enable backups for RDS DB instances.
- Disable public read for S3 buckets.
From the AWS Config console, application owners can see which resources comply -- or not -- with a particular rule. AWS Config has a feature called Conformance Packs, which are groupings of pre-configured rules that simplify the process of monitoring best practices with a few clicks in the AWS console.
The service integrates with CloudWatch Events, AWS CloudTrail, AWS Systems Manager, Amazon EC2 Dedicated Host, Application Load Balancers and AWS Organizations.
Key takeaway
AWS Config and CloudTrail do overlap. They both monitor services that track and record changes to AWS resources. They also have similar applications, such as operational issue troubleshooting and security analysis.
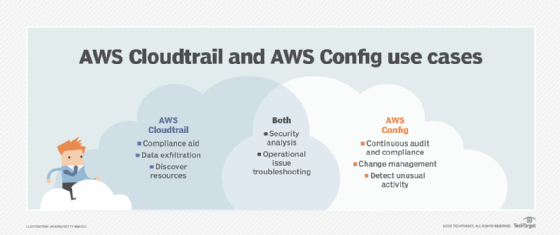
Both services also offer integration with CloudWatch Events, which enables developers to configure actions based on specific events. For example, developers can send a message to an SNS topic, or trigger a Lambda function based on a particular API call or configuration update.
But the tools take a different approach to monitoring. Cloudtrail focuses on who made the specific change, when and from where. Config zeroes in on how the resource has changed. The recommendation is to enable both services, particularly in AWS accounts with applications in a production environment, or those with a high number of resources or team members.





