What is risk mitigation?
Risk mitigation is a strategy that helps businesses prepare for disasters and other issues and decrease the effects of threats they face. Like risk reduction, risk mitigation reduces the negative effects of threats and disasters on business continuity (BC).
Threats that might put a business at risk include cyberattacks, weather events and other causes of physical or virtual damage. Risk mitigation is one element of risk management, and its implementation differs from one organization to another.
Why is risk mitigation important?
The principle of risk mitigation acknowledges that some risks can't be eliminated, and organizations must prepare for potential risks. A proper risk mitigation plan will weigh the potential effect of each risk and prioritize planning around its possible impact.
Risk mitigation focuses on the inevitability of some risks. For example, hurricanes, tornadoes and other natural disasters can't be avoided. Risk mitigation is used for those situations where a threat can't be eliminated entirely. Rather than planning to avoid a risk, mitigation deals with the aftermath of a disaster and the steps that can be taken prior to the event occurring to reduce adverse and potentially long-term effects.
Ideally, an organization would be prepared for all risks and threats and avoid them entirely. However, a risk mitigation plan helps it prepare for the worst. This approach acknowledges that some degree of damage will occur, and it's necessary to have systems in place to deal with that.
What's in a risk mitigation plan?
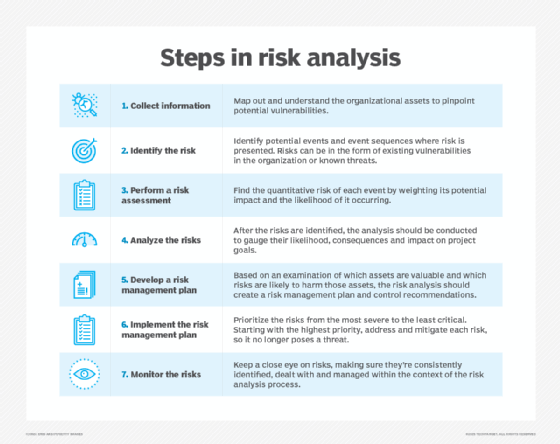
Most organizations will follow a few standard steps when creating a risk management plan. Recognizing recurring risks, prioritizing risk mitigation and monitoring the established plan are vital aspects to maintaining a thorough risk mitigation strategy.
There are five basic steps in the design process of a risk mitigation plan:
- Identify all possible events that pose risk. A risk mitigation strategy takes into account all the priorities and protection needs of an organization's mission-critical data and other assets. It considers any risks that might arise due to geographic location. A risk mitigation strategy must also factor in an organization's employees and their needs.
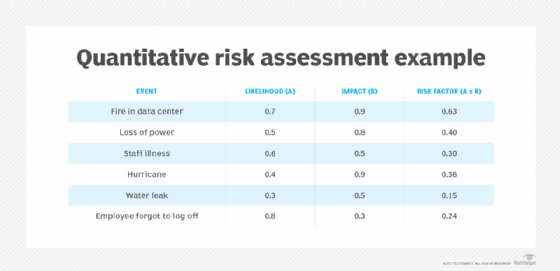
- Perform a risk assessment. This involves quantifying the level of risk in the events identified. Various measures, processes and controls are identified to reduce the impact of risk.
- Prioritize risks. This step involves ranking the risks in terms of severity. Risk mitigation prioritization can involve accepting more risk in one part of the organization to better protect another. By establishing an acceptable level of risk for different areas, an organization can better prepare the resources needed for BC, while putting fewer mission-critical business functions on the back burner.
- Track risks. This step involves monitoring risks as they change in severity or relevance to the organization. It's important to have strong metrics for tracking risks as they evolve and for tracking the plan's ability to meet compliance requirements.
- Implement and monitor progress. This involves reevaluating the plan's effectiveness in identifying risk and improving mitigation as needed. In BC planning, testing a plan is vital; risk mitigation is no different. Once a plan is in place, regular testing and analysis should occur to make sure the plan is up to date and functioning well. Risks facing data centers are constantly evolving, so risk mitigation plans should reflect any changes in risks and shifting priorities.
Types of risk mitigation strategies
There are several types of risk mitigation strategies. They are often used in combination, and one might be preferable over another depending on the company's risk landscape. These strategies are all part of the broader practice of risk management:
- Risk avoidance. This strategy is used when the consequences are deemed too high to justify the cost of mitigating the problem. For example, an organization can choose not to undertake certain business activities or practices to avoid any exposure to the threat they might pose. Risk avoidance is a common business strategy and can range from something simple, such as limiting investments, to something as severe as not building offices in potential war zones.
- Risk acceptance. In this type of strategy, organizations accept a risk for a given period of time to prioritize mitigation efforts on other risks.
- Risk transfer. This approach allocates risks between different parties, aligning with their capacity to protect against or mitigate the risk. For example, a company might risk having a defective product because it's built with some amount of third-party material. The company might then transfer responsibility for a certain fraction of the risk because of this.
- Risk monitoring. This is the act of watching projects for changes in the impact of the associated risks.
Risk can affect any combination of performance, cost and scheduling. Therefore, different strategies should be used to address risks based on the way they affect these factors. For example, it might be more important for a company to perform well than for it to save money in a certain project scenario. The company would likely employ a risk acceptance strategy, temporarily prioritizing risks that affect performance more heavily than cost.
Risk mitigation best practices
Below are risk mitigation best practices that information security professionals should follow:
- Make sure stakeholders are involved at each step. Stakeholders can be employees, managers, unions, shareholders or clients. All perspectives are important for developing a comprehensive, holistic risk mitigation strategy.
- Create a strong culture around risk management. This means communicating the values, attitudes and beliefs surrounding risk and compliance from the top down. While it's important for every employee to have risk awareness, the probability of a strong culture is greatly improved when management sets the tone.
- Communicate risks as they arise. Risk awareness must be strong throughout the entire organization, so facilitating communication of new, high-impact risks is important to keep everyone up to speed.
- Ensure the risk management policy is clear. Roles and responsibilities should be clearly defined, and each defined risk needs a clear mitigation process that employees will be able to follow.
- Continuously monitor possible risks. Risk monitoring practices should be clearly determined and implemented to continuously improve the risk mitigation plan.
Risk mitigation tools
One commonly used risk mitigation tool is a risk assessment framework. An RAF provides an organization with an outline of which systems are at high or low risk and presents information for both technical and nontechnical personnel. It can present consistent risk assessment and reporting methods.
Common RAFs include the following:
- Risk Management Guide for Information Technology Systems from the National Institute of Standards and Technology.
- Operationally Critical Threat, Asset and Vulnerability Evaluation from Carnegie Mellon University.
- Control Objectives for Information and Related Technology, commonly known as COBIT, from the Information Systems Audit and Control Association.
- The Mitre website, which offers comprehensive guidelines for risk mitigation.
Other commonly used risk mitigation tools include the following:
- A probability and impact matrix.
- A strengths, weaknesses, opportunities and threats analysis -- commonly called a SWOT analysis.
- A root cause analysis.
Organizations often bring in external specialists who have an understanding of internal needs and resources and can be a beneficial part of a risk mitigation plan. Several BC and disaster recovery (DR) vendors focus on risk mitigation, and even smaller organizations can take advantage of DR as a service to keep costs low.
Learn more about implementing the key steps in an effective risk management process.
Ben Lutkevich is site editor for Informa TechTarget's SearchSoftwareQuality. Previously, he wrote definitions and features for WhatIs.






