What is network security? Definition and best practices
Network security encompasses all the steps taken to protect the integrity of a computer network and the data within it. It involves a combination of tools, policies, protocols and practices designed to prevent unauthorized access, misuse, modification or denial of a network and its resources. Successful network security strategies use multiple security approaches to protect users and organizations from malware and cyberattacks, such as distributed denial-of-service (DDoS) attacks.
A network is composed of interconnected devices, such as computers, servers and wireless networks. Many of these devices are susceptible to attackers. Network security involves the use of software and hardware tools on a network or as software as a service. Security becomes more important as networks grow more complex, and enterprises rely more on their networks and data to conduct business. Security methods must evolve as threat actors create new attack methods on these increasingly complex networks.
No matter the specific method or enterprise security strategy, security is usually framed as everyone's responsibility because every user on the network represents a possible vulnerability in that network.
Why is network security important?
Network security is critical because it prevents cybercriminals from gaining access to valuable data and sensitive information. When hackers get hold of such data, they can cause a variety of problems, including identity theft, stolen assets and reputational harm.
The following are four of the most important reasons why protecting networks and the data they hold is important:
- Operational risks. An organization without adequate network security risks having its operations disrupted. Businesses and personal networks depend on devices and software that can't operate effectively when compromised by viruses, malware and cyberattacks. Businesses also rely on networks for most internal and external communication.
- Financial risks for compromised personally identifiable information (PII). Data breaches can be expensive for both individuals and businesses. Organizations that handle PII, such as Social Security numbers and passwords, are required to keep it safe. Exposure can cost the victims money in fines, restitution and repairing compromised devices. Data breaches and exposure can also ruin a company's reputation and expose it to lawsuits. IBM's "Cost of a Data Breach Report 2024," conducted by the Ponemon Institute, said the average cost of a data breach rose to $4.88 million in 2024 from $4.45 million in 2023.
- Financial risk for compromised intellectual property. Organizations can have their intellectual property stolen. The loss of a company's ideas, inventions and products is costly and can lead to loss of business and competitive advantages.
- Regulatory issues. Many governments require businesses to comply with data security regulations that cover aspects of network security. For example, medical organizations in the United States are required to comply with the regulations of the Health Insurance Portability and Accountability Act (HIPAA), and organizations in the European Union that deal with citizens' data must follow the General Data Protection Regulation (GDPR). Violations of these regulations can lead to fines, bans and possible jail time.
Network security is so important that several organizations focus on instituting and sharing strategies on how to adapt to modern threats. Mitre ATT&CK, the National Institute of Standards and Technology and the Center for Internet Security provide free, nonproprietary security frameworks and knowledge bases to share cyberthreat information and help businesses and other organizations evaluate their network security methods.
How does network security work?
Network security is enforced using a combination of hardware and software tools. The primary goal of network security is to prevent unauthorized access into or between parts of a network.
A security official or team determines strategies and policies that keep an organization's network safe and help it comply with security standards and regulations. Everyone on the network must abide by these security policies. Every point in the network where an authorized user could access data is also a point where data can be compromised, either by a malicious actor or through user carelessness or mistakes.
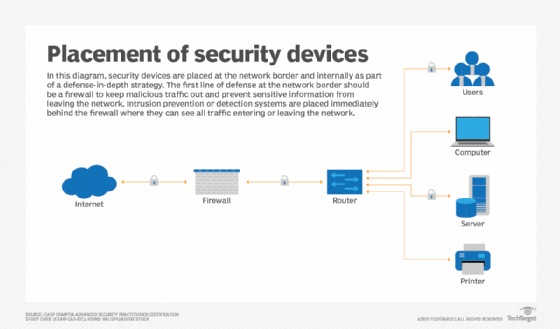
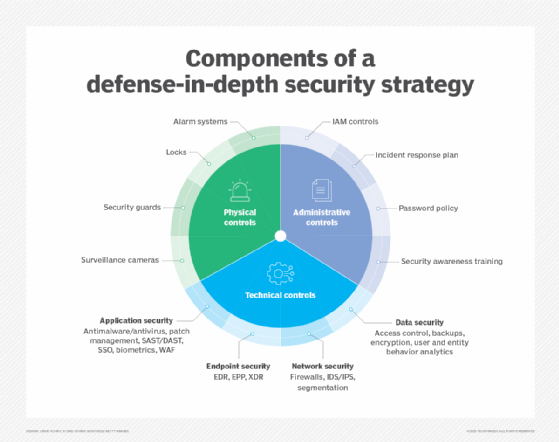
Network security professionals often use a defense-in-depth strategy, layering multiple controls so a breach at one level doesn't compromise the entire system. At the perimeter, firewalls, intrusion detection systems (IDSes), intrusion prevention systems (IPSes) and encrypted virtual private networks (VPNs) regulate traffic and block unauthorized access, while internal segmentation limits lateral movement attacks.
Endpoints are protected by tools such as antivirus, endpoint detection and response (EDR) and patch management. Networks are continuously monitored by behavioral analytics as well as security information and event management (SIEM) systems to detect anomalies. Strict access controls, such as multifactor authentication (MFA), network access control and role-based authentication, ensure only authorized users and devices can connect to the network. This multilayered approach, combined with ongoing monitoring and policy enforcement, helps maintain data integrity, availability and overall network security.
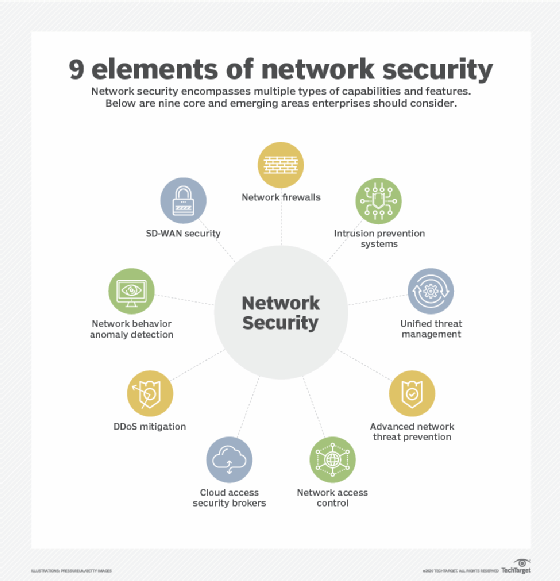
Types of network security software and tools
The choice of security policies and tools varies from network to network and changes over time. The following are commonly used types of network security tools and software:
- Access control. This approach limits access to network applications and systems to a specific group of users and devices. These systems deny access to users and devices not already sanctioned.
- Antivirus and antimalware. Antivirus and antimalware are software designed to detect, remove or prevent viruses and malware -- such as Trojan horses, ransomware and spyware -- from infecting a computer and, consequently, a network.
- Application security. It's crucial to monitor and protect applications that organizations use to run their businesses. This is true whether an organization creates that application or buys it, as modern malware threats often target open source code and containers that organizations use to build software and applications.
- Behavioral analytics. This method analyzes network behavior and automatically detects and alerts organizations to abnormal activities.
- Cloud security. Cloud providers often sell add-on cloud security tools that provide security capabilities in their cloud. The cloud provider manages the security of its overall infrastructure and offers tools for the user to protect their instances within it. For example, Amazon Web Services provides security groups that control the incoming and outgoing traffic associated with an application or resource.
- Data loss prevention. DLP tools monitor data in use, in motion and at rest to detect and prevent data breaches. They often classify the most important and at-risk data and can help train employees in best practices to protect that data. For instance, not sending important files as attachments in emails is one such best practice.
- Email security. Email is one of the most vulnerable points in a network. Employees become victims of phishing and malware attacks when they click on email links that secretly download malicious software. Email is also an insecure method of sending files and sensitive data that employees unwittingly engage in.
- Extended detection and response. XDR unifies and coordinates multiple security tools to detect, investigate and respond to threats across the entire network.
- Firewall. Software or firmware inspects incoming and outgoing traffic to prevent unauthorized network access. Firewalls are some of the most widely used security tools, positioned in multiple areas on the network. Next-generation firewalls offer increased protection against application-layer attacks and advanced malware defense with inline deep packet inspection.
- Intrusion detection system. An IDS detects unauthorized access attempts and flags them as potentially dangerous but doesn't remove them. An IDS and an IPS are often used in combination with a firewall.
- Intrusion prevention system. IPSes are designed to prevent intrusions by detecting and blocking unauthorized attempts to access a network.
- MFA. This approach to network security is easy to use and increasingly popular. It requires two or more factors to verify a user's identity. For example, Google Authenticator generates unique security codes that a user enters alongside their password to verify their identity.
- Mobile device security. Business applications for smartphones and other mobile devices have made these devices an important part of network security. Monitoring and controlling which mobile devices access a network and what they do once connected to a network is crucial for modern network security.
- Network segmentation. Organizations with large networks and network traffic often use network segmentation to break a network into smaller, easier-to-manage segments. This approach gives organizations more control of and increased visibility into traffic flow. Industrial network security is a subset of network segmentation, providing increased visibility into industrial control systems. ICSes are more at risk of cyberthreats because of increased integration with the cloud.
- Sandboxing. This approach lets organizations scan for malware by opening a file in an isolated environment before granting it access to the network. Once an organization opens a file in a sandbox, it can observe whether the file acts in a malicious way or shows any indications of malware.
- SIEM. This security management technique logs data from applications and network hardware and monitors for suspicious behavior. When an anomaly is detected, the SIEM system alerts the organization and takes other appropriate action.
- Software-defined perimeter. An SDP is a security method that sits on top of the network it protects, concealing it from attackers and unauthorized users. It uses identity criteria to limit access to resources and forms a virtual boundary around networked resources.
- Virtual private network. A VPN secures the connection from an endpoint to an organization's network. It uses tunneling protocols to encrypt information that's sent over a less secure network. Remote access VPNs let employees access their company network remotely.
- Vulnerability scanners. Vulnerability scanning is used to identify security weaknesses in systems and networks.
- Web security. This practice controls employee web use on an organization's network and devices, including blocking certain threats and websites. It also protects the integrity of an organization's websites.
- Wireless security. Wireless components are among the riskiest parts of a network and require stringent protections and monitoring. It's important to follow wireless security best practices, such as segmenting Wi-Fi users by service set identifiers, or SSIDs, and using 802.1X authentication. Good monitoring and auditing tools are needed to ensure wireless network security.
- Workload security. When organizations balance workloads among multiple devices across cloud and hybrid environments, they increase the potential attack surfaces. Workload security measures and secure load balancers are crucial to protecting the data contained in these workloads.
- Zero-trust network access. Similar to network access control, ZTNA only grants users the access they need to do their job. It blocks all other permissions.
Benefits of network security
The following are the main benefits of network security:
- Functionality. Network security ensures the ongoing high performance of the networks that businesses and individual users rely on.
- Privacy and security. Many organizations handle user data and must ensure the confidentiality, integrity and availability of data on a network, known as the CIA triad. Network security prevents security breaches that can expose PII and other sensitive information, damage a company's reputation and result in financial losses.
- Intellectual property protection. Intellectual property is key to many companies' ability to compete. Securing access to intellectual property related to products, services and business strategies helps organizations maintain their competitive edge.
- Compliance. Complying with data security and privacy regulations, such as HIPAA and GDPR, is legally required in many countries. Secure networks are a key part of adhering to these mandates.
- Protection against cyberthreats. Network security is a critical defense against the constantly evolving landscape of cybersecurity threats. By adopting strong security measures, organizations safeguard their systems against a range of attacks, including malware, ransomware, phishing and DDoS incidents.
- Trust building. Earning and maintaining trust is essential in today's interconnected business environment, and network security plays a central role in that effort. A strong security posture demonstrates to stakeholders that their data is well protected, enhancing the organization's reputation and building long-term trust.
- Secure digital transformation. As organizations embrace cloud computing, remote work and the internet of things (IoT), network security becomes a key enabler of digital transformation. It helps businesses innovate and expand their digital footprint with confidence, knowing that critical assets and data remain protected. By supporting zero-trust frameworks and enforcing identity-based access controls, network security provides a resilient foundation for modern and agile operations.
- Cost reduction. Cyberattacks can carry staggering financial consequences, from regulatory fines and legal fees to operational disruptions and reputational damage. By investing in strong network security, organizations reduce their exposure to these risks and avoid the costs of a breach. Proactive protection not only limits direct losses but also minimizes the potential for long-term financial setbacks that could affect growth and stakeholder confidence.
- Enhanced visibility and control. Network security provides organizations with greater visibility and control over their digital environment. By consolidating monitoring across endpoints, traffic flows and user behaviors, security teams gain the insights needed to detect anomalies early and act decisively. This proactive stance improves incident response times and also supports informed decision-making, helping organizations stay resilient in the face of evolving cyberthreats.
Challenges of network security
Maintaining network security involves a number of challenges, including the following:
- Evolving network attack methods. The biggest network security challenge is the rate at which cyberattacks evolve. Threat actors and their methods constantly change as technology changes. For example, new technology, such as blockchain, has led to new types of malware attacks, such as cryptojacking. As a result, network security defense strategies must adapt to these new threats.
- User adherence. As mentioned, security is every network user's responsibility. It can be difficult for organizations to ensure that everyone is adhering to network security best practices while simultaneously evolving those strategies to address the newest threats.
- Remote and mobile access. More companies are adopting bring your own device policies, which means a more distributed and complex network of devices for organizations to protect. Remote work is also more prevalent. This makes wireless security more important, as users are more likely to be using a personal or public network when accessing company networks.
- Third-party partners. Cloud providers, managed security services and security product vendors often get access to an organization's network, opening new potential vulnerabilities.
- Insider threats. These issues originate from individuals who already have authorized access to systems and data within an organization. Whether it's a disgruntled employee acting maliciously or a well-meaning staff member making a careless mistake, insider threats often bypass traditional security controls. Detecting and mitigating insider risks requires a nuanced approach that combines behavioral monitoring, strict access controls and a culture of security awareness throughout the organization.
- Limited security budgets. Budget constraints can significantly hinder an organization's ability to maintain strong network security. When financial resources are limited, it often means delaying critical upgrades, falling behind on patch management or operating without the full staffing needed for threat detection and incident response. These limitations create gaps that attackers can exploit, making it important for organizations to prioritize security investments strategically, even in tight fiscal environments.
- Misconfigurations and human error. Misconfigurations and human error continue to be among the leading causes of security breaches. Whether it's an accidentally exposed port, overly permissive firewall rules or a missed software patch, even small oversights can have significant consequences. As networks scale and evolve, maintaining precise configurations becomes more challenging, making it important to implement automated validation tools, enforce strict change management procedures and cultivate a security-first mindset among teams.
- Alert fatigue and tool overload. Many organizations struggle with alert fatigue and tool overload, which can undermine even the most well-funded security efforts. When disparate security tools generate floods of alerts without context or correlation, security teams are left sifting through noise to identify real threats. This not only slows down response times but also increases the risk of missing critical indicators of compromise. Integrating and automating responses through platforms such as SOAR or XDR can help streamline operations and reduce burnout.
Network layers and security
Networks contain layers, as represented by the Open Systems Interconnection (OSI) model. Data passes through these layers as it travels among devices, and different cyberthreats target different layers. Therefore, each layer in the stack must be secured for the network to be considered secure.
This table matches the OSI levels to the corresponding type of network security.
| Layers (ISO 7498-1) | ISO 7498-2 Security Model |
| Application | Authentication |
| Presentation | Access control |
| Session | Nonrepudiation |
| Transport | Data integrity |
| Network | Confidentiality |
| Data Link | Assurance and availability |
| Physical | Notarization and signature |
Notice that the third layer from the bottom is called Network, but network security doesn't apply only to this layer. Every device in a computer network functions on multiple layers when processing information. Given that, each layer must be secure for the network to be considered secure. In other words, the word network in this definition of network security refers broadly to the corporate infrastructure as a whole, not just the network layer.
For example, some people might make the distinction between cloud security and network security. Cloud security includes application security and container security, which exist outside of the network layer of the OSI model. However, those cloud functions can still be considered part of the overall corporate network, and securing them is part of network security.
Enterprise network security tools
According to independent research by Informa TechTarget's SearchNetworking, the following is a curated list of enterprise network security tools, spanning firewalls, threat detection and cloud-native protection:
- Cato Networks. This is a cloud-native secure access service edge (SASE) platform that integrates software-defined wide area network (SD-WAN), ZTNA and threat prevention into a single global network.
- Check Point. Check Point offers comprehensive threat protection for on-premises, virtualized and cloud infrastructures.
- Cisco Secure Firewall. This tool includes access control, real-time monitoring, next-generation firewall features, advanced malware protection and strong integration with Cisco's broader security ecosystem.
- CrowdStrike Falcon. This is a cloud-native endpoint and XDR platform that uses AI to detect and respond to threats in real time.
- Darktrace Enterprise Immune System.This tool uses AI and machine learning (ML) to autonomously detect and respond to cyberthreats by modeling normal behavior and spotting anomalies.
- Fortinet FortiGate. This is a high-performance next-gen firewall with integrated SD-WAN and security fabric for unified threat management across the network.
- IBM QRadar. This SIEM platform collects, analyzes and correlates security event data to detect and respond to incidents efficiently.
- Microsoft Defender for Endpoint. This endpoint security platform is embedded in the Microsoft ecosystem to provide threat detection, vulnerability management and response capabilities.
- Nessus. Developed by Tenable, Nessus scans for vulnerabilities in operating systems, applications, network devices and cloud infrastructure.
- Palo Alto Networks. Palo Alto Networks combines its next-gen firewall with Prisma Access to deliver unified, cloud-native security that enforces zero-trust principles across on-premises, remote and cloud environments.
- SentinelOne Singularity. This is an autonomous endpoint security and XDR platform with AI-driven detection, automated remediation and rollback for advanced threats.
- Snort. This is a powerful open source IDS and IPS. Organizations of all sizes use Snort to monitor network traffic for suspicious activity and known attack patterns.
- SolarWinds NetFlow Traffic Analyzer. This network monitoring tool captures flow data to analyze traffic patterns, detect anomalies and optimize performance.
- Sophos XG Firewall. This firewall provides deep learning threat detection, synchronized security with endpoints and comprehensive network visibility.
- Splunk Enterprise Security. This scalable SIEM tool provides advanced analytics, threat correlation and incident investigation capabilities.
- Zscaler Zero Trust Exchange. This is a cloud-based zero-trust platform that securely connects users to apps while inspecting traffic inline for threats and data loss.
How to select a network security tool for your organization
According to the 2024 CDW cybersecurity research report, 68% of organizations said they use between 10 and 49 network security tools or platforms. Selecting the right network security tool requires aligning its technical capabilities with the organization's risk posture, infrastructure complexity and compliance requirements.
Organizations should consider the following items and features when selecting a network tool:
- Understand business needs. Selecting the right network security tool begins with a deep understanding of the organization's needs. Organizations should start by conducting a risk and vulnerability assessment to identify critical assets and potential attack vectors. It's important to understand regulatory and compliance obligations, which often dictate specific security requirements and auditing capabilities that the tools must support.
- Define key features. Once an organization defines its needs, it should outline the essential features the tool must include. These features might consist of core components, such as firewalls, IDS and IPS, encryption protocols, EDR and XDR, MFA and support for cloud environments and zero-trust architectures. Aligning features with specific threat models helps the organization avoid paying for unnecessary tools and ensures it doesn't overlook important security risks.
- Check scalability and integration. A tool that is effective for a 100-user environment might not perform well in larger, 10,000-user or multi-cloud deployments. Organizations should select tools that can grow alongside their business and integrate smoothly with existing IT infrastructure, including application programming interfaces, SIEM systems and third-party analytics tools. Strong integration helps minimize redundancy, reduce complexity and create a more unified and efficient security ecosystem.
- Evaluate threat intelligence and automation. Assessing a tool's ability to provide real-time threat intelligence and automate routine processes is essential for modern enterprises, especially those with lean security teams. The more a tool can adapt and respond autonomously, the less manual effort is required for ongoing security operations.
- Understand usability and management. Usability is often overlooked but is just as important as a tool's technical capability. Organizations should look for tools with intuitive interfaces, centralized dashboards and clear workflows. A tool that is overly complex or difficult to use can result in misconfigurations, delayed responses or user resistance, all of which can increase security risk.
- Do a vendor assessment. Vendor reputation and support structure are also important factors for organizations to consider. It's essential to investigate the vendor's history, financial stability and customer service track record. Organizations should ensure the vendor offers timely support, clear service-level agreements, regular updates and comprehensive training resources. Evaluating the vendor's development roadmap is also recommended to confirm that the product will evolve and meet future security requirements.
- Calculate total cost of ownership (TCO). Cost considerations for an organization should extend beyond the initial purchase price. It's important to evaluate the TCO, which includes licensing fees, hardware requirements, implementation, training, updates and ongoing maintenance. Organizations should factor in the potential cost of a security breach if the tool fails to perform effectively. Balancing overall cost with the level of protection and long-term value is essential for sustainable success.
- Proof of concept (PoC) or trial. Before making a final purchase, organizations should request a PoC or trial deployment. This provides an opportunity to test the tool within their own environment, simulate potential threats, assess performance and collect feedback from internal users. This hands-on evaluation helps reveal practical strengths or limitations that might not be apparent from vendor demonstrations or marketing materials.
- Check peer feedback and case studies. Peer feedback and case studies from similar organizations are valuable resources. Organizations should review industry-specific use cases and reviews and connect with reference customers. Gaining insight into how a tool performs in comparable environments can help determine whether it's a good cultural and operational fit.
- Plan deployment and maintenance. Once a decision is imminent, organizations should plan their deployment strategy carefully. This includes defining rollout phases, such as starting with a single site, department or function, and putting in place adequate monitoring, training and change management practices. After deployment, the organization's team must be prepared to manage updates, incident response and ongoing system optimization.
- Document the decision. Organizations should document every step of the decision-making process. This documentation should include evaluation criteria, feature comparisons, trial results, vendor assessments, return on investment estimates and compliance evaluations. Doing so not only promotes internal accountability and transparency but also provides valuable reference material for future reviews, audits and system upgrades.
Network security best practices
Network security is crucial for protecting organizational data and systems from unauthorized access and cyberthreats. The following are the key best practices organizations should follow to maintain strong network security:
- Build layered defenses. Organizations should build overlapping security controls across the network, endpoint and application layers. This ensures that if one control fails, others still offer protection, creating resilience against sophisticated attacks.
- Embrace zero-trust. In line with the zero-trust principle of "never trust, always verify," organizations should continuously authenticate users and devices, enforce least-privilege access and segment networks to minimize lateral movement.
- Secure access rigorously. Organizations should adopt MFA, create strong password policies and implement role-based access controls, complemented by privileged access management for high-level accounts.
- Keep systems updated. Since vulnerabilities are a favored entry point for attackers, organizations should automate patch management across software, firmware and network devices.
- Monitor and audit frequently. Organizations should continuously monitor network traffic. To do this, they can use SIEM or network detection and response tools, establish alerts to flag suspicious activity and conduct routine audits, penetration tests and vulnerability scans to maintain network security.
- Train and empower employees. Organizations should raise awareness about social engineering and phishing threats. They can do this by implementing training programs, simulated phishing campaigns and interactive learning initiatives that encourage a culture of cybersecurity mindfulness.
- Prepare for incidents. Organizations establish clearly defined protocols, including assigned roles, designated communication channels, detailed response playbooks and structured recovery steps. This incident response plan should be tested and updated regularly to ensure it's effective and aligned with evolving threats and organizational changes.
- Automate intelligent detection. Organizations should deploy AI and ML-based tools to enable proactive threat detection, automate incident response processes and integrate actionable threat intelligence to adapt to evolving cyber-risks.
- Segment networks and control access. Organizations should divide their networks into separate zones and implement network access control to manage and restrict access. This segmentation helps limit exposure and prevents attackers from moving laterally across the network, thereby containing potential breaches and minimizing damage.
- Secure cloud, IoT and emerging environments. Organizations should adopt cloud-native security approaches, including cloud access security brokers, container security measures and the SASE framework. They should use encryption and continuous monitoring across all environments to ensure comprehensive protection of data and infrastructure.
- Plan for future threats. Organizations should proactively plan for future threats by beginning the transition to post-quantum cryptography and preparing for emerging risks.
Network security jobs and certifications
Jobs related to network security include the following:
- Chief information security officer. CISOs are one of the highest-paying positions in network security. They're responsible for developing and implementing an overall information security program.
- Penetration tester. Pen testers are hired to break into a corporate network to expose vulnerabilities. This can be automated or performed manually by employees or through pen testing as a service from third-party providers.
- Security engineer. These professionals focus on quality control within the IT infrastructure.
- Security architect. These people plan, analyze, design and test an organization's IT infrastructure.
- Security analyst. These experts analyze and plan security strategy, as well as perform security audits.
- Cloud security specialist. These security pros secure cloud environments and protect the cloud-based systems, data and infrastructure from cyberthreats.
- Cybersecurity architect. These security pros design, build and oversee the implementation of secure systems and networks to protect an organization's digital assets from threats.
- Security operations center analyst. These analysts monitor security alerts from various sources, triage incidents and perform initial investigations.
Some certifications for careers in network security include the following:
- CompTIA CySA+. This is a midlevel certification for cybersecurity analysts focused on behavioral detection, threat intelligence, vulnerability management and incident response.
- CompTIA Security+. This entry-level credential validates core cybersecurity knowledge and practical skills, such as threat identification, risk management, network architecture, cryptography and incident response.
- EC-Council's Certified Ethical Hacker. The CEH credential is focused on hacking techniques and penetration testing and teaches attackers' mindset, tools and methodologies.
- Global Information Assurance Certification Security Essentials. GSEC is an entry-level to midlevel certification for hands-on security professionals. It covers real-world topics, such as access control, cryptography, network security, risk management and log analysis.
- ISACA's Certified Information Security Manager. The CISM certification is a management-level credential for professionals who design, oversee and assess enterprise information security programs.
- ISACA's Certified Information Systems Auditor. CISA is a management- and assurance-level certification for professionals who audit, control and monitor information systems.
- ISC2 Certified Cloud Security Professional. CCSP is an advanced credential for cloud security professionals. It covers architecture, data protection, cloud infrastructure security and compliance across major cloud providers.
- ISC2 Certified Information Systems Security Professional. CISSP is an advanced-level certification covering a range of security domains, such as access control, cryptography, risk management, security operations and architecture. It's designed for experienced practitioners and leaders in cybersecurity.
- OffSec Certified Professional. OSCP is a technical, hands-on certification from Offensive Security focused on penetration testing using Kali Linux. It requires successfully hacking into live lab machines and completing a 24-hour exam.
Network security is fundamental to a strong cybersecurity strategy. Read more about the best cloud security certifications and the steps to map a successful cybersecurity career.







