10 cloud vulnerabilities that can cripple your environment
Enterprises can be devastated by security-related weaknesses or flaws in their cloud environments. Find out where you are most vulnerable before an attacker comes knocking.
Businesses make a big mistake when they assume the cloud will automatically keep their workloads and data safe from attack, theft and other malfeasance. Even in the cloud, vulnerabilities and the potential for mistakes and exploitation are inevitable.
Cloud platforms are multi-tenant environments that share infrastructure and resources across countless global customers. A provider must work diligently to maintain the integrity of its shared infrastructure. At the same time, the cloud is a self-service platform, and each customer must carefully define the specific environment for each of its workloads and resources.
Before delving into these cloud security challenges and how to protect against them, enterprises must understand the differences among the three major types of dangers: threats, vulnerabilities and risks. These terms are often used interchangeably, but they carry different meanings for IT security professionals:
- A threat is something that is definitively happening -- an action or behavior -- that the organization must defend against, such as a DoS attack, human error or natural disaster.
- A vulnerability is an oversight, gap, weakness or other flaw in the organization's security posture. This could include an improperly configured firewall, an unpatched OS or unencrypted data.
- A risk is a potential threat against the organization's vulnerabilities. For example, someone stores unencrypted data in the public cloud, and human error could enable the data to be accessed or changed. This could be perceived as a significant risk for the business that must be addressed.
When users understand public cloud vulnerabilities, they can then identify potential security gaps and common mistakes. An IT team needs to recognize and address each type to prevent its system from being exploited. Below are 10 of the most common areas of focus.
1. Misconfigurations
Users are responsible for composing the various resources and services that host a cloud workload. Each element involves unique configurations, so your IT team needs to prioritize mastery of the various settings and options. Cloud resources are guarded by an array of configuration settings that detail which users can access applications and data. Configuration errors and oversights can expose data and enable misuse or alteration of that data.
Every cloud provider uses different configuration options and parameters. Cloud architects and engineers are typically experts in proper configurations, but the onus is on users to learn and understand how the platforms that host their workloads apply these settings.
IT teams can mitigate configuration mistakes in the following ways:
- Adopt and enforce policies of least privilege or zero trust to block access to all cloud resources and services unless such access is required for specific business or application tasks.
- Employ cloud service policies to ensure resources are private by default.
- Create and use clear business policies and guidelines that outline the required configuration settings for cloud resources and services.
- Be a student of the cloud provider's configuration and security settings. Consider provider-specific courses and certifications, and pay close attention to any new settings or options a provider offers.
- Use encryption as a default to guard data at rest and in flight where possible.
- Use tools, such as Intruder and Open Raven, to check configuration errors and audit logs.
2. Poor access control
Unauthorized users take advantage of poor access control to get around weak or absent authentication or authorization methods, such as identity and access management.
For example, malicious actors take advantage of weak passwords to guess credentials. Strong access controls implement additional requirements, such as minimum password length, mixing upper and lower cases, the inclusion of punctuation or symbols, and frequent password changes.
Access control security can be enhanced through the following common tactics:
- Enforce strong passwords, and require regular resets.
- Use multifactor authentication techniques.
- Require regular reauthentication for users -- do not remember credentials for prolonged periods.
- Adopt policies of least privilege or zero trust.
- Avoid the use of third-party access controls, and employ cloud-based access controls for services and resources within the cloud.
3. Shadow IT
Anyone can create a public cloud account, which they can then use to provision services and migrate workloads and data. It's precisely this flexibility that helped bring cloud computing to the forefront of enterprise IT. But those not well versed in security standards often mismanage data and misconfigure the security options -- leaving exploitable cloud vulnerabilities. In many cases, such shadow IT deployments might never even recognize or report exploits. This denies the business any opportunity to mitigate the problem until long after the damage is done.
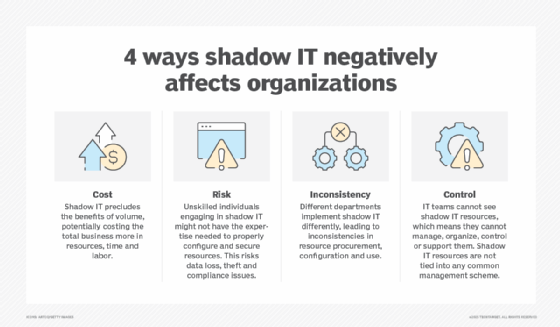
Today's businesses are more tolerant of shadow IT, but it's vital that organizations implement standard configurations and practices. Business users, departments and other organizational entities must adhere to the business's set standards and regulatory obligations to combat vulnerabilities and keep the overall organization safe.
4. Insecure APIs
Unrelated software products use APIs to communicate and interoperate without any knowledge of the internal workings of each other's code. APIs usually require -- and grant access to -- sensitive business data. Many APIs are made public to help speed adoption, enabling outside developers and business partners to access the organization's services and data.
But APIs are sometimes implemented without adequate authentication and authorization. That is, the API does not support such features. Or the API does support such features, but users don't bother to invoke them. Those APIs can wind up completely open to the public, so anyone with an internet connection can access -- and potentially compromise -- data. Consequently, insecure APIs or those with weak security and other defects are rapidly becoming a major attack vector for hackers and other malicious actors.
Whether using a cloud provider's APIs or creating business APIs deployed in the cloud, it's important to develop and use APIs with the following:
- Strong authentication.
- Data encryption.
- Activity monitoring and logging.
- Access controls.
Businesses that develop and implement APIs should treat the APIs as sensitive code and subject to thorough security reviews, including penetration testing. Cloud and other outside APIs should be subject to the same scrutiny. Avoid outside APIs that don't meet established security guidelines.
5. Violations
In cloud computing, the provider is responsible for the security of the cloud, while the customer is responsible for security in the cloud.
In this shared responsibility model, the provider maintains the integrity and operations of the infrastructure and controls the separation of customer resources and data. The customer is responsible for configuring application and data security, such as access controls.
When a threat successfully exploits a vulnerability and accesses data without a proper business purpose, the business is solely responsible for that breach and any subsequent consequences. Consider the following common examples:
- Sensitive customer data is stolen, which puts the business in violation of prevailing regulatory obligations and damages its reputation.
- Important data is stolen, which causes a loss of intellectual property, compromises the organization's competitive position and jeopardizes the investment that yielded that data.
- Internal business data is altered or erased, which creates a raft of potential impacts, such as production problems.
Breaches usually carry penalties for the business. For example, breaches that violate regulatory obligations might result in significant fines and penalties. Breaches that involve data stored for clients or customers might result in contractual violations that lead to time-consuming litigation and costly remedy.
Ensure proper configurations, and follow other precautions outlined in this piece to mitigate any regulatory or legal exposures.
6. Outages
Cloud infrastructures are vast and often global in scope, but failures do occur, usually resulting in highly publicized cloud outages. Such outages are caused by hardware problems, outside provider issues and configuration oversights -- precisely the same issues that plague traditional local data centers.
A cloud can also be attacked through DDoS and other malicious mechanisms intended to impair the availability of cloud resources and services. If an attacker can render any public cloud resources or services unavailable, it impacts every business or cloud user that employs those resources and services. Cloud providers are adept at handling attacks, and cloud support teams can help when specific business workloads are attacked.
While businesses and other public cloud users can't prevent cloud outages and attacks, consider the effect of such disruptions on cloud workloads and data sources, and plan for such events as part of your disaster recovery (DR) strategy.
Given the vast nature of public clouds, DR for mission-critical business workloads can usually be addressed through high availability architectures implemented across cloud regions or zones. Still, such postures aren't implemented automatically, and you must design them carefully and test regularly to ensure the business is as unaffected as possible when outages occur.
7. Inadequate data management
Modern businesses rely on ever-growing volumes of sensitive data, but business data is governed by an equally expanding array of heavy regulations, such as GDPR, that affect data sovereignty, data protection, data security and data privacy. Simply moving data from a local data center to a global cloud provider doesn't alleviate a business or business leaders from data management responsibilities, such as data lifecycle management, including proper data destruction. Oversights in data management can leave a business vulnerable to significant fines and other legal penalties.
Cloud adoption must include careful consideration of data management issues that are relevant to the business. Cloud data storage must meet the same stringent rules that govern local data storage. Cloud data management can be addressed through the following important points:
- Sensitive or important business data in the cloud should be encrypted at rest and in flight to guard against theft, and access logs should track all access and changes that affect data.
- Data stored in the cloud must be inventoried to ensure that all data is classified, accounted for and subject to appropriate data management practices for each data type.
- Data should be governed by mature lifecycle practices that manage data from creation through archiving and eventual destruction.
- When data must be destroyed at the end of its retention lifecycle, the business should consider using tools capable of secure data destruction; just deleting data isn't an adequate destruction practice.
8. Lack of process or standardization
Everything starts with a plan, and this is also true for cloud adoption. A typical business often approaches cloud use with different people doing similar things differently. The lack of transparency into what each business element is doing, why and how frequently leads to oversights and disconnects. These can result in other cloud problems, such as misconfigurations, poor access control, regulatory violations and other issues that can do more harm than good for the business.
There's certainly nothing wrong with tinkering with new technology or testing creative new approaches to solving business problems. But the road from innovation to implementation can be long and bumpy with lots of twists and turns. Business and technology leaders should seek to review and unify cloud practices and guidelines before using a cloud for live production workloads. The idea is to learn from mistakes and get everyone doing similar things in similar ways to develop faster, more predictable and more successful business outcomes.
Standardizing on best practices and processes can be a challenging issue that demands collaboration and leadership. It takes time, and the results are constantly evolving. The business needs technology leaders with cloud expertise, business leaders with solid regulatory and business governance skills, finance professionals with a keen knowledge of cloud costing, and workload stakeholders willing to share ideas and cooperate to meet business needs. This is the foundation of cloud FinOps practices.
9. Lack of monitoring
You can't manage what you can't see. It's an old axiom that applies perfectly to today's IT and cloud environments. Monitoring tools can help to ward off an array of potential vulnerabilities and expose undesirable usage patterns. For example, cloud monitoring can do the following:
- Inventory data to ensure all data assets are classified and protected throughout their lifecycle.
- Watch cloud usage to check for unneeded resources and services, known as cloud sprawl.
- Safeguard configurations and prevent unauthorized configuration changes.
- Measure application performance and user experience.
- Log access and activity to maintain proper security measures.
There are countless monitoring tools available to meet the unique needs of almost any enterprise. Third-party tools can easily be installed in the cloud or delivered as remote SaaS versions and used to oversee cloud activity. Major third-party monitoring tools can readily be found from various online and vendor searches. The list below presents a cross-section of available tools and is not intended to be exhaustive. Major offerings include the following:
- AppDynamics.
- BMC TrueSight Operations Management.
- Datadog.
- DX Unified Infrastructure Management.
- Dynatrace.
- Grafana.
- LogicMonitor.
- Nagios.
- Netdata.
- New Relic.
- PagerDuty.
- Sematext Cloud.
- SharePoint monitoring.
- SolarWinds Observability.
- Sumo Logic.
- Zabbix.
- Zoho Corp. ManageEngine Log360 Cloud.
Cloud providers also offer a wide range of native monitoring and management tools that are tailored for the specific provider, such as the following:
- Amazon CloudWatch.
- Azure Monitor.
- Google Cloud Monitoring.
- Google Cloud operations (formerly Stackdriver).
10. Imperfect technology ecosystem
While most vulnerability discussions focus on the cloud provider and cloud user, the role of a broader technology ecosystem can't be overlooked. Every business, including cloud providers and users, depends on an array of other providers, vendors and sources for everyday operations. Consider the following examples of the greater technology ecosystem:
- IT hardware vendors must provide secure and reliable equipment. Defects in BIOS and even the machine code of processor command sets can introduce vulnerabilities.
- Software developers must develop and test secure code that is reasonably free of defects. But developers can only test for the expected, and many defects are only exposed in actual production.
- Open source software can play a role in software development and software security. Bringing in third-party code opens all manner of vulnerabilities that can result in security or performance issues.
- SaaS providers must deliver services that are reliable and secure. But those providers must develop and manage code and IT infrastructure that can be subject to the same problems found in the relationship between a cloud provider and a cloud user.
- The broader internet depends on ISPs and regional carriers, each of which has its own configuration, security and performance concerns.
- Tools can age poorly as threats and operational demands evolve. The tools must evolve as well or potentially leave new threats unchecked.
Many of these and other technology ecosystem issues are far beyond the direct control of cloud providers and cloud users.
Editor's note: This article was updated to include additional cloud vulnerability categories, update products and reflect product name changes.
Stephen J. Bigelow, senior technology editor at TechTarget, has more than 20 years of technical writing experience in the PC and technology industry.








