
carloscastilla - Fotolia
Comparing containers and VMs for multi-tenant apps
Secure containers is a big concern when comparing virtual machines and containers for multi-tenant apps. Learn what each has to offer and which works best for your organization.
Multi-tenancy is the idea of a single instance of an application being used by multiple users, or tenants. In the era of virtualization, this was made possible by running multiple virtual machines on a single server with each VM being isolated from its neighbors. This was leveraged by software-as-a-service apps like Salesforce, or infrastructure-as-a-service providers like Amazon Web Services, who would use multi-tenancy to share the resources of a single hardware server between multiple customers. This wasn't without its flaws -- AWS was called out for its many "noisy neighbor" issues. Under heavy load, one instance's performance would affect other instances on the same server. But by and large, VMs were a reliable option for multi-tenant apps.
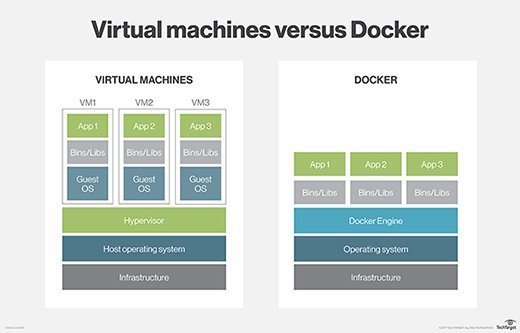
In today's rush to containerize apps, Multi-tenancy has taken center stage in the comparison between VMs and their more agile counterparts -- Docker containers. The chart below shows an architecture image of both these technologies.
The primary difference between VMs and containers is that VMs include a hypervisor and a guest OS layer. Containers, on the other hand, avoid this and instead use a Docker engine combined with the host OS, which makes for a much lighter package and lots of agility. However, this comes at a cost. While VMs are isolated at the hypervisor level, containers use namespaces and cgroups, making their isolation "softer."
Because containers share the same host OS, if one container is compromised, it's very likely that neighboring containers would be affected as well.
This being the case, let's look at the efforts being made to secure containers.
CaaS -- containers in VMs
Containers as a service (CaaS) offerings like AWS Elastic Cloud Compute Container Service, Azure Container Service and Google Container Engine take a dual approach. They run containers inside VMs, which gives them some of the advantages of containers with the security of VMs.
Another advantage to this approach is that containers benefit from the mature management tools available in these cloud platforms. Essentially, you use the same tools you'd use to manage your cloud-based VMs for your containers as well. This includes mature identity and access management tools like AWS IAM, monitoring tools like AWS CloudWatch and workflow automation tools like AWS CodePipeline and AWS CodeDeploy. This goes a long way to secure containers. However, you still pay the hypervisor tax, and in that sense, this option still falls short of the promise of containers for multi-tenant apps.
Startups -- innovation from the outside
There are a number of startups that see multi-tenant apps as an opportunity and are innovating to better isolate containers.
Twistlock is a security tool that scans container images on developer machines or registries like Docker Hub to detect vulnerabilities. It uses the industry standard CIS Docker benchmark report to check for 80+ possible vulnerabilities. Integrating with continuous integration tools like Jenkins, it's able to seamlessly fit into your automated CI/continuous deployment pipeline.
Aqua Security is another security platform that secures containers in runtime. It scans container images and locks down container activity so that compromised containers don't affect neighboring containers or the host. It monitors CPU and excessive memory usage of containers and enforces restrictions when necessary.
Joyent Triton is another interesting option which uses SmartOS Zones for isolation. Zones is a proven isolation technology used by early container technologies like Solaris.
Hyper is a cloud startup that uses a new type of container called HyperContainer which is a blend of a VM and a container. While HyperContainer includes a hypervisor, it doesn't package a container inside a VM like most CaaS offerings do. Instead, it keeps the hypervisor really lightweight. Hyper runs these containers on top of bare-metal servers and is able to isolate the containers at the hypervisor level.
CoreOS is another startup that is taking steps to make up for the weak defaults in Docker's isolation. It launched rkt, a container engine that allows isolation not just via namespaces and cgroups, but also using a hardware hypervisor. Docker lists hypervisor isolation as an upcoming feature.
Apart from rkt, CoreOS acquired the container registry Quay which can securely store and distribute container images. Quay includes a container image scanning tool Clair. Together, all these products from CoreOS are a promising alternative to Docker.
Docker's own efforts to improve isolation
Docker's stand is that its containers are built to be secure by default. It supports all Linux isolation features and further simplifies isolation with strong defaults. Additionally, Docker suggests adding AppArmor or Security-Enhanced Linux to "harden" containers. Docker has also released a script called Docker Bench that checks containers against the CIS benchmarks.
Apart from this, Docker is focused on building robust security for their commercial offering, Docker Data Center. This is in the form of the Docker Trusted Registry. It has security features that are common to what enterprises have, such as Lightweight Directory Access Protocol and Active Directory. It also supports role-based access control, which lets you distribute Docker images publicly, within your organization, within a particular team or to a select few. You can also keep your images private if you choose. Docker Content Trust ensures only those images built by your CI system are deployed on your cluster.
To conclude, isolation is a concern when working with containers for multi-tenant apps. CaaS services take the safe route of running containers inside VMs. Several startups are innovating with unique approaches to secure containers and isolation. Finally, Docker itself is keen on becoming enterprise-ready, and that means ensuring containers are isolated.







