
7 key OT security best practices
Keeping operational technology secure requires vigilance and effort, especially as OT increasingly converges with IT. These cybersecurity best practices can help.
Operational technology forms the backbone of critical industrial control systems, underpinning everything from energy production and water supply to manufacturing and transportation. Today, these systems increasingly use edge computing to connect to IT networks, turning OT devices into powerful IoT and industrial IoT endpoints.
This connectivity, however, also makes OT vulnerable to cyber attacks that could have devastating -- and possibly even fatal -- consequences.
Organizations that rely on OT should consider adopting the following OT security best practices to manage cyber-risk.
1. Place OT security under the CISO's control
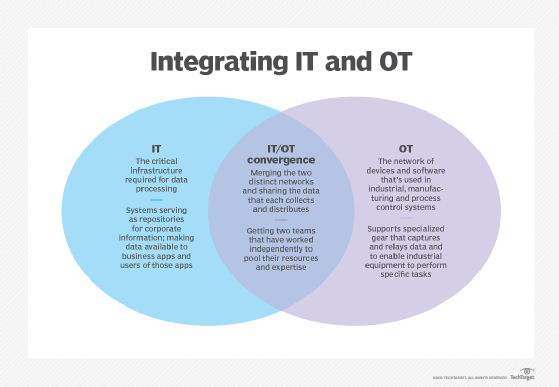
Traditionally, OT systems operated separately from IT departments, leading to a siloed approach to cybersecurity. But, with the increasing convergence of OT, IT, IoT and industrial IoT (IIoT), a unified strategy for combating cyberthreats is essential.
Placing OT cybersecurity under the CISO helps ensure the consistent application of security measures and optimize the organization's security posture. The CISO can provide the necessary oversight, resources and expertise to assess OT security risks accurately and detect and respond to threats and vulnerabilities effectively.
2. Identify and prioritize OT assets
Before an enterprise can defend its assets, it needs to know what -- and, importantly, where -- they are. Every organization should maintain an up-to-date inventory of all OT systems, hardware, software and related technologies.
In some organizations, various business units still manage OT asset inventories separately. Ideally, however, the security team has centralized, automated discovery and management capabilities with full visibility into the OT environment and attack surface.
After identifying assets, prioritize them based on their importance to operations. A system, say, that controls a power plant's turbine is likely more critical than the system that monitors the corporate office's ambient temperature.
By prioritizing its assets, an organization can satisfy the following important objectives:
- Focus investments on protecting high-priority assets.
- Establish incident response policies that secure the most sensitive assets first.
3. Conduct security awareness training
Humans are often the weakest link in the cybersecurity chain, and that holds true in OT environments. Regular security awareness training ensures all employees -- whether in IT, OT or nontechnical positions -- understand cyber-risks and their roles in mitigating them.
Security awareness training should cover the unique challenges presented by OT systems, including the potential consequences of critical infrastructure attacks.
4. Update and patch software regularly
OT systems can be vulnerable to exploits if they run outdated software. A strong patch management process ensures all systems receive timely updates.
OT connectivity is critical to operations, so updates and patches must undergo testing in a controlled environment before deployment. This minimizes network downtime and prevents potential operational disruptions caused by incompatible or faulty patches.
5. Control network access
Controlling who and what can connect to an OT network is paramount, using security tools such as identity and access management and network access control. Follow the principle of least privilege, and limit OT systems access to only those devices and users that absolutely need it to do their jobs. This can significantly reduce the risk of intrusions.
6. Consider a zero-trust framework
The zero-trust model operates on the principle of "never trust; always verify." Instead of assuming everything inside a company's network is safe, zero trust demands continuous authentication and authorization of all users and devices -- both internal and external.
Zero-trust technology can also use behavioral and context clues to identify suspicious activities, such as OT access requests at unusual times of day or from unexpected users. This can both limit a successful attacker's ability to move laterally once inside a network and prevent a rogue internal agent from exploiting critical infrastructure systems.
7. Deploy microsegmentation
Microsegmentation divides the enterprise network into small, secure zones, limiting an intruder's access to corporate resources.
In an OT context, this might mean implementing network segmentation so devices in one zone cannot communicate directly with those in another without proper authorization. This contains the potential spread of threats, ensuring that, even if one segment is compromised, other critical segments are not.
As the line between OT and IT continues to blur, comprehensive security practices must extend to OT environments. By adopting these OT security best practices, organizations can help ensure the protection and integrity of their critical OT systems, thereby safeguarding their operations and the public at large.





