
Maksim Samasiuk - Fotolia
Container security tools pump up the platform
Startups are developing technologies that fill in some of the security gaps, including better controls for container orchestration.
The decades-old approach to software development called software containers is often explained with analogies. Just how complex is containerization? And what does it mean for security models?
"Virtual machines are like herds of cattle. Containers are more like locusts. They are dense, little, going everywhere, and controlling them becomes much harder," said Loris Degioanni, the CTO and co-founder of Sysdig Inc., a San Francisco-based container security tools provider that came out of stealth mode in 2015.
Moving to microservices
The shift from centralized software deployments toward distributed environments, often running in the cloud, is transforming data centers and application architectures as more companies create services made up of business functions and other components known as microservices. Why is this happening now?
"Enterprises want to adopt continuous integration and continuous development that is based on splitting applications into services and microservices," Degioanni said. "And that requires essentially using different building blocks to write these applications, and those building blocks tend to be containers."
Developers first started to move to Agile environments to improve speed and scalability in the cloud. Containerized applications, which package libraries and dependencies, offer portability with fewer constraints from operating environments. Interest in containers -- and container security tools -- is high; adoption is low.
According to Gartner, less than 20% of global organizations run containerized applications in production environments. That number is expected to increase rapidly over the next two years, however, reaching 50% by 2020.
While the shift toward microservices architectures is new, containers are not. The concept originated with Linux container technology, which enabled users to run isolated instances of Linux on a single host.
"If you look at a modern Linux operating system, everything is in containers already," said Dan Walsh, a consulting engineer who heads the Red Hat container team, during a presentation in 2017 for a Weave Online User Group. The security modifications in the Linux kernel for Security-Enhanced Linux can provide even better process isolation. Based on constructs from the National Security Agency, SELinux provides mandatory access control that the Department of Defense requires. (Walsh is the author of "The Container Coloring Book," which uses a three little pigs analogy to explain container security.)
A container is essentially a process -- a lightweight, executable package of software -- running on Unix, Linux and, more recently, Windows systems. Based on isolation created by the Linux kernel namespaces, it cannot see other containers or processes running on the host. Linux kernel control groups are used to isolate and limit resource allocation, such as memory, to maintain system performance. When you run applications in containers, you end up managing applications rather than operating systems, according to Walsh.
Docker simplified aspects of the Linux container when dotCloud released it as an open source project in 2013. Since then, the company has continued to build container security tools, such as secrets management, into Docker. The Docker Enterprise Edition is a container security platform that offers security, governance and automation, according to the company. Orchestration, which involves container placement and scheduling at the network level, is managed by Docker Swarm, Kubernetes, Apache Mesos and other frameworks. Docker added support for Windows environments in 2016.
As companies move to containerized environments, supporting Docker and other formats, visibility from image creation to runtime execution is critical for security teams. Computer security company Lacework reported in June that it found more than 21,000 publicly facing container orchestration systems in the cloud, and 300 lacked administrative access controls.
Startups are developing technologies that fill in some of the security gaps, including controls for container orchestration. In May, Google announced partnerships with Aqua Security, Capsule8, StackRox, Sysdig Secure and Twistlock to offer native integration in its Cloud Security Command Center for the Google Kubernetes Engine.
Innovation from startups
For companies like Google that need to solve the runtime security problem now, the container security tools offered from a number of startups may provide answers. Several container security startups have developed platforms to monitor and secure the container lifecycle across on-premises and multi-cloud environments.
In March, Aqua Security Software Ltd. released version 3.0 of its Container Security Platform with Kubernetes-native enterprise controls. The company -- based in Ramat Gan, Israel, and Burlington, Mass., and formerly known as Scalock -- came out of stealth mode in 2016 with a platform aimed at Fortune 500 customers that require visibility, monitoring and auditing (compliance) of containers from the development phase to runtime in Linux and Windows environments. Version 2.0 of the Aqua platform added secrets management and more granular network segmentation.
"We do provide some assessment to the infrastructure, making sure that wherever you are running your container has good security processes," said Amir Jerbi, Aqua Security's CTO and co-founder. Jerbi holds numerous patents and served as chief architect of CA Technologies' security group.
Aqua's main focus, however, is the application layer, ensuring that the application the company is running in the container will be secured whether it's running on premises or in the cloud. The beauty of containers is that they are flexible, he said. "The container will run the same way regardless of the platform or the infrastructure that you are using. So when you are building your security solution, you need to make sure it will be as flexible and as agile as containers, allowing you to secure the container regardless of the decisions you would make -- regardless of the cloud decision and the orchestrator decision."
The Aqua platform provides security for the container lifecycle, including the build process by developers, shipping to a file system to store the container (registry) and taking it from the registry and running it in the data center or the cloud. While DevOps incorporates the technology into its pipeline for the build and ship stages, IT security focuses on the runtime. "If we identify any abnormal activity, we will block the container and alert the security group," Jerbi said.
The platform uses automation and machine learning to understand container behavior and create profiles. The impact on build and runtime performance is minimal at 2% to 3%, Jerbi said, because containers are small and their behavior is predictable.
However, like other shadow IT, CISOs may not always be aware of the extent of container use within their organizations. Security officers need to find out what is going on and then map the security gaps, according to Jerbi, who said that often those holes involve development and runtime security.
Another startup in the container tools space, StackRox, updated its Container Security Platform in July by extending policy management to the orchestration layer and adding a "continuous feedback loop" for developers and security teams to help them improve security posture.
Founded in 2014 in Mountain View, Calif., StackRox released the first version of its container security platform, which focused on runtime security, at Black Hat 2017. Version 2.0, released at the RSA conference in April, extended the technology to the container lifecycle so that it now covers the build and deployment process as well as runtime security. The company also uses containers and microservices in its platform. "One of our biggest differentiators is that we can provide more global policies," said Ali Golshan, co-founder and CEO of StackRox, "because we are not just providing a point solution at each part of the process; we are putting together all of the data sets."
Part of the company's strategy is to use instrumentation in the infrastructure without preconceived ideas about what it will detect.
The main types of events the company sees center on the application or the orchestrator itself, according to Golshan. The reason: Cloud-native folks are building a lot more hygiene into their build, reducing privileges, so the attack surface is very small. The other types of events that StackRox is seeing are at the orchestration level because the tool is complex. "There is a lot of exposed API, making sure to expand your attack surface," he said.
Sysdig is an open source project, co-founded by Degioanni. He also founded CACE Technologies, the company behind Wireshark, in 2005. Sysdig is a container intelligence platform with two products, Sysdig Monitor and Sysdig Secure. The technology uses a single agent per host (instance of the Linux operating system) to monitor and provide forensics for container environments. The Windows version of the container security tools is in the alpha stage. Version 2.0 of Sysdig Secure, released at DockerCon in June, incorporates vulnerability scanning earlier in the development cycle. The security module supports Docker, Kubernetes, Red Hat OpenShift and Amazon Elastic Compute Services.
Competition from traditional vendors
In addition to startups, traditional players are eyeing the container security tools space. Some will acquire container security technologies -- Tenable was early to the market when it acquired FlawCheck in 2016 -- and others will introduce their own tools.
Cloud security provider Qualys released its Container Security platform at DockerCon in June. In addition to vulnerability scanning, the new platform provides inventory, change management tracking and policy compliance checks, among other functionality.
Red Hat added 100 new container customers to its OpenShift container platform in the first quarter of this year. The company's stock plummeted, however, based on a projected slowdown in traditional middleware, according to Red Hat CEO Jim Whitehurst.
Cloud platforms are like Windows versus Unix in the '90s, when it was very important to tune apps to the platform; Java came to the market officially as a way to abstract the way developers were running their code, and then Unix became less important. "Containers and microservices are a bit like the Java of cloud," Degioanni said.
Red Hat is among the companies working to advance standards from groups such as the Open Container Initiative, established by Docker and others, as well as the Cloud Native Computing Foundation.
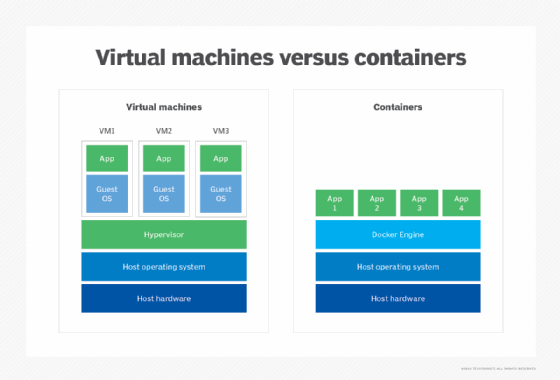
Perhaps the biggest question for many CISOs is how containers match up to virtual machines.
"Do not treat containers like VMs," Sysdig's Degioanni said. "Do not treat a locust as a cow."






