How to build a data protection policy, with template
Enterprises can't afford to operate without a sound data protection policy that specifies business goals, stakeholders, regulatory obligations, data classifications and access.
Every modern enterprise runs on data. Competitive new product designs, complex financial matters, detailed corporate plans and sensitive customer information are all built on data, the foundation of virtually every aspect of business operations. But data also presents a risk. Exposing certain data by accident, negligence or malfeasance can cause serious harm to the enterprise. Every organization bears full responsibility for safeguarding its data, typically beginning with the formation of a data protection policy.
A data protection policy is a formalized written document that outlines the ways in which a business will protect important and sensitive data. It typically defines the goals involved in data protection and lays out the general rules and guidelines to meet those goals. The goals and guidelines generally align closely with the prevailing compliance environment and seek to meet broadly adopted industry practices or adhere to specific current regulatory legislation, such as the GDPR or CCPA.
A data protection policy does not define implementation or specify the tools or technologies to establish an appropriate data protection environment. That's by design. The policy defines what is to be done. Precisely how that policy is implemented and enforced is deliberately open-ended. A company can adopt any suitable infrastructure to meet the policy and change the tools, technologies and tactics over time as needs evolve.
Why a data protection policy is important
Data carries risk to the business. The loss or theft of sensitive data -- especially data that involves information about people -- can result in a significant loss of reputation for an enterprise. A breach event can also expose the company and its senior officers to significant fines and other serious penalties. The potential consequences of a data breach can be so severe that business leaders simply can't afford not to establish a data protection policy.
By creating and following a data protection policy, an organization can demonstrate it recognizes the value of its data and has a commitment to ensure its proper protection. There are other considerations that can benefit from a data protection policy, including the following:
- Legal protection. There's an old legal truism: If it's not written down, it doesn't exist. Creating a formal data protection policy provides an enterprise with the opportunity to document its attention to data and identify any weaknesses in its data protection posture that can be corrected before a breach occurs. Without a suitable policy, data protection tends to be a patchwork of ad hoc technologies that often don't provide the coherent protection a business requires. If a data breach occurs, the presence of a policy and documentation of its implementation enables an organization to discover why a data breach occurred and take proactive remediation. That can often help mitigate fines and other penalties arising from a breach.
- Business partnerships. All businesses are governed by data protection regulations. When one business shares sensitive data with a partner, the source of that data will expect, even require, the partner receiving the data to possess and implement a suitable data protection policy. That reduces secondary risk for the business providing the data to a partner that experiences a data breach.
- Lending and investing. Conscientious lenders, such as banks, and the investment community, such as venture capitalists, recognize the value of business data and its risks. A well-considered and properly implemented data protection policy can be a vital document in securing a business loan or approaching investors to demonstrate compliance with prevailing legislation or industry practices.
Key elements of a data protection policy
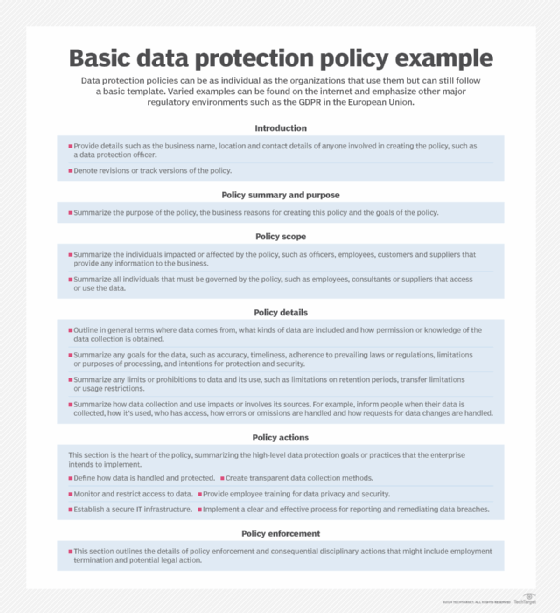
There's no universal format or content requirement for a data protection policy. The focus of any policy, as well as its key elements, will depend on the individual business as well as the various regulations and practices that affect the business. In broad terms, a data protection policy is a high-level document that should typically focus on three main areas:
- Access. Access control policy areas define who can access which types of data and prevent unauthorized access to anyone who doesn't need access.
- Availability. Data must be intact and available when the business needs it. Data availability policies define how data is backed up -- including onsite, offsite, cloud and remote -- and restored in the event of loss or damage, such as a disk failure. High availability and disaster recovery schemes might also be defined for certain data types.
- Security. Data security policies influence the ways in which data is safeguarded from accidental disclosure or intentional malicious attacks. Actions might include encrypting data at rest and in flight as well as other goals like intrusion prevention and anti-malware mandates.
A data protection policy can address a wide range of topics relevant to a company's specific needs. Common elements of a data protection policy can include the following:
- A backgrounder outlining the organization's need for data protection -- why the policy is needed.
- A summary of industry standards, regulatory legislation and business governance that requires the need for a data protection policy.
- A general summary of the organization's approach to data protection.
- The roles and responsibilities involved in data protection -- who can access data and their involvement in data protection.
- A detailed definition of data types -- what kinds of data the business collects and uses.
- What data is collected, and if necessary, how data collection is minimized.
- How data is classified -- for example, protected regulated data, confidential data or public data.
- How access to data is authorized, such as the use of least-privilege principles, and reviewed.
- How each data type is used by the organization.
- How the rights of data subjects are protected according to regulations like the GDPR.
- How each data type is secured, monitored, retained and destroyed.
- How the data protection policy is enforced.
- How the data protection plan is reviewed and updated.
- How the business demonstrates its accountability under the data protection policy.
- How data breaches are to be mitigated and reported.
A data protection policy can link or refer to other documentation, such as technical implementation details or best practices guidelines. Such specific documents can be updated and refined separately from the overall data protection policy.
Building a data protection policy
Just as there's no single structure or content for a data protection policy, there's no single pathway to developing a policy. Every organization is different. Even though businesses might be governed by the same regulations and fundamental obligations, there are countless ways to achieve the same overall data protection goals. Regardless of the specific business or pertinent compliance environment, several worthwhile principles can help responsible business leaders craft a suitable data protection policy, including the following:
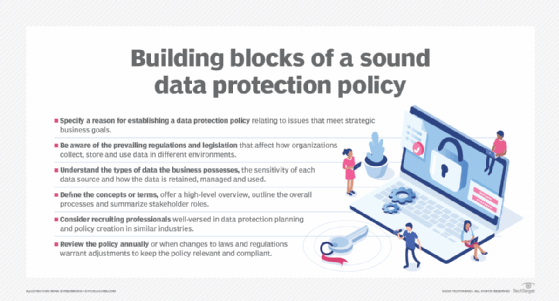
- Understand the goals. A data protection policy should start with a reason. It might be as straightforward as a means of ensuring compliance with prevailing regulations and legislation. Savvy organizations can take this further and see value in nuance such as clarifying the responsibilities of all parties, ensuring the integrity of business data or directing prompt and clear responses to data handling requests and management. A data protection policy can cover a lot of ground, so there are numerous opportunities to meet strategic business goals.
- Understand the obligations. Businesses must be aware of the prevailing regulations and legislation that affect operations in different environments. An enterprise operating in multiple jurisdictions or geopolitical regions could be subject to a myriad of different regulations. U.S. companies operating globally, for example, might be subject to individual state laws, such as the CCPA, federal regulations, like Sarbanes-Oxley, and other national and regional regulations, such as the EU's GDPR and Australia's Privacy Act. It's important to know which regulations apply to the business and how each regulation applies to data the organization collects, stores and uses.
- Understand the data. Take the time to understand the types of data that the organization possesses and weigh the sensitivity of each data source. There might be personally identifiable information of individuals, sensitive business data, such as designs or plans and public data like press releases and announcements. Each regulation can impact what data is collected and how it's retained, managed and used. Knowing the varied data across a business can allow proper categorization and help architect the most appropriate policies to ensure the company meets its data protection obligations for every data type.
- Focus on the what, not the how. A data protection policy is an expression of intent -- not implementation. The policy should define concepts or terms, offer a high-level overview of the policy's purpose, outline the overall processes to be adopted and how those workflows align with regulatory requirements, and summarize the various individual roles involved across the organization. Leave the details of technical implementation to other architectural or design documents, which can be created and updated separately.
- Engage a data protection professional. Establishing a sound data protection policy can be an onerous undertaking for the uninitiated, especially for smaller businesses scrambling to position themselves properly for ever-more numerous and complex data rules at every level. Consider seeking out professionals well-versed in data protection planning and policy creation related to the same industry or line of business. An experienced consultant or service can help shepherd a business through policy development and review. Larger companies might even hire an experienced full-time data compliance officer to support the enterprise.
- Review regularly. A data protection policy should be treated as a dynamic entity that's constantly evolving in response to changes in industry practices and ever-increasing regulatory demands. Most data protection policies are reviewed annually or when prevailing legislation is passed or changed. By keeping technical implementation details out of policy discussions, policy updates can be performed faster and more easily without making any changes to the underlying technical data protection infrastructure. Changes in legislation might require more frequent data backups, for example, but have no effective impact on the organization's actual backup and restoration mechanism.
Stephen J. Bigelow, senior technology editor at TechTarget, has more than 20 years of technical writing experience in the PC and technology industry.





