
rvlsoft - Fotolia
Set AWS security automation in motion with these practices
Enterprises need to continuously improve their cloud security posture. Catch up on the latest expert advice on AWS security tools and practices.
One way to deter breaches of AWS deployments is to make sure no one employee or team is responsible for securing it. That doesn't mean you should leave cloud protection up to fate. Instead, set up AWS security automation.
Enterprises entrust too much data to the public cloud to manage security manually. For IaaS, where AWS holds nearly half the total market share, organizations spent $32.441 billion in 2018, up more than 30% year-over-year, according to Gartner. AWS and other cloud providers assure users that their data centers and servers are secure, but also expect customers to share the responsibility in terms of application design and management, as well as data protection.
Cloud security automation comes in many forms and users can enforce it with a wide range of tools, both native to AWS and from independent software vendors. Review expert advice on how to use automation tools such as AWS CloudFormation to reduce vulnerabilities through deployment consistency and rapid application patches and updates. And learn about threat detection and response tools, such as AWS Security Hub and Splunk Phantom.
However, AWS security automation is more than the right tools. Developers and administrators must also adopt practices such as DevSecOps and continuous security improvement.
Build security into cloud ops
Any cloud admin can automate aspects of deployment management, according to information security consultant Dave Shackleford. Configuration control shrinks the attack surface of instances and containers, whether through AWS OpsWorks or a third-party tool. Configuration management can be a gateway to infrastructure as code, with templates for application deployments that a company's security experts can vet. Shackleford also recommends AWS users utilize CloudTrail to take advantage of the relative ease of metadata tagging in the cloud.
"Once assets are tagged, any number of automated or semi-automated security strategies can be pursued," he said. For example, the cloud admin can set tags to collect evidence for threat investigation or use tags as groups to update network access policies en masse, rather than manually tweaking each asset. Read his advice on these and other cloud-native management tools for security automation.
If you take AWS security automation a step deeper into the application lifecycle, you'll hit DevSecOps, which emphasizes security from development through deployment and support. DevSecOps embeds security and compliance policies into the CI/CD pipeline where code gets built and spun up on AWS instances. But this takes a lot more than opting in to AWS security defaults and services, such as Identity and Access Management, and Security Hub, according to Rich Mogull, VP of products at DisruptOps, a security platform for multi-cloud infrastructure. Learn how to implement security-minded DevOps, or DevSecOps, from AWS leadership and expert users in this report from AWS re:Inforce, the cloud provider's security conference.
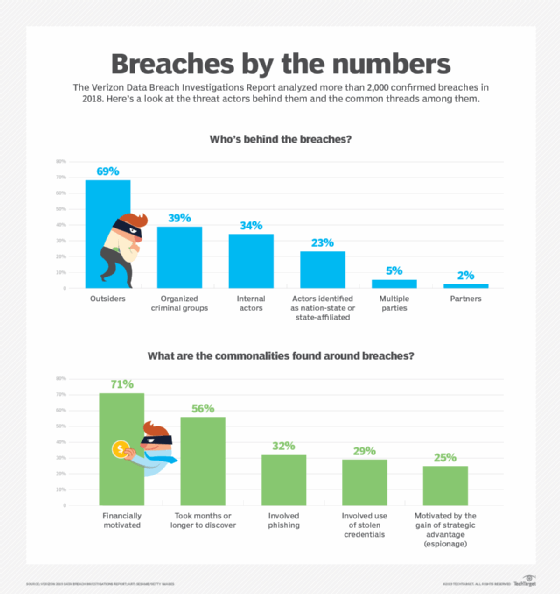
Businesses appear to have improved their data security practices after record-high breaches in 2017.
In 2018, the number of publicly disclosed data breaches in the business sector fell to 571, a sharp drop from 907 in 2017. Across all industry verticals, data breaches decreased from 1,632 to 1,244 over the same timeframe. Although the business sector has more breaches than education, banking, government and other sectors, it also exposes the fewest records per breach of all sectors tracked by the Identity Theft Resource Center.
Breaches are most likely to be perpetrated by outsiders, and more than half of the breaches in 2018 took at least months to discover, according to the Data Breach Investigations report from Verizon.
SOAR into the cloud
Security automation is a core part of a SOAR software stack. SOAR -- security orchestration, automation and response -- is a software stack that promises to disable low-level security threats before the IT team has to take action. A fully realized SOAR setup remediates vulnerabilities in the deployment stage, underpins rapid incident response and automates security policy enforcement. SOAR implies more holistic data synthesis and autonomous response than security information and event management (SIEM).
Enterprises that run critical workloads on AWS should investigate how SOAR changes SIEM tools, and ensure users feed the correct operations data into security management tools for timely, automated and precise incident support. Security architect Matthew Pascucci outlines the effect of SOAR, and provides detailed examples to help refine security automation.
AWS also offers native security data analysis. AWS Security Hub aggregates security alerts and automates compliance checks across Amazon cloud accounts and services. It's also designed to prioritize alerts, so admins can quickly address pressing security concerns, explains technology editor Stephen Bigelow. Get an overview of Security Hub and how it works with native and third-party data sources to evaluate it for SOAR.
Bring on the specialists
While security automation is a way to remove human error from cloud deployments, automation is no replacement for skill. A team member who is deeply knowledgeable about secure networks, data protection and disaster recovery prevents automation from making matters worse. Veteran IT journalist Alan Earls investigates the common security missteps in enterprise AWS deployments, with insights on essential cloud security skills that prevent them.
Automation tools also require a human touch for maintenance and updates. Ensure security specialists approach automation with a continuous improvement mindset, never one of "set and forget," said Mike O. Villegas, who is active in the ISACA IT security professionals association and VP of a security consulting firm for the payment industry. "With the proliferation of new attack vectors introduced daily, it is foolish to believe that the security automation tool does not need further attention," he said. Get Villegas' advice on how to keep security automation tools up-to-date and what common areas they should cover.








