
Spartak - Fotolia
Best practices to overcome an IoT security challenge
The internet of things poses numerous security challenges, but with the proper preparation and tools, your enterprise can mitigate the threats.
The internet of things is affecting your enterprise this very moment, whether you're aware of it or not. If you play a role in IT or security, it's incumbent on you and your team to ensure the safe collection, management and disposition of information assets as they relate to your IoT environment -- and that includes knowing what's on your network. It sounds a bit simplistic, but the reality for businesses large and small is that you can't secure the things that you don't acknowledge or don't even know are there. Even if you believe IoT devices aren't on your network, odds are good that there's something there that needs to be addressed in some way.
The biggest enterprise IoT security challenge is knowing what's what. Smart lightbulbs, a connected HVAC system, a connected security camera or even the Fitbit on an employee's wrist -- IoT can consist of everything from sensors and actuators to physical security devices and building control systems to more niche systems that serve a medical or financial purpose.
Anything with an IP address or URL that's connected to your network could be an IoT device. Why is this a big deal? IoT systems often interact with critical network systems and can tie into core business processes. Some of them take in, process and store sensitive data, such as personally identifiable information and intellectual property. IoT systems are network-accessible -- and sometimes internet-accessible -- which means they could be used against you and your business if they're not properly controlled. What makes IoT devices unique in the context of security is that they often fall outside of traditional requirements for analysis, development and oversight. This can create serious security risks if not addressed.
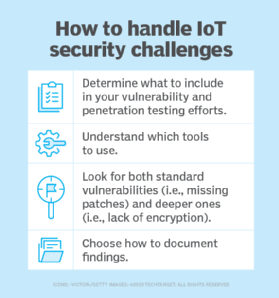
Another top enterprise IoT security challenge is uncovering specific vulnerabilities. Many things must be considered to ensure you're looking for -- and uncovering -- the security flaws that matter, such as the following:
- What to include in your ongoing vulnerability and penetration testing. It could be that IoT systems are simply part of your traditional testing of all network systems. Or, perhaps, you need to test them separately -- and gingerly -- as they're often not as resilient as traditional network hosts like servers, workstations and network infrastructure systems.
- Which tools need to be used. I've found that traditional security testing tools work well, including Nessus and Netsparker for host and web vulnerability scanning and CommView, CommView for WiFi and Wireshark for network communications analysis. I've also found tools such as NetScanTools Pro, Nmap and Shodan work well for additional system discovery and fingerprinting that other tools can overlook given how some IoT system TCP/IP stacks work.
- Vulnerabilities to watch out for. These include the standard vulnerabilities of missing patches and weak passwords, but dig in deeper and ensure that IoT systems are using Transport Layer Security to encrypt communication sessions and encrypt data at rest, as well as making sure devices are not susceptible to denial-of-service attacks. The OWASP Internet of Things Project is a great reference here.
- How you'll document your findings. Will IoT systems be lumped in with your traditional vulnerability and penetration testing findings? Or will there be a dedicated report? How will the reporting be communicated? And who will be responsible for remediation efforts?
Another IoT security challenge is integrating the systems within your existing security standards, policies and controls. Your documentation may say that all systems must meet minimum requirements around passwords, logging and alerting, backups and so on. That means nothing -- and can actually create liabilities -- if some or all of your IoT systems can't support these features or otherwise easily integrate into your security program. Consider the following:
- You may need new security standards that can embrace and enable your IoT system capabilities.
- You'll need to add IoT into the scope of some, if not all, of your security policies. Your specific procedures and even plans for incident response and disaster recovery and business continuity will likely need to be updated, especially for IoT systems that play a critical role in your environment or may otherwise pose risks.
- Ongoing oversight is a must, and monitoring, logging and alerting need to be taking place. I've found that traditional security information and event management systems can work with some tweaking, but there are tools dedicated to IoT that can take the pain out of the process.
- You may need to factor IoT systems into your compliance efforts, especially as they relate to personally identifiable information. Regulations such as the Health Insurance Portability and Accountability Act, GDPR and the Gramm-Leach-Bliley Act will likely fall under this umbrella.
An ethical hacker explores IoT insecurities.
Probably the biggest unknown IoT security challenge, and greatest area of scrutiny for the enterprise, is that we often don't know what such systems are doing -- or are capable of doing -- on the network. Compounding the paranoia, many IoT vendors aren't very forthcoming with such information. I'm working on an IoT device security assessment project as I write this. The vendor wants to ensure that its product and associated application environment are secure, and rightly so. An even bigger concern is on the part of the end customers, in terms of how sensitive records, such as personally identifiable information, are being stored and managed, as well as what else IoT devices are doing on the network. These are IoT concerns that must be addressed both now and ongoing in the future, and the reason why standards bodies, such as NIST and the Institute of Electrical and Electronics Engineers, are getting involved.
You, your executives and your business as a whole are ultimately responsible for vendor security issues. Even if every IoT security challenge is brought about and must be resolved by the vendors themselves, it's still up to you to figure out how to address the existing security issues in your specific environment. Do what you can to further improve those efforts. Treat IoT devices as a new influx of systems posing unknown risks that must be secured, because that's exactly what they are.







