container registry
What is a container registry?
A container registry is a collection of repositories made to store container images. A container image is a file comprised of multiple layers which can execute applications in a single instance. During the application development process, developers should have access to all the container images needed for an application. Hosting all the images in one stored location allows users to commit, identify and pull images when needed.
A user can act as a host for a container image by placing an image into a container registry for others to use. If an organization is hosting a native cloud application, then utilizing a container registry may be a good idea.
Repository vs. registry
The terms repository and registry may be easily confused when talking about containers. A container repository is used to store related images for setup and deployment. Container repositories can be used to manage, pull or push images.
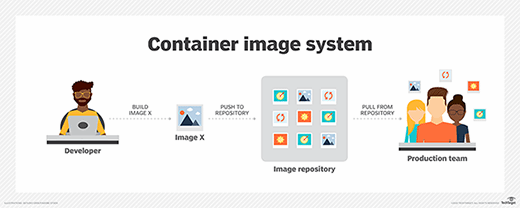
Container registries store multiple repositories of container images, as well as storing API paths and access control rules. Container registries also have to option of being hosted publicly or privately.
Public vs. private registries
Public container registries are generally the faster and easier route when initiating a container registry. They are ideal for smaller teams that can take more advantage from incorporating standard and open sourced images from public registries. Public registries are also seen to be easier to use; however, they may also be less secure than private registries.
A private container registry is set up by the organization using it. Private registries are either hosted or on premises and popular with larger organization or enterprises that are more set on using a container registry. Having complete control over the registry in development allows an organization more freedom in how they choose to manage it. This is why private registries are seen to be the more secure -- an organization can apply as many security measures as they feel needed.
Container security
Public containers are seen as less secure because individual container images may contain malicious or outdated code which, if goes unpatched, could lead to a data breach. It may also be unknown who has read or write access to an image.
If an organization's priority is security when it comes to container registries, then they should implement a private registry. Other security approaches to container registries include:
- Assigning role-based access control (RBAC).
- Scanning for vulnerabilities in images.
- Digitally signing images to ensure each image is trusted.
- Using authentication methods such as access tokens or JSON key files, similar to how Google's container registry works.
- Using Identity and Access Manager (IAM) settings, like how IBM's Cloud Container Registry does.
Vendors
Organizations can create and deploy their own container option or use cloud services.Popular options from the three cloud giants include Google Cloud's Container Registry (GCR), Azure Container Registry (ACR) and Amazon's Elastic Container Registry (ECR). Third-party options include Docker Hub, GitHub Container Registry, JFrog Container Registry and Red Hat Quay.






