What is extended detection and response (XDR)?
Extended detection and response (XDR) is a technology-driven cybersecurity process designed to help organizations detect and remediate security threats across their entire IT environment.
An XDR system is an evolution of endpoint detection and response (EDR) technology that expands endpoint security visibility and protections beyond PCs, smartphones and other endpoint devices. The broader scope of XDR includes networks, servers, cloud services and applications, as well as various security tools and identity providers that support user authentication processes.
XDR software collects cyberthreat data from sources that are typically disconnected. It aggregates and unifies that data into one security platform. XDR correlates security alerts and events across different domains, providing contextual insight into what's happening in an organization's IT infrastructure. It examines workloads for vulnerabilities, malware threat vectors and the overall IT ecosystem. It also helps prioritize and triage events when they occur.
All the data XDR platforms collect is normalized to support advanced analytics and artificial intelligence (AI) applications that can identify anomalies and detect potential security threats. Security analysts use XDR tools to correlate data and determine the root cause and scope of security incidents.
This article is part of
What is threat detection and response (TDR)? Complete guide
Response capabilities are a core part of XDR. These include endpoint protection as well as analyses of cloud workloads and overall cloud security. Once threats are detected, XDR platforms can coordinate the responses of various security tools to help mitigate the risk of cyberattacks, data breaches and other issues. Security teams often use incident response playbooks with XDR to automate containment of compromised assets through actions such as blocking malicious Internet Protocol (IP) addresses and quarantining users or devices.
Key components of XDR
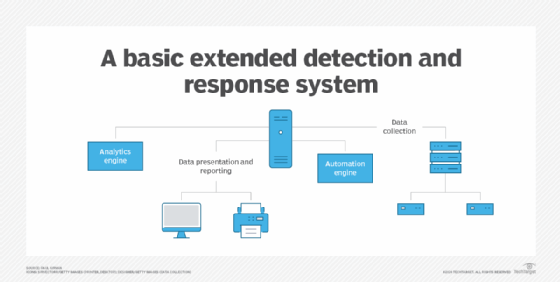
An XDR system is typically a collection of integrated technology platforms that perform specific functions, along with dashboard and reporting capabilities. XDR systems include the following platforms and systems:
- Analytics engine. This system receives and analyzes security event data from a variety of tools. AI is a key component of these scalable analytics engines.
- Automation engine. This one connects to and operates all analysis, threat detection, risk prioritization, threat hunting, event triage and mitigation activities.
- Automated tools. These present the analytics, report recommended actions and respond to attacks, among other functions.
XDR systems align with existing security tools. Platforms from different vendors can be integrated to create XDR tools, or a single vendor can provide native XDR capabilities.
How does XDR work?
XDR technology supports threat detection and response efforts through a multistep process that includes the following steps:
- Data collection and ingestion. The first step for an XDR system is to collect and ingest relevant telemetry data. XDR connectors pull in data from endpoint agents, network sensors, cloud platforms, identity systems, email and other sources. Common data types that are collected include endpoint activity, network traffic, log data, file metadata, process details, user behavior and IT alerts. Large volumes of historical and real-time data are consolidated into the XDR platform, where they're commonly stored in a data lake that can handle a variety of structured, semistructured and unstructured data.
- Analytics and threat detection. XDR tools aggregate the collected data and apply correlation rules, machine learning models, user and entity behavior analytics, and other advanced analytics techniques to detect known and unknown security threats. Analytics insights are presented in a unified management console that provides visibility into threats across IT environments. Security analysts can investigate detected threats using timeline analysis, threat hunting queries and other XDR capabilities.
- Automated responses and threat mitigation. Based on identified threats, XDR platforms trigger automated response actions defined in playbooks. Possible responses include isolating infected host systems, killing application processes, blocking IP addresses or domains, disabling user accounts and quarantining emails. Such actions are orchestrated across EDR tools; firewalls; antivirus software; security information and event management (SIEM) systems; security orchestration, automation and response (SOAR) platforms; and other security controls integrated with XDR technology.
- Centralized detection. XDR centralizes threat detection, investigation, hunting and response workflows, enabling security analysts to pivot as needed between workflows without switching to a different tool.
XDR's potential business benefits
XDR technologies can provide various benefits for enterprises and their security teams. In general, extended detection and response tools enhance threat protection and streamline security operations. More specifically, the potential benefits of XDR include the following:
- Enhanced security posture. XDR's comprehensive threat visibility, detection and response capabilities secure cloud and hybrid cloud environments against different types of cyberattacks and other security threats.
- Better security coverage. Ingesting diverse telemetry data closes visibility gaps and coverage blind spots that can result from using siloed security tools.
- Improved threat detection. Broader data collection by XDR tools enables earlier and more accurate detection of security threats across IT environments.
- Faster incident response. Automated workflows and playbook-driven responses support faster investigation and containment of detected threats than manual approaches.
- Increased productivity. Workflow consolidation and automation help to free up security analysts for more strategic work so they don't waste time on menial tasks.
- Simplified operations. XDR's unified management console, workflows and reporting functions streamline security operations and make them easier to manage.
- Reduced costs. Consolidating what otherwise would require multiple tools into a single XDR technology can reduce expenses compared with buying, deploying and managing different security products.

What's the difference between XDR and EDR?
XDR builds on EDR's capabilities but provides expanded abilities to detect and respond to threats. Here's a comparison of the two technologies:
- Data collection is from endpoints only with EDR, while XDR collects data from various sources.
- Similarly, EDR's threat detection scope and automated response capabilities are limited to endpoints. XDR can identify and respond to threats across an organization's entire IT environment.
- EDR's security analytics functions are endpoint-centric compared with XDR's centralization of analytics on data from the different sources it supports.
- Workflows are fragmented in EDR and unified in XDR.
- EDR provides per-tool management consoles vs. the single console built into XDR platforms.
XDR vs. managed detection and response
XDR and managed detection and response (MDR) both aim to improve threat detection and incident response capabilities in organizations, but they do so in different ways. XDR provides a set of technologies for internal deployment and use. MDR is a managed service offered by external security providers that does threat monitoring, detection, investigation and mitigation work. MDR services typically include separate XDR and EDR options to meet the needs of different customers.
Organizations can use both XDR software and MDR services. A business might augment its internal security team with third-party support by outsourcing some cybersecurity functions to an MDR provider. For example, the MDR service might be responsible for dealing with advanced threats that the company's security staff doesn't have the resources or skills to handle.
What is the difference between XDR and SIEM?
SIEM tools primarily gather and analyze security event data, facilitate the launch of incident response activities and generate security data that SOAR systems use. XDR systems perform many of the same tasks as SIEM and SOAR systems, but they also deliver greater performance and functionality. XDR systems use data collected and analyzed by SIEM systems, and, ideally, the two technologies complement each other in a security operations center (SOC).
Challenges to be aware of on XDR
The term XDR was coined in 2018 by Nir Zuk, founder and CTO of security software and services vendor Palo Alto Networks. Initially, XDR was defined in different ways, which caused confusion about the technology.
Today, there's a common understanding of what XDR is. Nonetheless, XDR deployments come with some challenges. Potential drawbacks include the following:
- IT complexity. Implementing XDR security tools can add complexity to IT environments because of the need to deploy connectors to various data sources.
- Coverage gaps. Endpoint-centric XDR options might lack full network and cloud visibility if an organization is using other tools that are purpose-built for a specific type of threat detection.
- Staffing and skills limitations. Installing XDR software doesn't eliminate the need for skilled resources to take advantage of its capabilities. But there's a persistent lack of experienced cybersecurity professionals overall. If an organization doesn't have the required skills, it must hire people with them, train existing workers on XDR or turn to an MDR service.
- Training. Even if an organization already has a skilled cybersecurity staff, XDR introduces new workflows, use cases and tools that might require additional training for effective use.
- Vendor dependence. Relying on a single XDR provider's security software stack creates a risk of vendor lock-in.
- Increased costs. XDR's data collection, storage and analytics functions can drive higher IT infrastructure costs.
How to implement XDR in an organization
The following nine steps are a good way to start out with an XDR system:
- Review and update cybersecurity requirements. Assess existing security capabilities and strategies and consider what additional ones are needed.
- Examine security systems. Identify features and functions not currently in use or ones that need a performance boost.
- Secure management approval and budgeting. Prepare a presentation for senior management that includes a return on investment analysis and evaluates costs and features of candidate systems.
- Check out security system options. Assess whether it makes sense to invest in SIEM and SOAR, and then migrate to XDR.
- Establish a project plan and team. Consider adding external third-party expertise.
- Use a multiphase rollout. Ensure that each phase is tested before moving to the next.
- Provide training. Train SOC teams and provide briefings for employees and senior management.
- Maintain and support. Establish schedules for system patching and other maintenance activities.
- Ensure continuous improvement. Schedule periodic system assessments for ongoing improvement.
Key capabilities of XDR tools
XDR tools include the following core capabilities and features:
- Data collection and ingestion from multiple sources.
- Data correlation and normalization to prepare data so it's useful for analytics.
- A centralized data lake to store the collected data in one place.
- Data enrichment with threat intelligence and other contextual information.
- Advanced analytics and AI techniques, such as machine learning and behavior analytics.
- Unified threat hunting and investigation across an IT environment.
- Automated response actions defined by organizations in incident response playbooks.
- Consolidated workflows for threat detection and management.
- Reporting features to provide visibility into security operations and metrics.
Learn more about XDR platforms and vendors, specifically the difference between open XDR and native XDR.







