6 cloud migration challenges to prepare for and overcome
A cloud migration can bring lots of risks, unexpected costs and inconveniences. You can minimize or avoid them with thorough assessment, planning and training.
Cloud migration promises enhanced scalability, improved efficiency and reduced operational costs. However, the journey from on-premises to cloud infrastructure is often more complex than organizations anticipate. Without proper planning and foresight, these transitions can lead to disrupted operations, security vulnerabilities and unexpected expenses.
Research from McKinsey found that up to 38% of cloud migration projects fall behind schedule and 75% go over budget. Understanding common pitfalls before embarking on your cloud journey can help avoid such setbacks and ensure a smoother transition.
Organizations should be prepared to face these six common challenges.
1. Inadequate assessment and planning
One of the worst pitfalls of cloud migration is underestimating the importance of thorough assessment and planning. It can lead to a cascade of issues throughout the migration process and beyond, potentially resulting in failed projects, unexpected costs and disrupted operations.
A comprehensive assessment is the foundation of a successful cloud migration strategy. It involves analyzing current IT infrastructure, applications, data and business processes. Without this crucial step, organizations risk moving forward with incomplete information, which can lead to poor decision-making and resource allocation.
Key assessment components can include the following:
- Infrastructure inventory and dependencies.
- Application portfolio analysis.
- Data assessment and compliance requirements.
- Network architecture evaluation.
- Performance benchmarking.
- Security control mapping.
Common consequences of inadequate assessment include unexpected costs from underestimated total cost of ownership (TCO), performance issues from overlooked dependencies, compliance violations, security vulnerabilities and operational disruptions. Organizations can mitigate these risks by engaging key stakeholders early, using automated discovery tools and conducting pilot migrations before full deployment.
2. Hidden and escalating costs
The pay-as-you-go model of cloud computing can indeed be deceptively complex, and organizations often underestimate TCO when migrating to the cloud. While basic compute and storage costs are generally straightforward, numerous hidden expenses can significantly impact an organization's cloud budget.
Data transfer costs, particularly egress fees, are a prime example of these often-overlooked expenses. Cloud providers typically charge nothing for data ingress but can charge substantial fees for data egress. Some organizations spend up to 27% of their cloud budget on egrees fees, according to Cloudflare, a cloud platform provider. This asymmetry in pricing can lead to significant financial surprises, especially for data-intensive applications or those with high outbound traffic.
Storage costs can also be more complex than they initially appear. While the base cost per gigabyte is usually clear, organizations might not fully account for the different storage tiers that are available -- e.g., hot, cool and archive storage -- and their associated retrieval fees. For instance, retrieving data from archive storage can incur hefty charges, which may not be immediately apparent when choosing a storage option.
Operational costs are another area where expenses can accumulate quickly. This category includes costs for monitoring tools, managed services and other operational support functions. These tools and services, while often necessary for maintaining a reliable cloud infrastructure, can add up to a significant portion of the overall cloud spend.
Training and upskilling staff is yet another hidden cost of cloud migration. As organizations transition to cloud-based systems, they often need to invest in training their IT teams on new technologies and methodologies. This can include formal certification programs, which can be time-consuming and expensive.
3. Security and compliance gaps
The shared responsibility model in cloud computing creates new security and compliance challenges for organizations. While cloud providers secure the underlying infrastructure, organizations remain responsible for critical aspects of security and compliance, including the following:
- Data encryption and access controls.
- Identity and access management.
- Application security.
- Regulatory compliance.
- Network security configuration.
Many organizations struggle to fully understand and implement their cloud security responsibilities. A 2023 Gartner survey found that 63% of organizations have implemented a zero-trust strategy to handle cloud security, highlighting a growing awareness of the challenges.
To address them, organizations should do the following:
- Clearly define security ownership and responsibilities.
- Implement strong access controls and encryption.
- Regularly audit configurations and access.
- Use cloud-native security tools provided by cloud service providers.
- Maintain compliance through ongoing assessments.
These steps align closely with what the Cloud Security Alliance has to say about the shared responsibility model.
Ultimately, successfully implementing the shared responsibility model requires a comprehensive approach combining people, processes and technology. Organizations must invest in training, adopt security best practices and take advantage of cloud-native tools to close security and compliance gaps.
4. Integration and dependencies
Complex application dependencies can derail migration timelines and budgets.
Imagine if your organization is migrating a customer-facing application that seems standalone but actually has hidden dependencies on legacy databases, third-party services and internal tools. Without proper dependency mapping, migration could lead to the following kinds of service disruptions:
- Incomplete data transfers, resulting in missing customer information.
- Authentication failures due to unmapped connections to internal identity services.
- Broken integrations with third-party payment processors or analytics tools.
- Performance degradation from inefficient database queries across cloud and on-premises systems.
- Compliance violations if sensitive data is inadvertently exposed during the migration process.
These issues could result in extended downtime, lost revenue, damaged customer trust and regulatory penalties. To mitigate these risks, it's crucial to follow these key steps for dependency management:
- Create detailed application dependency maps.
- Identify integration points and APIs.
- Test interconnections in a staging environment.
- Plan for temporary hybrid operations.
- Implement strong monitoring.
5. The skills gap
The transition to cloud computing requires new skill sets that many IT teams don't possess. For example, 38.9% of respondents to a recent O'Reilly survey identified cloud security as the most significant skills shortage, highlighting a pressing challenge in the industry.
Organizations can address this gap through three key approaches:
- Structured training programs
- Develop role-specific learning paths.
- Use cloud provider certification programs.
- Implement hands-on labs and workshops.
- Strategic partnerships
- Engage MSPs for specialized expertise.
- Partner with cloud consultants for implementation guidance.
- Use training partners for skill development.
- Knowledge management
- Create comprehensive documentation.
- Establish internal best practices.
- Implement collaboration tools.
Start with a skills assessment to identify specific gaps in your team's cloud knowledge. This helps create targeted training programs rather than taking a one-size-fits-all approach.
6. Vendor lock-in
Vendor lock-in is a significant risk in cloud computing when organizations become overly dependent on a single provider's proprietary services, making it difficult and costly to switch providers. This dependency often develops gradually as companies adopt more platform-specific managed services, databases and automation tools.
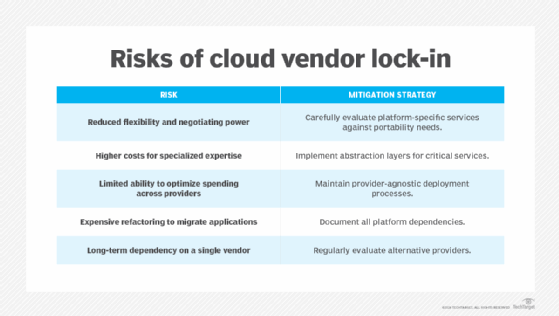
This chart lists some of the risks organizations can incur from only using a single vendor, along with potential mitigation strategies.
Breaking free requires a methodical approach, starting with auditing cloud service use to identify areas of greatest dependency. While basic services, like compute, have low lock-in risk, more advanced services, such as serverless architectures, pose especially high risk. Making informed architectural choices early and balancing immediate benefits against long-term flexibility are crucial for avoiding problematic lock-in.
Adam Bertram is a 20-year veteran of IT and an experienced online business professional. He's an entrepreneur, IT influencer, Microsoft MVP, blogger, trainer and content marketing writer for multiple technology companies.








