
alphaspirit - Fotolia
Quick steps to enable AWS multifactor authentication
AWS secures the underlying infrastructure, but organizations are responsible for locking down account access and integrity. Here are a few simple ways to establish MFA on AWS.
IT organizations on the road to AWS can leave access doors wide open behind them.
While comprehensive cloud security costs money and involves complex procedures, multifactor authentication (MFA) is one simple way to protect AWS workloads without much -- or any -- additional spending.
AWS Multi-Factor Authentication requires users to provide unique identification to log in to their AWS cloud environment, in addition to their regular sign-in credentials. This little extra step makes a huge difference to AWS security. If unauthorized people somehow get ahold of login credentials, they still need this additional authentication to access the account. MFA can stop attacks before they even begin.
Supported AWS Multi-Factor Authentication setups
AWS MFA mechanisms can be virtual or physical.
A virtual device is the most commonly used approach to AWS Multi-Factor Authentication. This is a software app run on a mobile device that generates a six-digit numeric code. It relies on a time-synchronized, one-time password algorithm, and each user's MFA access information is unique. AWS also supports a hardware version of the MFA device.
Real-life consequences of lax security
Cyberattacks come in various shapes and sizes, from minor nuisances to devastating disasters that can even put a company out of business.
In 2014, code hosting and project management services provider Code Spaces was put out of business after an attacker got access to its AWS console. In an attempt to extort money, the attacker deleted all of the company's S3 buckets, snapshots of Elastic Block Store volumes and Amazon Machine Images. Code Spaces couldn't recover after losing almost all of its customers' data. The company reported that it actually had a decent degree of redundancy in place for expected losses during normal operations but was vulnerable to someone with high-level privileges and account access.
This incident should be a lesson to any company employee with AWS credentials -- especially admin-level permissions. It could have been avoided with AWS multifactor authentication features enabled.
AWS users can alternatively opt for a Universal 2nd Factor (U2F) security key rather than a code. The U2F security key is a physical device that plugs into a USB port. It works via an open authentication standard hosted by the FIDO Alliance, an open industry association targeting security beyond passwords.
Editor's note: AWS has an SMS MFA device in preview that will feature low setup costs.
Enable MFA for AWS users
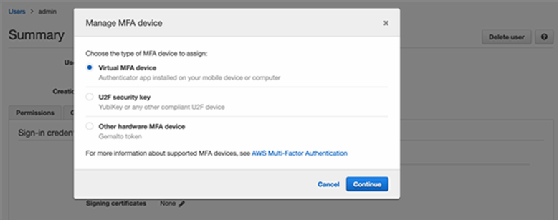
To enable AWS MFA via one of these options, log in to AWS Management Console, and go to the Identity and Access Management controls. Choose a user, and go to her Security credentials tab. Next to Assigned MFA device, click Manage. Select the MFA type you want to use, and then follow the correct procedure:
- For virtual MFA devices, scan a QR code, and type two consecutive MFA codes to enable it.
- To access hardware MFA, input the serial number of the device, followed by the two consecutive MFA codes AWS shows you.
- A U2F security device must be inserted into your USB port to activate the key, but then it's as simple as tapping the button.
When it comes to security, a little extra effort goes a long way. It's fairly simple to implement MFA on AWS, and it can significantly increase the overall access security of your cloud workloads and stored data. Even as AWS handles the underlying infrastructure safety, AWS security comes down to awareness within each organization's IT team.








