IT process automation: 6 examples to boost efficiency
A variety of software offerings, increasingly infused with AI, can help an IT shop become more productive, from handling service requests to conducting user satisfaction surveys.
Process automation is a broad software category with specific uses within IT departments and the wider enterprise.
Different facets of the technology automate repetitive tasks, workflows and more complex processes. Product categories within the process automation umbrella include robotic process automation (RPA), business process automation and digital process automation (DPA). Other products include workflow automation software and low-code/no-code tools.
For IT shops, process automation use cases generally fall into two categories: IT automation and IT process automation. Traditionally, IT automation focuses on discrete, repetitive tasks such as server and storage provisioning. IT process automation typically targets multistep functions such as service management and incident response. The lines between the two areas are blurring, however, as vendors expand product offerings and add new features. For example, AI is adding autonomous decision-making capabilities to the process automation mix.
The technology landscape might be complicated, but the goal for IT managers is straightforward: Improve their operational efficiency and extend those productivity benefits to in-house customers.
Process efficiency wins
There are several examples of how process automation can boost efficiency.
1. User support
Service management, a core user support function, involves a variety of tasks, such as handling user requests, creating and managing support tickets, and guiding change management. Automation eases repetitive tasks along that spectrum of services while also speeding up time to resolution. Options here include IT service management (ITSM) software, RPA offerings and low-code/no-code platforms.
Meanwhile, advances in AI have boosted the efficiency of another aspect of user support: self-service. Automation is now replacing a larger portion of tier 1 support, which fields user questions on anything from broken laptops to potential security issues.
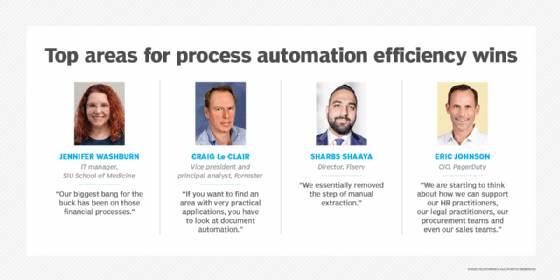
"All of these operational questions that used to be, 'Put in a ticket, it will go to someone and they'll get back to you,' are starting to become things where human intervention is almost not required," said Eric Johnson, CIO at digital operations management software provider PagerDuty.
Earlier generations of self-service technology, he noted, resulted in a 25% to 50% deflection rate -- that is, the percentage of inquiries resolved without reaching a service desk staffer. But generative AI (GenAI)-infused technology is pushing deflection rates to between 75% and 80%, he said.
The ability to harness large language models, natural language processing and virtual agents has increased the sophistication of self-service offerings. "It opens up all kinds of new opportunities for how we support people," Johnson explained. "It's not just IT support. We are starting to think about how we can support our HR practitioners, our legal practitioners, our procurement teams and even our sales teams."
2. Document automation
Document automation, a subset of process automation, provides an important efficiency boost that touches on multiple functions within an organization. This technology extracts data from forms and other source material and loads it into document templates or business systems. "If you want to find an area with very practical applications, you have to look at document automation," said Craig Le Clair, vice president and principal analyst at Forrester and author of Random Acts of Automation, published in January.
Applications and use cases include customer onboarding, content analytics, and finance and accounting, he added. In finance and accounting, for instance, document processing uses machine learning to extract data from the appropriate fields and hand that data to a task-performing RPA bot, which then loads that data into an ERP system. IT use cases include technical documentation and reporting.
Document automation has been around for a while, but the recent addition of generative AI is bolstering the technology, LeClair said. "What's changed is the ability to get more data and expand the number of documents you can do extraction for -- with help from GenAI," he explained.
Financial services technology firm Fiserv is combining AI with UiPath's RPA software to extract service-level agreements (SLAs) and associated data from vendors' contracts. That task has traditionally been manual, with a team of people pouring through dozens of pages of contracts to find the required data.
Sharbs Shaaya, director of enterprise AI-powered automation at Fiserv, said the company is experimenting with AI agents that go into contracts to extract data such as performance metrics and the fees vendors agree to pay for failing to meet them. The data is transferred to an RPA bot, which continues the execution of the SLA validation process. "We essentially removed the step of manual extraction," Shaaya said.
3. Employee onboarding
The onboarding use case is critical for IT departments, which spend considerable time setting up accounts and readying devices for new employees. Automating such user provisioning tasks can bolster efficiency. Options here include RPA and DPA products, as well as the process automation aspects of IT asset management systems and identity and access management offerings.
However, IT can look beyond user provisioning to automate other departments' onboarding needs. At Southern Illinois University (SIU)'s School of Medicine, the process automation team built an automated process that lets the school's employee health office gather onboarding documentation even before a new hire walks through the door, said Jennifer Washburn, an IT manager at the school who heads the team, which uses Laserfiche's process automation software. "When the start date comes, they are ready, and there are no delays in onboarding," Washburn said, noting the office's early jump on collecting documents.
4. Finance and HR
The SIU's medical school includes a medical practice, so its back-office processes include credentialing healthcare providers, funding positions and managing promotions. Historically, those processes were conducted on paper, Washburn said. Actions such as processing promotions and funding them involved filling out PDFs online, printing them out and mailing them to the school. Once received, the forms would make the rounds, via courier, from office to office for the necessary signoffs. The process took weeks -- and, sometimes, months.
Process automation, however, allows for electronic routing and a faster turnaround time. "Our biggest bang for the buck has been on those financial processes," Washburn said.
5. Security
The rising volume of cyberattacks demands higher efficiency when dealing with them. Automating incident management accelerates response time.
PagerDuty, for example, uses its own incident management product when a security information and event management system or a user report uncovers a potential threat, Johnson explained. This automation use case quickly identifies a problem, gets the appropriate people working on it and resolves the issue in a postmortem as rapidly as possible.
The result is an improvement in operational efficiency metrics such as mean time to acknowledge and mean time to resolution, John said, adding, "Those types of metrics are important because the longer a problem is sitting out there, not addressed, the risk just grows."
6. User feedback
IT departments provide internal customer support in many ways, whether it's dealing with technical issues, updating software or streamlining business processes through automation. Many IT managers conduct user satisfaction surveys to measure the effectiveness of those efforts. Automating the survey process can save time and boost consistency.
Washburn said the SIU medical school's automation team uses an automated process review to survey "process owners" -- internal customers who requested the process and are stakeholders in its adoption. Automation creates a regular routine in which Washburn's staff can gauge process owners' satisfaction, gather ROI measures and evaluate opportunities for continued process improvement.
What to expect down the road
IT managers can expect to see AI make further inroads into all forms of process automation. Agentic AI, in particular, could automate complex, multistep business processes as the technology evolves. Such technologies will increasingly interact with other automation categories, as AI and tools such as RPA converge into hyperautomation.
Over time, AI might provide an orchestration layer that coordinates the work of automation offerings such as RPA and DPA. But for now, these more conventional technologies will largely fill that role. GenAI, for instance, is expected to orchestrate less than 1% of core business processes in 2025, according to Le Clair.








