IAM compliance: Know the system controls at your disposal
IAM is critical to an organization's data security posture, and its role in regulatory compliance is just as crucial.
Identity and access management is the backbone of enterprise data security. A strong IAM framework that manages identities and which systems, applications and data those identities can access is vital to keeping sensitive data safe.
Because of its importance, many industry and government regulations and laws address IAM and require the use of various IAM controls.
Note, however, that adopting an IAM framework and using IAM technologies isn't a recipe for meeting compliance mandates. Rather, demonstrating that the framework and technologies indeed provide a more secure environment is the secret to compliance success.
What is IAM and why is it important for regulatory compliance?
IAM is a framework of business processes, policies and technologies that helps manage the different types of digital identities that access an organization's systems and resources across on-premises and cloud environments. Identity types include user identities, such as employees, customers and partners; device identities, such as smartphones, laptops and IoT devices; and machine identities, such as applications, workloads and services.
IAM enables organizations to control who or what can access corporate systems and data. An IAM framework involves assigning identities, authenticating identities, authorizing identities and managing identities. These key IAM practices help fortify an organization's security posture by averting unauthorized access to data and preventing data breaches and data loss.
IAM plays an important role in compliance. Many data privacy and protection laws and regulations, including GDPR, HIPAA and PCI DSS, have stringent requirements to ensure organizations control which identities are allowed to access sensitive information.
With an effective IAM framework in place, organizations not only help ensure the confidentiality, integrity, availability, security and privacy of data, but also help prove they meet IAM compliance mandates during an audit.
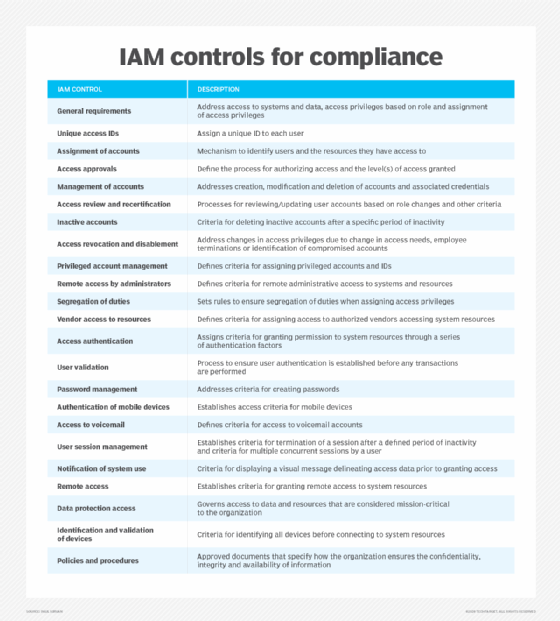
How do IAM systems support compliance?
The first step toward achieving and maintaining IAM compliance is understanding which processes, controls and tools are relevant to an organization's goals and regulatory requirements.
Following is a sampling of IAM controls included in IAM standards and regulations to varying degrees:
- Access controls. These regulate what an identity can view or use in an organization. Types of access controls include role-based access control (RBAC), group-based access control (GBAC) and attribute-based access control (ABAC). Access controls also include physical access to buildings, etc.
- Authentication. This process determines whether an identity is who or what it says it is. Types of authentication include passwords, MFA and biometrics.
- Authorization. This is the process of granting access permissions that enable an identity to perform certain actions after it has been authenticated. Like access controls, types of authorization include RBAC, GBAC and ABAC.
- Provisioning. The process of setting up an identity's account involves assigning a unique ID to a user, organization, application or device, defining the ID's roles and attributes, setting up the ID's level of access rights, establishing the ID in systems and assigning the ID credentials.
- User access reviews. Performed on a regular basis, these reviews ensure identities maintain only the access required to do their jobs while removing access that is no longer required -- for example, if an employee changed roles within the organization.
- Deprovisioning. It is the process of removing an identity from an organization's systems and revoking any access rights -- for example, after an employee quits or has been terminated.
Most IAM tools -- web-based, portal-based, APIs or via a cloud service -- provide these controls. Other IAM features that could tie into compliance include the following:
- Remote access. This involves an identity's ability to access systems and applications from any location. Organizations should create a remote access security policy that outlines remote access best practices and tools.
- Password management. This includes policies and best practices to maintain password hygiene. It often includes avoiding password reuse, requiring MFA, mandating secure password storage and using password managers.
- MFA. It is an IAM technology that requires an identity to provide two or more methods to authenticate itself. These might include username-password, biometrics or security tokens.
- Single sign-on. SSO is an authentication technology that permits an identity to access multiple applications and systems with a single set of credentials. Using SSO, a user does not need to sign into each application, which helps simplify UX and prevent user friction.
IAM compliance standards, regulations and resources
Multiple industry organizations and governments have established standards, regulations and other criteria for ensuring public and private sector entities provide IAM programs.
Ongoing proactive management of IAM controls and related activities, supplemented by periodic audits and reviews, can confirm an organization meets compliance requirements. Following are regulations many organizations are subject to, as well as their corresponding IAM requirements:
- COBIT. Originally developed by ISACA, COBIT is an IT management and IT governance framework for organizations of any size or industry. Not a mandatory legal requirement, COBIT offers guidance to help organizations improve IT management best practices. IAM controls recommended by COBIT include using the principle of least privilege (POLP) and privileged access management (PAM), and maintaining an audit trail of the identities that access sensitive data.
- Family Educational Rights and Privacy Act. FERPA is a U.S. law that regulates secure access to educational information and records. FERPA has several requirements for the disclosure of student data, including the use of PINs, passwords and other factors that an authorized user has or possesses.
- U.S. Federal Financial Institutions Examination Council. FFIEC provides compliance standards for financial institutions. It has both an information security workbook and audit guidelines that address IAM requirements. Guidance on identity management from FFIEC include using MFA, implementing POLP and discussing IAM risks during cybersecurity awareness trainings.
- GDPR. This European standard addresses a broad range of data security and protection requirements to ensure the privacy of user data. IAM controls mandated by GDPR include using POLP, segregation of duties and strong authentication with MFA.
- Gramm-Leach-Bliley Act. GLBA is a federal law that requires financial institutions to have controls that protect the confidentiality of customer data. GLBA IAM controls include monitoring and logging user activity, following POLP and maintaining separation of duties.
- HIPAA. This U.S. federal healthcare law's Security Rule and Privacy Rule define controls that address the security and privacy of protected health information (PHI). IAM controls needed to achieve HIPAA compliance include assigning unique user IDs, verifying any identity accessing PHI and authenticating PHI data to ensure it has not been altered or destroyed in an unauthorized manner.
- NIST. NIST Special Publication 800-63-3 "Digital Identity Guidelines" and its three companion standards -- SP 800-63A "Enrollment and Identity Proofing," SP 800-63B "Authentication and Lifecycle Management" and SP 800-63C "Federation and Assertations" -- address IAM requirements for federal agencies. NIST SP 800-53 "Security and Privacy Controls for Information Systems and Organizations" covers information security requirements for federal information systems and organizations. Identity governance controls outlined by NIST include the use of federated identity systems, using biometrics as part of MFA and ensuring separation of duties.
- North American Electric Reliability Corporation. NERC provides standards and controls for protecting information as used by electric power utilities. Its Critical Infrastructure Protection (CIP) plan in particular regulates the cybersecurity of the Bulk Electric System in North America. The NERC CIP includes IAM guidance around the entities responsible for managing systems and the controls required for electronic and physical access to systems.
- PCI DSS. This is a global security standard that addresses the security of credit and debit card transactions and protects cardholder data. IAM controls required by PCI DSS include not using default system passwords, restricting cardholder data access based on POLP, using PAM and not using shared or group identities, i.e., each user must have a unique ID.
- Sarbanes-Oxley Act. SOX is a federal law that mandates auditing and financial regulations for public companies. Section 404 specifies controls for preparing financial reports and ensuring the integrity of report data. IAM controls mandated by SOX include physical and electronic access controls to prevent unauthorized access to sensitive data. These include setting passwords, maintaining separation of duties and monitoring user and account activity.
ISACA and Internal Organizations for Standardization (ISO) provide extensive resources on IAM. For example, in addition to COBIT, ISACA also provides a variety of audit and compliance documents organizations can refer to when examining IAM controls prior to a compliance audit. The ISO 27000 series of standards, which addresses IAM requirements, is widely used as an audit benchmark. NIST guidance, though directed toward federal agencies, is also a useful starting point for organizations to implement IAM controls.
Sharon Shea is executive editor of Informa TechTarget's SearchSecurity site.








