
Better API security needed as companies modernize apps
As developers build more complex applications, the widespread use of APIs is creating significant security challenges for organizations, according to a new survey from ESG.
Application programming interfaces -- the code that enables software applications to communicate -- are a core component of modern applications. Developers use APIs to integrate third-party services, libraries and tools into their applications, saving themselves the effort of building these resources from scratch. They're crucial for mobile app development and web applications. Using APIs, developers can easily update or replace a component and scale apps as needed.
As developers have dramatically increased their use of APIs to meet business needs, however, security tools, processes and skill sets have not kept pace, explained Melinda Marks, senior analyst at TechTarget's Enterprise Strategy Group. A recent ESG survey on API security showed that virtually all organizations using APIs have experienced at least one security breach in the last 12 months and, despite their growing reliance on APIs, struggle with fundamental security measures.
"I was shocked by the concern about basic things -- 90% [of respondents] said they were concerned about authorization, which is essential for secure connections and access," said Marks, who covers applications and cloud security and co-authored the survey.
The survey, titled "Securing the API Attack Surface" and published August 24, 2023, is based on responses from 397 IT/information security and applications/DevOps professionals responsible for evaluating or purchasing cloud security technology products and services.
Survey results on the frequency of API updates also came as a surprise to Marks. Continuous integration and continuous deployment (CI/CD) is essential to keeping applications updated, "but CI/CD also means that changes are being made that require checking," she said. Thirty-five percent of respondents said they were updating APIs daily, 40% said weekly and 22% said monthly. "That 35% updating daily was a little alarming," she said, given the current state of API security programs.
In this Q&A, which was edited for clarity and length, Marks talks about why API security is challenging for organizations -- and urgently needed.
Talk a little about the motivation for doing this survey on API security.
 Melinda Marks
Melinda Marks
Melinda Marks: When we think about cloud native applications and developers, there's an increasing number of APIs -- application programming interfaces that they use to build more complex applications. The APIs enable applications to connect to other applications, other components and resources so the applications can provide more features and capabilities for users.
What makes these modern applications great -- the capabilities of these cloud-native applications and microservices-based applications -- is their complexity, their ability to make calls, to tap into more resources, to run in a dynamic way. And all of those things require and create increasing APIs.
As with a lot of things that enable increased productivity and innovation, people often don't think about the security implications and the fact that these enhanced capabilities also create extra attack surface areas where, if not managed properly and secured, there are ways for attackers to get in. And, if attackers have gotten in by some other route, they can also laterally move through the API connections to wreak havoc.
So, a big reason we wanted to do this research is that we know APIs are growing, and we know they're risky. In addition, there's a lot of buzz about APIs, a lot of marketing and a lot of security vendors talking about their products. People are trying to figure out what they need to do to address this: Do my current security tools address APIs? What else should I be looking at? How do I figure out how to reduce my risk so this isn't a big concern for my organization?
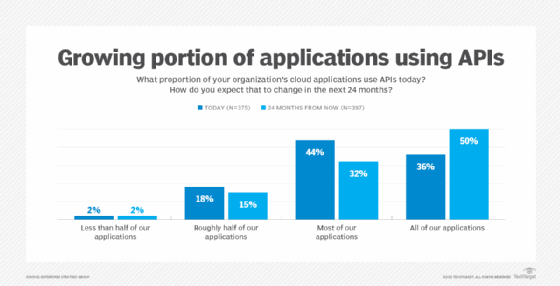
Can you elaborate on how the security risks related to APIs are different from those of other kinds of software?
Marks: When we think of application security breaches, we tend to think of attacks that hack the code it takes to build and run the application. If you look at application security resources like the OWASP Top 10 [consensus list of the critical security risks to web applications], it is has traditionally focused on the code that it takes to build the application and run the application. The highest vulnerabilities are typically things like code or SQL injection, access issues, cross-site scripting. Security teams look for ways to address these top application security risks.
But with cloud-native development, applications are built to run in dynamic environments where they can make calls and interact with resources and other applications. There are different components that you need to run the application. You have to secure everything that it takes to run the application, not just the code and the place where it's running. And a major part of the security in cloud native applications are those APIs where the connections are being made.
OWASP has developed a separate Top 10 list on API security challenges to address this risk, but it's still controversial. Some API security people I meet have questioned if it captures the right API threats. So, API security is one of things that is not well understood, and the attacks are rapidly evolving. For security organizations, it's a big challenge.
What did you find out about the prevalence of security incidents linked to API usage?
Marks: Ninety-two percent of respondents said they've experienced at least one security incident related to insecure APIs in the last 12 months -- a startling number -- and, of those, 57% said they've had multiple incidents.
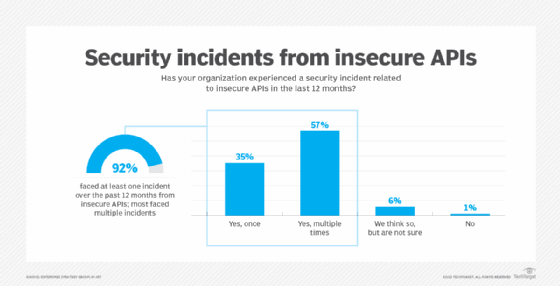
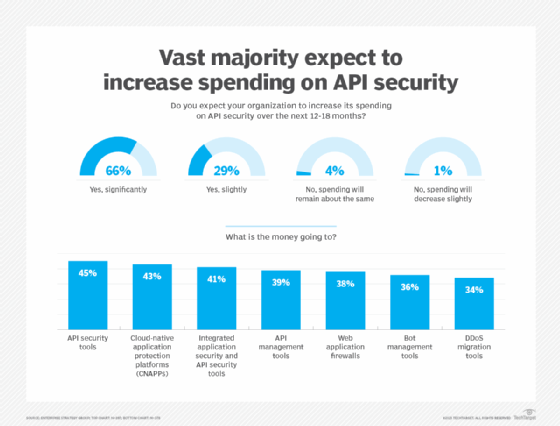
The good news is that with all the discussion about API security, people are getting the budget to spend on it: Ninety-five percent of respondents said they plan to increase API security spending in the next 12 to 18 months.
Now they have to figure out how to fix it.
Are some of the security problems with APIs related to the skill sets of the developers making the APIs, or to a lack of process for security and developers to work together?
Marks: All of the above. If the developers are just building their applications and they don't have that security mindset, this is a challenge because they're not taking the right steps to make sure their APIs are secure.
APIs are valuable for developers to use to build feature-rich applications, but they need awareness of security risks. When you think about the connections these applications need to make, authentication is a basic step. It's important to know that the place they're pulling the data from is secure, that it's the right source of information, that the connection is secure or else it is vulnerable to an attacker getting in there and stealing the data because something is not configured properly with the API.
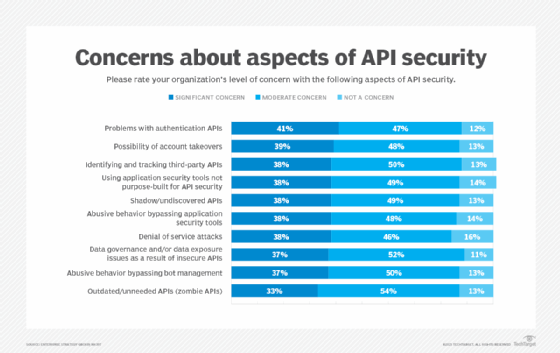
These are very basic things but remain a huge challenge: Nearly 90% of respondents cited API authentication as a concern, with 41% saying it was a significant concern.
What's the solution for improving API security -- a better team of coders, limiting the use of APIs?
Marks: Limiting the APIs is not really realistic. APIs are integral to how modern applications function. They're powerful tools for making better applications and bringing competitive advantages to companies. For example, people want to use banking applications that make it easy to shop and track their accounts, but these require APIs, and if a point of access is compromised, it could have serious consequences.
We need to make sure developers understand the security implications of APIs and have the processes and tools in place that provide visibility, take inventory, monitor and make sure they are effectively securing their APIs.
But there's a lot of complexity with cloud-native security. When you have a higher volume and speed of software releases, as you do in cloud-native apps, how do you get that visibility and how do you get the eyes into what's going on in development?
This is a challenge, but it is getting better now as security teams have more visibility into the early stages of development and get out of reactive mode. And there are a lot of effective, newer solutions that are focused on the API problem, monitoring APIs and identifying issues, allowing teams to react faster or tweak their programs to make sure they can more effectively manage risk for API usage.
What sorts of features are developers and security teams looking for in API tools?
Marks: There's a question in the survey listing some 15 different key API security capabilities -- identifying APIs with sensitive data, blocking excessive traffic, addressing the OWASP API Top 10, alerting on sensitive data exfiltration and so on. We asked respondents to rank the importance of the capabilities as very important, important, not that important or not at all important.
Everyone ranked all of them as very important or important, so that tells you something! They're looking for comprehensive solutions that address a variety of capabilities, from compliance and inventory to responding to attacks and helping with developer testing.
What steps should organizations take to assess their API security readiness?
Marks: What I recommend in general is to first look at what they're already using and check into whether there are API security capabilities included. When you're thinking of what tools to buy, you don't always have the choice of just buying the best tool out there or the luxury of building your ideal product, and you can't necessarily just rip things out and replace.
It's better to assess what capabilities you currently have and identify what's going to address the gaps in the most efficient way. Network security solutions may have integrated API security protection capabilities to detect and block API attacks. Application security solutions may include APIs for their testing, monitoring, protection and remediation capabilities. API management solutions may have security features and capabilities. Also, most cloud-native application protection platforms (CNAPPs) include API security because of their impact on security risk and the need to protect applications.
Once you assess where there are gaps, or where there may be too much manual effort involved to mitigate risk, you can evaluate whether a focused API security solution addresses your needs and can fit well with your overall security strategy. There are several newer vendors attuned to cloud-native environments that are strong in this area.
And there is more pressure on organizations to solve the problems related to API security. They need to stay informed on what will work, what won't work, what may not be effective, what may be an incomplete solution. And vendors need to be transparent and informative about how they can help.
Read the full report
Enterprise Strategy Group subscribers can click here for a report on the survey covered in this Q&A.








