11 IoT security challenges and how to overcome them
While influential and beneficial, IoT introduces several security challenges, from device discovery and patching to access control and cyberattacks.
From smartwatches to smart streetlights, smart home devices to smart manufacturing, the internet of things has revolutionized how people and organizations operate, improving efficiencies and optimizing processes.
With these benefits, however, comes a major challenge: IoT increases the number and types of security risks businesses and consumers face. Any device that connects to the internet is a potential entry point to the larger network and the sensitive data it contains. IoT-related cyberattacks could be detrimental to a business or, in some cases, life-threatening or deadly.
Here are 11 of the many inherent IoT security challenges and how to mitigate them.
1. Expanding attack surface
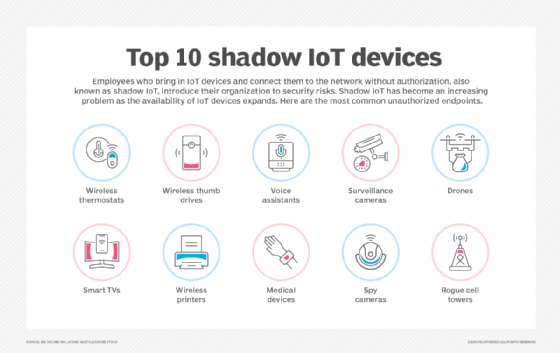
Challenge: The sheer number, variety and complexity of IoT devices create a vast attack surface for security teams to manage and secure. Yet, as one of the oldest security adages goes, "You can't protect what you can't see." This is especially true in the case of IoT, with small sensors and little internet-enabled devices deployed across networks and geographies that often lack oversight and management. Without proper visibility into what devices are connecting to their networks -- a problem known as shadow IT -- organizations are subject to unauthorized access, data loss, attacks and operational disruptions.
Solution:
- Perform asset discovery. Use port scanning, protocol analysis and other detection techniques to determine which devices are connecting to networks. Free tools, such as Nmap, Shodan and Masscan, are available, as are commercial products and services that help discover, identify and manage IoT devices.
- Create and maintain an asset register. List approved devices on an enterprise asset register, along with each device's associated patch management processes and lifecycle information.
- Conduct a risk assessment. Perform an IoT risk assessment to understand what the devices can -- and should -- have access to and why.
2. Access control
Challenge: IoT devices have a unique identifier that aids authentication and authorization. After discovering which devices connect to the network, organizations need to assess what they can access and talk to. With hundreds or thousands of unique IDs to manage, this can be a daunting task.
Solution:
- Principle of least privilege. Use the POLP to permit devices to access only what is necessary for them to do their job.
- Strong passwords. Update any device that comes with a factory-installed password. Use MFA when possible. Consider biometrics, if feasible.
- Hardware-based roots of trust. Generally considered the strongest IoT security option, hardware-based roots of trust are built directly into hardware and embedded on devices.
- Digital certificates. Digital certificates can be used, but some IoT devices do not have the ability to process them. Other lightweight cryptographic algorithms can be used in this instance (see "Encryption and data security" section below for more on that).
- Zero trust. Take a zero-trust security approach to control devices and access rights.
- IoT platforms. Commercial IoT platforms offer features to manage devices and control what data other devices and network devices can access.
3. IoT passwords
Challenge: Remember the 2016 Mirai attacks? They were traced to connected cameras and other IoT devices that had factory-default or hardcoded passwords. Cybercriminals infiltrated servers using these devices and a list of known credentials -- a list that, by some accounts, only had 60 username/password combinations.
Solution: Hardcoded passwords are a problem that only manufacturers can solve. Organizations should only choose software that does not use hardcoded passwords, and manufacturers should not produce products with them.
Consider the following tactics for other default and password security challenges:
- Update default passwords, if possible.
- Implement an enterprise password policy.
- Require strong, unique passwords.
4. Patch management
Challenge: IoT devices present several unique patching and updating challenges:
- IoT devices that use proprietary or outdated software, firmware and hardware. The OS, applications and communications technology might not be able to be updated because it is old, legacy or retired.
- Some devices are physically inaccessible. Consider sensors dispersed across hundreds of acres of farmland to detect temperature, humidity and moisture. Sensors on top of a bridge monitoring its vibration and the weather pose a similar challenge.
- Not all devices can be taken offline for long periods of time to perform updates. Consider critical smart manufacturing equipment that could cost an industrial IoT organization millions of dollars if it's taken offline for an hour, smart grids that millions of people depend on for heat or electricity, and smart medical devices that keep people alive.
- Some IoT devices have no UI or screen. And, to further complicate things, some won't even accept updates.
- Vendors create issues, too. Some devices reach end of life and are no longer supported by the manufacturer. Similarly, some vendors don't realize security updates with vulnerabilities are discovered, leaving customers open to breaches.
- Patching operational technology is tough. OT networks historically never connected to the internet and did not pose an imminent threat to IT networks. Legacy OT systems -- some decades old -- often run their own proprietary systems, which can make patching more difficult.
Solution:
- Track patches. Enter each IoT device deployed into an asset register as part of the device discovery or adoption process. Include which versions of software, firmware and hardware each device runs and keep track of when updates are available and installed. Also, track when devices reach end of life and must be retired.
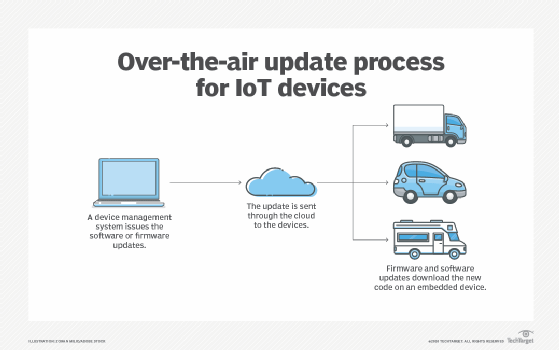
- Think about patching predeployment. Consider potential patching and updating processes before adopting. Ensure the availability and security of over-the-air updates. Also, decide between automatic updates and periodic schedules, as each has its own set of benefits and drawbacks.
- Consider IoT platform capabilities. Many IoT platforms contain features to simplify patching and updating processes, such as automation, and can manage devices that require rollbacks or resets.
5. IoT cyberattacks
Challenge: IoT systems are subject to the same cyberthreats as other cyber environments, including DDoS attacks, botnets, malware and ransomware.
Solution:
- Use intrusion prevention/detection systems (IPSes/IDSes) with DDoS protection features.
- Partner with an ISP that detects and filters DDoS packets.
- Follow basic cyber hygiene best practices, including the use of firewalls, antimalware, endpoint security platforms, endpoint detection and response, and extended detection and response.
- Keep software up to date.
- Change default passwords.
- Monitor network traffic.
- Segment which data and networks IoT devices can access.
- Disable unnecessary features on IoT devices.
- Regularly back up data from devices and networks.
6. Physical security
Challenge: Protect IoT devices from not only cybersecurity threats but also physical security threats. Because IoT hardware -- including IoT sensors, wearables and edge devices -- is more easily accessible than other network components, it is subject to physical damage, tampering and theft.
For example, attackers could attach a device that exfiltrates data to unsecured IoT devices that have been physically broken into. Or, storage mechanisms could be removed and their data stolen.
Solution:
- Harden IoT devices.
- Embed security on the device.
- Ensure proper access control.
- Change default passwords.
- Encrypt data and connections.
- Remove or disable unused ports.
- Ensure IoT devices cannot be easily disassembled or components removed.
- Put devices in a tamper-resistant case or render the device unusable after physical tampering, if necessary.
7. Encryption and data security
Challenge: Cryptography is a mechanism that prevents privacy risks, protects data integrity and ensures secure communications. Many connected devices, however, don't have the power, processing or memory resources required to run traditional encryption algorithms, such as AES. Such devices must use an algorithm with high security but low consumption -- one that considers the size, power consumption and processing capabilities of resource-constrained devices.
Solution:
- Use lightweight cryptographic ciphers. Elliptical curve cryptography (ECC), for example, provides the security equivalent of Rivest-Shamir-Adleman, or RSA, but with smaller key sizes and operations that require less processing, making it an ideal option for devices with lower storage space, processing power and battery life. Other lightweight ciphers include Clefia, a lightweight AES cipher; Enocoro, a hardware-oriented stream cipher; Speck, an add-rotate-XOR cipher; and Ascon, a family of symmetric-key cryptographic standards selected by NIST for future standardization.
- Use trusted security protocols. Consider TLS or Datagram TLS, IPsec, MQTT and OAuth 2.0, among others.
- Consider PKI. Public key infrastructure can be embedded into devices at the manufacturing or enterprise level. PKI issues unique identities and digital certificates to devices and supports the distribution and identification of public encryption keys, enabling users and devices to exchange data securely.
- Prepare for quantum computing. When it becomes viable, quantum computing will be capable of breaking asymmetric cryptography, including algorithms such as RSA and ECC. Organizations should include IoT devices in their post-quantum security planning.
8. Network security
Challenge: The scale and diversity of IoT devices connecting to an enterprise network make it difficult for admins to manage and maintain network security.
Solution:
- Use network segmentation to separate IoT, OT and IT networks. Put different networks or parts of networks into different zones to create subnetworks -- using one zone each for sales, finance, operations and so forth. Customize each zone's security policies based on its users, devices and data.
- Use an IoT gateway. An IoT gateway can mitigate the efficiency and connectivity issues that can accompany network segmentation. Acting as an intermediary between the device and the network, a security gateway has more processing power, memory and compute capabilities than the IoT devices connecting to it. It can therefore implement stronger security measures -- such as firewalls and antimalware -- closer to the devices, preventing security threats from passing through to the network.
- Use network security technologies. These include antimalware, firewalls, IDSes and IPSes.
- Manage ports. Disable port forwarding and never open ports when not needed.
- Block unauthorized IP addresses. Use allowlisting and denylisting to block unauthorized and malicious IP addresses.
- Monitor bandwidth. Add bandwidth as needed to ensure applications receive the bandwidth needed to maintain productivity and efficiency.
- Use continuous traffic management and monitoring. Monitor network traffic in real time to protect data and communications, detect abnormal activity and identify potential threats.
- IoT communications protocols. Consider the security of IoT communications protocols, such as Bluetooth, Bluetooth Low Energy, cellular, MQTT, Wi-Fi, Zigbee and Z-Wave. Insecure communications are prone to eavesdropping and man-in-the-middle attacks.
- Penetration testing. Include connected devices in penetration tests to assess vulnerabilities.
- Create IoT policies. Establish policies and capabilities to manage lost or stolen devices, such as remote wiping and disabling connectivity.

9. Lack of standardization
Challenge: The IoT industry has been plagued by a lack of standardization from the start, both in terms of security and otherwise. Global standards help ensure consistency, compatibility and security among products and applications -- a necessity for IoT environments to function smoothly.
Solution:
Legislation, regulations and standards are emerging to remedy this, including the following:
- The U.S. Cyber Trust Mark program, launched in January 2025, is a voluntary certification program that helps identify smart consumer devices that have met recommended security standards.
- Enacted in December 2024, the EU Cyber Resilience Act requires manufacturers to ensure security throughout the product lifecycle.
- In May 2021, a U.S. presidential executive order, "Improving the Nation's Cybersecurity," called for a consumer IoT labeling program to launch in 2023. The aim of the program is to inform consumers about the risks of their smart home devices.
- The U.S.'s 2020 IoT Cybersecurity Improvement Act required NIST and the U.S. Office of Management and Budget to develop guidelines and standards around security measures on IoT devices used by the federal government.
- Approved in 2018, California's SB-327, "Information privacy: connected devices," requires manufacturers to equip devices with "reasonable" security features, including a preprogrammed unique password for each device and a setting that requires a new password to be created upon first use.
- In 2018, the U.K. published "Code of Practice for Consumer IoT Security," the European Telecommunications Standards Institute's Technical Specification 103 645, a standard to regulate the safety of consumer devices.
NIST has introduced IoT guidance, including NIST Special Publication 800-213A and NIST SP 800-213, as well as several interagency reports.
Other legislation, including GDPR, HIPAA and CCPA, also affects IoT security, as do industry regulations. Companies should keep abreast of any new standards -- government, consumer or otherwise. These will influence IoT device manufacturing and security standards in the future.
10. Skills gap
Challenge: The skills gap has affected every industry, and IoT is no different. One thing that sets IoT apart from other industries is that it is still a fairly new discipline. It is also a convergence of IT and OT, meaning those fluent in OT are likely not well versed in IT, and vice versa. In addition, IoT isn't a single discipline. Successful IoT professionals require many skills, from cybersecurity and UX design to machine learning, AI knowledge and application development.
Solution:
- IoT-specific certifications and trainings have emerged, including some that are IoT security-specific, which provide a baseline knowledge of connected environments.
- Invest in trainings and certifications for in-house employees.
- Hire third parties and consultants for IoT-specific projects.
11. Remote work and smart home risks
Challenge: Remote workers can present security risks to organizations, especially if employees' IoT devices -- think smart TVs, connected baby monitors and smart fridges -- use the same networks employees use to connect to their company's data and systems. An attacker who infiltrates a smart thermostat, for example, could potentially also access confidential corporate data. Likewise, smart speakers could create a privacy issue if they overhear conference calls or video chats.
Solution:
- Include IoT security in regular security awareness trainings.
- Use policies to prevent IoT devices from creating enterprise security issues.
Sharon Shea is executive editor of Informa TechTarget's SearchSecurity site.