
rvlsoft - Fotolia
Understanding AWS security groups' capabilities and limitations
Expand your knowledge of AWS security groups. Learn how to configure them for traffic protection, along with how they compare to other firewall options on AWS.
AWS users must stay on top of network security. Firewalls offer an important security measure in the AWS cloud, and some virtual firewalls are easy to set up and organize.
AWS security groups are virtual firewalls at the instance level. Cloud admins can configure, attach and delete them in simple steps, outlined below. But, to get the best network traffic protection, first learn what security groups are and how they differ from other firewall choices within AWS deployments. And pick up these security group best practices.
Understanding AWS security groups
The security group firewall can protect EC2 and Amazon Relational Database Service instances. Security groups establish rules that govern inbound and outbound traffic. These rules define the IP address, port and protocol for traffic allowed through.
If a type of traffic is not explicitly allowed, the security group denies it. As a default, all outbound traffic is allowed, but the AWS user must define rules for inbound traffic. Security groups are also stateful, so if an instance sends a package out to a specific IP/port, you can still receive the response even if there is no rule that explicitly allows that traffic back in.
Users can attach security groups to instances at launch or even later in the life of an instance. Each instance can have up to five different security groups, and admins can attach each security group to multiple instances. This flexibility enables logical grouping between resources. For example, to allow Secure Socket Shell access via a VPN on a specific set of instances, attach an appropriate security group to each instance that needs SSH access, rather than opening up access on each separate instance.
A default security group is created automatically upon launch of a Virtual Private Cloud (VPC). AWS attaches the default security group to newly launched instances in that VPC, unless you specify a different security group.
Security groups vs. network ACLs
There's one more AWS firewall option we should mention. Network access control lists (ACLs) are an important piece of the firewall strategy within AWS' shared responsibility security model but are sometimes confused with security groups.
Network ACLs operate on a subnet level, below security groups, which operate at the instance level. The layers are key to understanding AWS security groups' efficacy: Incoming traffic reaches the network ACL first, as the network traffic flows toward the instance, when it encounters the instance's security group or groups.
Another difference is that network ACLs have no default rules. This means the AWS admin must define each rule explicitly. If there is a specific allow or deny rule, it will be enforced. Network ACLs are also stateless, so it's up to the user to track both incoming and outgoing rules. A network ACL will enforce a specific allow or deny rule to the letter of the law.
Out of the box, network ACLs allow all traffic, until the admin configures explicit rules. This open traffic setup makes the security group at the instance level, with its default restrictions, the more important line of defense within AWS' firewall options.
How to set up security groups on AWS
We'll set up this security group example via AWS Management Console. You can find the Security Groups tab under the EC2 dashboard or under VPC.
Open the Security Groups tab, and click on Create Security Group.

Here, name the security group. It's a best practice to create a detailed description for the security settings, especially if you work in a team where others might use the same group.
Security groups belong to VPCs. So, choose the desired one, and start adding inbound rules.
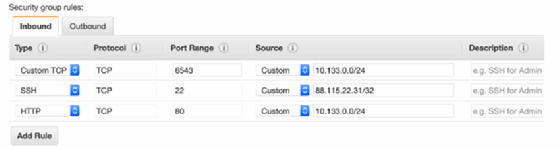
As mentioned previously, outbound rules that enable unlimited access are already set on each security group. You can, however, remove this configuration and create your own.
You can also create security groups using the AWS command-line interface, an AWS SDK or even with infrastructure-as-code tools, such as AWS CloudFormation or HashiCorp Terraform. However, the GUI console is a good way to get started with these firewall options.
To remove a security group, highlight it, and click Action > Delete. If the security group is attached to a running instance, AWS will throw up an error message, as seen below.

It is fairly easy to add the necessary rules and have the traffic flow to an instance, but follow security best practices: Only allow what is needed, and never open instances to public access, unless specifically required.






