AWS Key Management Service (AWS KMS)
What is AWS Key Management Service (AWS KMS)?
AWS Key Management Service (KMS) is a managed service provided by Amazon Web Services (AWS) that allows companies to create, control and manage the cryptographic keys that encrypt and protect their data. With AWS KMS, organizations get a world-class key storage, management and auditing system that makes it easy to control the encryption of data stored across their AWS services.
As the name suggests, AWS KMS is an encryption and key management service scaled for use in the AWS cloud. Organizations can use the encryption keys and functionality provided by AWS KMS to protect data in all their applications that use AWS. The service can also generate data keys that can be used outside of AWS KMS. Symmetric and asymmetric KMS keys can be generated for encryption and signing using AWS KMS.
AWS KMS allows organizations to better control who can use their AWS KMS keys and who can access their encrypted data. The service allows them to use its key management and cryptographic features directly in their AWS applications or through AWS services integrated with AWS KMS.
AWS KMS uses hardware security modules (HSM) to protect and validate all its cryptographic keys under the FIPS 140-2 Cryptographic Module Validation Program (CMVP). The CMVP is a joint effort between the National Institute of Standards and Technology (NIST) and the Canadian Centre for Cyber Security to promote the use of validated cryptographic modules and provide Federal agencies with a standardized way to procure equipment containing validated cryptographic modules.
AWS KMS includes an application programming interface (API) to create and manage KMS keys and special features including custom key stores, as well as use the KMS keys in cryptographic operations. All AWS KMS API calls must be signed and transmitted using the Transport Layer Security (TLS) protocol. AWS recommends using the AWS SDKs (available for .NET, C++, Go, Java and other languages) to make programmatic API calls to AWS KMS.
What is a key in AWS KMS?
An AWS KMS key is a logical representation of a cryptographic key. It is a primary resource in AWS KMS. To use or manage KMS keys, it's mandatory to use AWS KMS. The following three types of KMS keys can be created in AWS KMS:
- Customer managed key. Created by the organization.
- AWS managed key. Created by AWS services that use KMS keys to encrypt the organization's service resources.
- AWS owned key. KMS keys created by AWS services in a service account.
A KMS key contains the following:
- metadata (key ID, key spec, key usage, creation date, description and key state); and
- reference to the key material used when cryptographic operations are performed with the KMS key.
A KMS key can be created with the cryptographic key material generated in AWS KMS FIPS validated HSMs. KMS keys can be used for multiple cryptographic operations, such as the following:
- data encryption, decryption and re-encryption;
- message signing and verification;
- generating exportable symmetric data keys and asymmetric data key pairs;
- generating and verifying HMAC codes; and
- generating random numbers suitable for cryptographic applications.
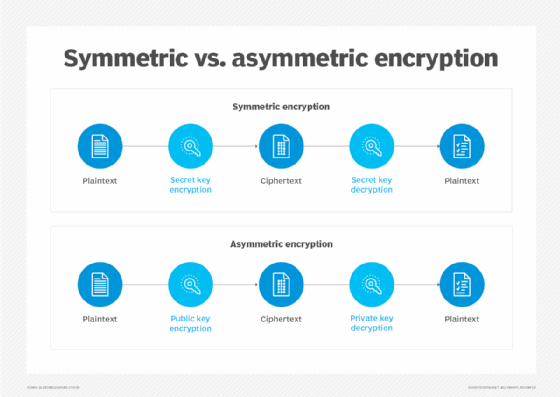
Symmetric, asymmetric and HMAC encryption keys in AWS KMS
A symmetric encryption KMS key is the most used type of KMS key. It never leaves AWS KMS unencrypted and is created by default when a user creates an AWS KMS key. The same key is used for encryption and decryption. It represents a 256-bit AES-GCM encryption key (except in China AWS Regions, where it represents a 128-bit SM4 encryption key).
AWS allows users to import their own key material into symmetric encryption AWS KMS keys and also create these keys in custom key stores. A symmetric encryption AWS KMS key is a good choice for most tasks, unless the task explicitly requires asymmetric encryption. In addition to encrypting, decrypting and re-encrypting data, a symmetric encryption KMS key can be used to generate data keys and data key pairs.
Data keys are a type of symmetric encryption key that can be used to encrypt large amounts of data and other data encryption keys. Unlike symmetric KMS keys, data keys are returned to the user and can be used outside AWS KMS.
An asymmetric encryption KMS key represents a mathematically related public key and private key pair. The private key never leaves AWS KMS unencrypted and to use it, the user must call AWS KMS. The public key can be used within AWS KMS by calling the AWS KMS API operations. It can also be downloaded and used outside AWS KMS. Asymmetric KMS keys are most useful for public key encryption, signing and verification. Data key pairs, which are asymmetric data keys, can be used in client-side encryption/decryption and for signing and verification outside AWS KMS.
Hash-based message authentication code (HMAC) KMS keys can also be created and used to generate and verify HMAC tags. It represents a variable length symmetric key that can be used to generate and verify HMAC. Users have the flexibility to create multi-region HMAC KMS keys, which function as copies of the same KMS key in different AWS Regions (data can be encrypted in one AWS Region and decrypted in a different Region).
Key material in AWS KMS
AWS KMS creates the key material for a KMS key by default. The key material for symmetric KMS keys and the private keys of asymmetric KMS key never leaves AWS KMS unencrypted. Organizations and their users cannot delete this key material. Instead, they must delete the KMS key. They also cannot extract, export, view or manage the key material. The only exception is the public key of an asymmetric key pair, which users can export for use outside of AWS.
What organizations can do is import their own key material into a KMS key. They can also use a custom key store to create KMS keys that use key material in their own AWS CloudHSM cluster.
Creation and management of AWS KMS keys
With AWS KMS, organizations can create, edit, view, enable, disable and delete symmetric and asymmetric KMS keys, including HMAC keys. They can also create, delete, list and update aliases (friendly names) for KMS keys to simplify their use and control access.
In addition, AWS KMS allows users to use key policies, identity and access management (IAM) policies, grants and tags to control access to KMS keys. Tags are also useful for identifying, automating and tracking the cost of AWS KMS keys. AWS KMS supports attribute-based access control (ABAC) to control access to customer managed keys based on associated tags and aliases, as well as condition keys to refine policies and automatic rotation of the cryptographic material in a KMS key.
Envelope encryption in AWS KMS
KMS uses envelope encryption, which has two different keys for protecting data and encryption keys. The practice involves encrypting plaintext data with a data key, and then encrypting the data key under another key. The top-level plaintext key encryption key, which is required to decrypt the keys and data, is known as the root key or AWS KMS key. All encryption keys are stored and managed securely in AWS KMS. Root keys never leave the AWS KMS FIPS validated HSM unencrypted.
Envelope encryption protects data keys so users can safely store the encrypted data key alongside their encrypted data. It also allows them to re-encrypt only the data keys that protect the raw data, so they don't have to re-encrypt raw data multiple times with different keys. In addition, envelope encryption combines the strengths of symmetric key algorithms that are faster and produce small ciphertexts and public key algorithms that simplify key management and provide inherent role separation.
AWS KMS integrations
AWS KMS integrates with almost all AWS services that encrypt enterprise data. All AWS services integrated with AWS KMS use only symmetric encryption KMS keys to encrypt data. They do not support encryption with asymmetric KMS keys. When organizations integrate one or more AWS service with AWS KMS, they can use the AWS KMS keys in their account to protect the data that the service receives, stores or manages.
AWS KMS integrates with AWS CloudTrail to log an enterprise's use of its KMS keys for auditing, regulatory and compliance purposes. CloudTrail delivers log files to the organization's designated Amazon S3 bucket which can be used to audit key usage. Some other possible integrations with AWS KMS include the following:
- Amazon DynamoDB
- Amazon EBS
- Amazon EMR
- Amazon RedShift
- Amazon RDS
- Amazon S3
- WorkSpaces
Compliance validation for AWS KMS
third-party auditors assess the security and compliance of AWS KMS. As of 2022, AWS KMS has been validated and certified by compliance standards, including the following:
- SOC 1 report
- SOC 2 report
- SOC 2 report for confidentiality
- PCI DSS Attestation of Compliance (AOC) and Responsibility Summary
- FedRAMP-High
- ISO27001:2013, 27017:2015, 27018:2014
- Cloud Computing Compliance Controls Catalog (C5)
See 12 AWS security tools to protect your environment and accounts.






