
Andrea Danti - Fotolia
Compare Azure Firewall vs. NSGs for network security
Traffic to and from resources needs proper security to protect data, but the wrong tool could leave you vulnerable. Explore these two services to find the right level of protection.
When enterprises run workloads on a cloud service, they need to monitor and manage both inbound and outbound network traffic for security purposes.
Microsoft Azure provides two security options to control inbound and outbound traffic:
- Azure Firewall
- Network Security Groups (NSGs)
Both services provide security, but at different network levels. Below, learn what each service is and its main features, as well as how the two compare.
What is Azure Firewall?
Azure Firewall is a managed, cloud network security service. This stateful firewall service deploys on any virtual network and protects Azure Virtual Network (VNet) resources by filtering both network and application-level traffic. Also, it enables admins to create traffic filtering rules, which they can enforce across multiple subscriptions and networks.
Azure Firewall has built-in high availability and admins can configure it to span multiple Availability Zones for a 99.99% uptime. Also, with unrestricted cloud scalability, it can scale based on changing flows of inbound and outbound traffic.
Other top Azure Firewall features include:
- application fully qualified domain name (FQDN) filtering rules;
- FQDN tags;
- service tags;
- threat intelligence;
- outbound source network address translation (SNAT) support;
- inbound destination network address translation (DNAT) support;
- multiple public IP addresses;
- Azure Monitor logging;
- forced tunnelling;
- web categories (in preview); and
- certifications.
What is Network Security Group?
An NSG is Microsoft's service to simplify virtual network security; it enforces and controls network traffic. NSGs are associated with subnets and network interfaces of an Azure VM.
NSGs contain security rules and provide a way to activate a rule or access a control list. With these rules, IT teams can organize, filter and route different types of network traffic. These rules, which filter inbound and outbound traffic, deny or allow traffic based on 5-tuple information:
- source
- source port
- destination
- destination port
- protocol
A comparison of Azure Firewall and NSGs
When comparing Azure Firewall vs. NSGs, look at what Open Systems Interconnection (OSI) layer each service has. This information helps IT teams understand how data is sent or received over a network. It begins at Layer 1, which is the physical layer then goes up to 7, which is the application layer. Azure Firewall is an OSI L4 and L7, while NSG is L3 and L4.
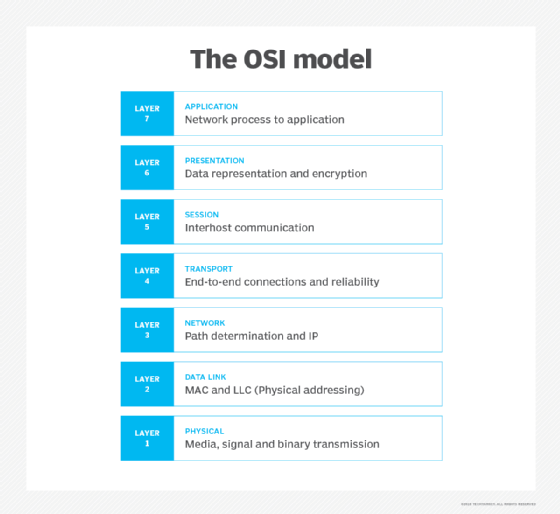
While Azure Firewall is a comprehensive and robust service with several features to regulate traffic, NSGs act as more of a basic firewall that filters traffic at the network layer. Azure Firewall is adept at analyzing and filtering L3, L4 and L7 traffic. Azure Firewall also provides support for threat-intelligence-based filtering, which NSG can't do.
Both options use service tags to define network access controls. Service tags are groups of IP addresses for particular services, and they protect Azure resources, as well as achieve network isolation. Unlike NSGs, Azure Firewall also supports application FQDN tags, which are used together with application rules to allow the required outbound traffic through the firewall.
In real world cases, enterprises typically use Azure Firewall when they need to filter traffic to a VNet with its threat intelligence-based filtering capabilities. NSGs are typically used to protect traffic flowing in and out of a subnet.
These two network security services can work together to provide defense-in-depth network security in which multiple defensive measures are put in place. That way, if one element fails, another security measure stands in its place.








