What is geolocation? Explaining how geolocation data works
Geolocation technology identifies physical locations of devices and individuals based on information such as geographic coordinates and Internet Protocol (IP) addresses. The term isn't used a lot, but it has become more commonplace. Most tech users rely on geolocation technology even if they don't realize it.
Devices connected to the internet use geolocation data to provide smarter, more personalized navigation. The technology comes with drawbacks, including privacy issues and the potential misuse of personal information. Nevertheless, it has pragmatic and practical uses in various industries and for consumers, making it nearly ubiquitous.
Geolocation data is typically collected by various entities, including internet service providers, mobile app developers, governments, law enforcement and advertisers. With accurate geolocation data, a brand can target advertising to specific customers, and app developers can build better navigational apps for mobile devices.
How geolocation works
Internet-connected devices, such as smartphones, laptops, tablets, smart cars, internet of things (IoT) sensors and smart watches, are conducive to sending geolocation data to entities that require it. These devices are assigned IP addresses for identification purposes. They can also have built-in Global Positioning System (GPS) receivers so satellite technology can track their physical locations.
An internet connection isn't needed for GPS-enabled devices because they use satellite signals to determine location. However, all other geolocation methods require an internet connection, such through Wi-Fi or a cellular network.
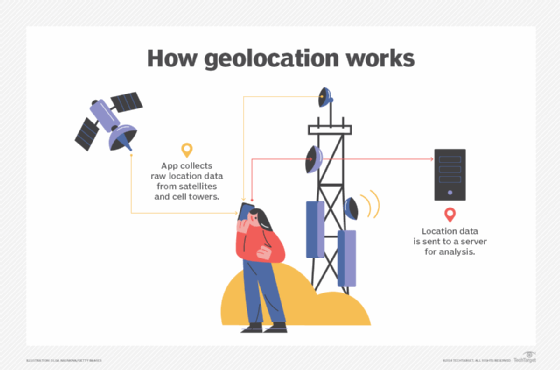
The process involved in geolocation data collection involves these key steps:
- Collection. A device collects raw data about its location from multiple sources. It does this by sending GPS signals, Wi-Fi pings and cellular data exchanges and then seeing how long it takes to get a response back.
- Transmission. The raw data is transmitted to the central server or cloud infrastructure that operates a geolocation app or service through different communications protocols, such as GPS or cell networks.
- Triangulation. Using this raw data, the device determines its location by measuring its distance from multiple cell towers, Wi-Fi access points or satellites.
- Processing. Algorithms process the raw data to produce accurate location data.
Geolocation data collection methods
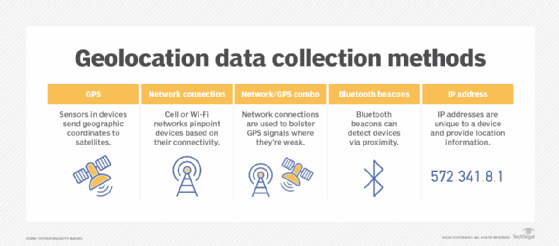
The most common geolocation methods for accessing data sources include the following:
- GPS. GPS pinpoints a device's location based on latitude and longitude coordinates. It only works for devices with built-in GPS sensors.
- Network connection. Cell phones and other internet-connected devices can be located wirelessly through a connection to a cell tower or Wi-Fi network.
- Combined GPS and cell towers. If a device has both a built-in GPS sensor and a cell connection, a combined approach to the location of a device is more reliable because the cellular connection can take over in geographical locations when the GPS signal is weak.
- Bluetooth beacons. Bluetooth-enabled beacons are small pieces of hardware capable of transmitting data via radio waves. They are placed in different locations so devices can determine their distance from them. However, this is proximity-based and doesn't work over long distances.
- IP addresses. These long numerical sequences are used as unique identifiers. Since no two IP addresses are the same, IP geolocation is a convenient way to identify the location of specific devices.
Why should businesses care about geolocation data?
Geolocation isn't limited to navigation on mobile phones. It has many practical uses across various industries. At the enterprise level, geolocation data assists in many different tasks:
- Sales and marketing efforts. Business analytics applications use location data about customers and website or social media visitors to reach them with offers and sales pitches that consider where they physically are.
- Fraud detection. Geolocation data is a useful component in fraud prevention. A user can pair a device, such as a smartphone, with a specific form of payment, such as a credit card. If a malicious actor attempts to use this card with a different device, geolocation data is used to determine that the device doesn't belong to the user.
- Increasing efficiency. Geolocation data lets logistics and delivery companies do real-time tracking. It's one of multiple factors involved in optimizing routes to deliver goods and location-based services faster and more efficiently to customers.
- Real-time fleet and vehicle safety. Geolocation data not only tracks individual vehicles and fleets of vehicles but also assists with real-time incident management to enhance their safety. A cargo ship experiencing a malfunction at sea, for instance, can provide GPS coordinates to a repair team, allowing them to offer help much more quickly.
- Connected devices. IoT and industrial IoT devices can be implemented in various industries. Depending on how far assets are placed from each other, these devices can rely on geolocation data to transmit important data, such as performance data.
Geolocation use cases and examples
Industries where geolocation plays an important role include the following:
- Finance. Device data coupled with payment methods facilitates fraud detection in finance and banking. Users can be immediately notified when unauthorized devices from different locations use their payment methods.
- Logistics. Route optimization and incident management in supply chains require precise geolocation data. With this information, any impediments to delivering goods and services can be addressed faster and more easily. For example, a trucking company might have vehicles break down, creating supply chain issues. With geolocation data, dispatchers can quickly locate a truck and send a repair team to fix it.
- Retail. Geolocation lets businesses use the geographic locations of their customers to tailor their marketing strategies. This is especially important in e-commerce where customers are scattered nationally or even globally. An online retailer, such as Amazon, relies on this data for clues about and insight into a customer's preferences.
- Health services. Health providers can use geolocation data to improve their emergency services and reach patients faster. For example, accurate location data lets emergency medical teams reach patients with critical health issues faster.
- Architecture and construction. Geolocation data makes it easier to identify building sites and equipment. While radio frequency identification tags are useful for tracking nearby assets used in construction, geolocation provides a broader scope of location information when sites, personnel and materials required are in different locations covering long distances. For instance, a construction firm contracted to build multiple locations of a business in a municipal or regional area can use geolocation data to better coordinate the movement of equipment needed at different sites.
Geolocation accuracy and limitations
Multiple factors determine the accuracy of a device's geolocation capabilities. These include the following:
- Device type. The device being used can affect geolocation accuracy. For example, mobile devices typically provide more accurate geolocation readings than stationary ones. This is because mobile devices usually have built-in GPS sensors and more constant cellular or Wi-Fi connectivity. Desktops, on the other hand, have Wi-Fi on less frequently and lack triangulation.
- Data collection method. The various data collection methods aren't equal in accuracy. For instance, IP geolocation is typically less accurate than network connections.
- Surrounding environment. Urban environments typically have many more nearby cell towers and Wi-Fi access points than rural areas, therefore enhancing accuracy. With GPS signals, physical buildings, obstructions and weather conditions can be a problem. GPS is often combined with cell technology to counterbalance weak GPS signals. GPS can also be combined with Wi-Fi, cellular and Bluetooth to enhance location accuracy.
Geolocation privacy issues
Geolocation data is often considered sensitive personal information that, in the wrong hands, could put a person or property at risk. Organizations handling this data must use security software tools and methods to safeguard it.
Misuse isn't limited to malicious actors. The organizations that collect this data can also handle it improperly or fail to be transparent about how they plan to use the data. Transparency issues arise when organizations that collect and process geolocation data don't tell customers or clients upfront how they plan to use the data. Various data privacy regulations, such as the European Union's General Data Protection Regulation, require transparency and consent.
Privacy issues also occur when organizations share geolocation data with third parties to improve geolocation services or for other purposes. For example, a person might give their bank permission to use real-time geolocation data to help locate nearby ATMs or bank branches on their cell phone as they move around a city. However, if the bank then sends that information to a third party, that vendor might use it for marketing and advertising in ways the customer finds intrusive and wrong.
Many people don't consider the collection of macro information on the country, state or even city they're located in as raising privacy issues. Problems happen when street-level data and home addresses are collected. This can be deemed sensitive location information depending on the jurisdiction. In the U.S., different states determine what is acceptable to track when individuals use mobile devices.
How to mitigate risks associated with geolocation
There are various ways to mitigate the security and privacy risks of geolocation data collection technology. These methods can also empower executives and employees alike to be cognizant of geolocation risks in their personal lives outside work. They include the following:
- Develop internal policies. An organization can craft detailed policies around privacy and security that dictate the terms for allowing geolocation data and determine acceptable use. Those writing them must be aware of global, federal, state and local privacy laws that affect them. And compliance is key when implementing these policies.
- Implement controls. Appropriate controls should be mandated for all employees. These include setting and configuring apps to limit geolocational data and implementing security measures such as access control and encryption to protect an organization's private data.
- Data classification. To further protect sensitive information, an organization can develop a system for classifying geolocation data as either safe or threatening to privacy and security.
- Training employees. Training programs increase employees' awareness of how devices and apps administered through their organizations use geolocation data and pose possible risks.
- Transparency. An organization's policies should make clear to customers and clients exactly how geolocation data is collected, processed and used. Employees must also understand what data is collected and how it's used to ensure they comply with applicable laws and regulations.
Spatial analysis and geolocation have some commonalities. Spatial analysis is the use of data that references a specific geographical area or location. Explore how spatial analysis is used for deeper insights from location data.





