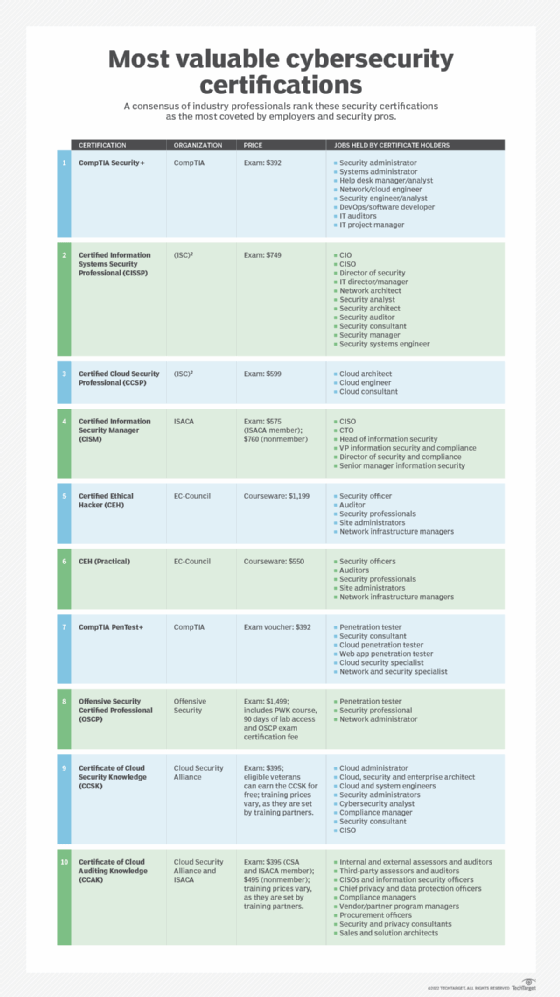
10 cybersecurity certifications to boost your career in 2025
A consensus of industry professionals rank these 10 security certifications as the most coveted by employers and security pros -- plus links to 10 vendor security certifications.
Cybersecurity remains one of the enterprise's highest priorities in 2025 as companies continue to balance in-office and remote work. And, with cyberattacks continuing at a breakneck pace, the demand for cybersecurity experts shows no signs of slowing. Data from Cyberseek indicated that there were 457,000 cybersecurity job openings just in the U.S. in January 2025.
For those looking to advance their cybersecurity careers or break into the field, cybersecurity certifications can help land jobs, boost careers or ensure against a job loss -- provided you choose wisely. Our guide provides insight into the following 10 cybersecurity certifications deemed most valuable for aspiring and seasoned cybersecurity professionals:
- CompTIA Security+.
- ISC2 Certified Information Systems Security Professional (CISSP).
- ISC2 Certified Cloud Security Professional (CCSP).
- ISACA Certified Information Security Manager (CISM).
- EC-Council Certified Ethical Hacker (CEH).
- EC-Council CEH (Practical).
- CompTIA PenTest+.
- Offensive Security Certified Professional (OSCP).
- Cloud Security Alliance (CSA) Certificate of Cloud Security Knowledge (CCSK).
- Cloud Security Alliance (CSA) Certificate of Cloud Auditing Knowledge (CCAK).
In building this list of the top 10 cybersecurity certifications, we talked to a broad range of people in the security industry. We heard from course providers and consultants; talked with a professor from University of Maryland Global Campus; sought advice from security providers, such as Cisco and Fortinet; and contacted leading trade groups and certification providers, including CSA, CompTIA, EC-Council, ISACA, ISC2, Information Systems Security Association International, Global Knowledge and Offensive Security.
Our list starts off with basic, entry-level and management-track certifications, then moves on to the offensive security certifications for hands-on penetration testers and certified ethical hackers. We end with a section that provides a list of 10 top vendor-specific certifications. Security professionals typically need a mix of all three types of certifications: management training, hands-on and vendor/product-specific knowledge.
CompTIA Security+
Most security pros say IT support technicians and admins -- and people looking to get into the security field -- should start with the CompTIA Security+ certification.
Upon completing the Security+ certification, students will have the skills and knowledge required to install and configure systems used to secure networks, applications and mobile devices. They will also be prepared to do the following:
- Assess the security posture of an enterprise environment, then recommend and implement appropriate security solutions.
- Monitor and secure hybrid environments, including cloud, mobile and IoT.
- Operate with an awareness of applicable laws and policies, including principles of governance, risk and compliance.
- Identify, analyze and respond to security events and incidents.
The exam consists of 90 multiple-choice and performance-based questions. Students have 90 minutes to complete the exam, which focuses heavily on performance-based questions. This emphasis ensures trainees can troubleshoot quickly and accurately. Passing the exam requires a score of at least 750 on a scale of 100-900.
Price
- Exam voucher: $392.
- Basic Bundle: $565 (includes exam voucher, one test retake and The Official CompTIA Security+ Study Guide e-book).
- Exam Prep Bundle: $720 (includes exam voucher, one test retake, The Official CompTIA Security+ Study Guide e-book and a 12-month individual license for CertMaster Practice for Security+, a knowledge assessment and certification training companion tool).
- E-learning Bundle: $977 (includes exam voucher, one test retake, a 12-month individual license for CertMaster Learn for Security+, which is a collection of interactive and self-paced instructional lessons with assessments, and a 12-month individual license for CertMaster Labs for Security+).
Jobs held by CompTIA Security+ holders
- Security administrator.
- Systems administrator.
- Help desk manager/analyst.
- Network/cloud engineer.
- Security engineer/analyst.
- DevOps/software developer.
- IT auditor.
- IT project manager.
ISC2 Certified Information Systems Security Professional (CISSP)
The ISC2 CISSP certificate is aimed at people with some hands-on experience in the field and is considered mandatory for career advancement. Few CISOs or upper-level security executives haven't completed it. First offered in 1994, CISSP is administered by ISC2. To qualify for the CISSP, candidates must pass the exam and have at least five years of cumulative paid work experience in two or more of the eight domains of the ISC2 CISSP Common Body of Knowledge (CBK).
The eight domains in the CBK are security and risk management; asset security; security architecture and engineering; communication and network security; identity and access management; security assessment and testing; security operations; and software development security. The exam evaluates expertise across these eight security domains. Passing the exam proves the student has the advanced knowledge and technical skills to effectively design, implement and manage a best-in-class cybersecurity program. The English CISSP Computerized Adaptive Testing (CAT) exam runs four hours long and consists of 125-175 questions. Students need a score of 700 out of 1,000 to pass. The certification remains valid for three years. The average salary for CISSPs is $92,639 globally and $120,552 in North America.
Price
- Exam: $749.
- Online, self-paced course: starts at $941.
Jobs held by CISSPs
- CIO.
- CISO.
- Director of security.
- IT director/manager.
- Network architect.
- Security analyst.
- Security architect.
- Security auditor.
- Security consultant.
- Security manager.
- Security systems engineer.
ISC2 Certified Cloud Security Professional (CCSP)
The ISC2 CCSP has become one of the leading cloud security certifications in the industry and is one of the hottest certifications on the market today. The CCSP recognizes IT and information security (infosec) leaders who have the knowledge and competency to apply best practices to cloud security architecture, design, operations and service orchestration.
To qualify for the CCSP, candidates must pass the exam and have at least five years of cumulative paid work experience in information technology, of which three years must be in information security and one year in one or more of the six domains of the ISC2 CCSP CBK. Students can substitute the ISC2 CISSP credential for the entire CCSP experience requirement.
The six domains in the CCSP CBK are cloud concepts, architecture and design; cloud data security; cloud platform and infrastructure security; cloud application security; cloud security operations; and legal, risk and compliance. The English and Japanese CCSP Computerized Adaptive Testing exam runs four hours and consists of 150 questions. Candidates need a score of 700 out of 1,000 to pass the exam. The certification remains valid for three years. The average salary for CCSPs is $80,717 globally and $114,172 in North America.
Price
- Exam: $599.
- CCSP online instructor-led training: $2,409.
- CCSP self-paced training: $836.
Jobs held by CCSPs
- Cloud architect.
- Cloud engineer.
- Cloud consultant.
- Cloud administrator.
- Cloud security analyst.
- Cloud specialist.
- Auditor of cloud computing services.
- Professional cloud developer.
ISACA Certified Information Security Manager (CISM)
Launched in 2002 by ISACA, CISM attracts professionals with technical expertise and experience in infosec/IT security and control who want to make the move from team member to management. CISM promises to add credibility and confidence to the candidate's interactions with internal and external stakeholders, peers and regulators by dramatically improving security knowledge and skills.
The CISM exam tests IT professionals and validates their expertise and experience in the following domains: information security governance; information security risk management; information security program development and management; and information security incident management.
CISM focuses on people already working in IT or infosec in some capacity who want to gain more knowledge to advance their careers. Eligibility for the test requires five or more years of experience in infosec management; experience waivers are available for a maximum of two years only. The exam consists of 150 multiple-choice questions that cover the exam content outline created from the most recent content analysis. The exam content outline was last updated and is effective as of June 1, 2022. Students have up to four hours to complete the exam. CISM certification holders can earn an estimated salary in the U.S. of $137,000 to $148,622.
Price
- Exam: $575 for ISACA members; $760 for nonmembers.
- CISM Review Questions, Answers & Explanations Database (12-month online subscription): $299 for ISACA members; $399 for nonmembers.
- CISM Online Review Course (self-paced): $795 for ISACA members; $895 for nonmembers.
- CISM Review Questions, Answers & Explanations Manual, 10th Edition (print, available in multiple languages): $120 for ISACA members; $156 for nonmembers.
- CISM Review Manual, 16th Edition (available in print and e-book): $109 for ISACA members; $139 for nonmembers.
Jobs held by CISMs
- CISO.
- CTO.
- Head of information security.
- Vice president of information security and compliance.
- Director of security and compliance.
- Senior manager of information security.
EC-Council Certified Ethical Hacker (CEH)
A CEH understands and knows how to look for weaknesses and vulnerabilities in target systems and uses the same knowledge and tools as a malicious hacker but in a lawful and legitimate manner to assess a target's security posture. The CEH credential, offered by EC-Council, certifies people in the specific network security discipline of ethical hacking from a vendor-neutral perspective.
The CEH credential was developed to establish and govern minimum credentials standards for professional information security specialists in ethical hacking; to inform the public that these credentialed individuals meet or exceed minimum standards; and to reinforce ethical hacking as a unique and self-regulating profession. Applicants must have two years of provable work experience in the security field to qualify. The exam runs four hours and consists of 125 multiple-choice questions.
Price
- CEH Exam: $1,199.
- On-demand training: $2,199.
- Unlimited on-demand: $2,999.
- Live training: $3,499.
Jobs held by CEHs
- Security officer.
- Auditor.
- Security professional.
- Site administrator.
- Network infrastructure manager.
EC-Council CEH (Practical)
The CEH (Practical) certification consists of a six-hour exam that requires students to demonstrate the application of ethical hacking techniques to solve a security audit challenge. Skills tested include threat vector identification, network scanning, OS detection, vulnerability analysis, system hacking and web app hacking. Students typically take this exam after they have attained the CEH certificate.
Students are given limited time, just like in the real world. The exam was developed by a panel of experienced subject matter experts and includes 20 real-life scenarios with questions designed to validate essential skills required in the ethical hacking domains as outlined in the CEH program. It's not a simulated exam; rather, it mimics a real corporate network through the use of live VMs, networks and applications designed to test skills. Students are presented with scenarios and asked to demonstrate the application of the knowledge acquired in the CEH course to find solutions to real-life challenges. Students pass with a score of 70% and above.
CEH (Practical) certificate holders have mastered the following skills:
- Understanding attack vectors.
- Performing network scanning to identify live and vulnerable machines in a network.
- Performing OS banner-grabbing, service and user enumeration.
- Performing system hacking, steganography and steganalysis attacks, as well as covering tracks.
- Identifying and using viruses, computer worms and malware to exploit systems.
- Performing packet sniffing.
- Conducting a variety of web server and web application attacks, including directory traversal, parameter tampering and cross-site scripting attacks.
- Performing SQL injection attacks.
- Performing different types of cryptography attacks.
- Performing vulnerability analysis to identify security loopholes in the target organization's network, communication infrastructure, end systems, etc.
Price
- Exam: $550.
- Fee includes a single CEH (Practical) Aspen Dashboard code. Upon activation, the Aspen Dashboard access lasts for 365 days, which means students can schedule an exam anytime within this period. The dashboard code is valid for one year from date of receipt, which means students must activate the code within one year or it expires. The fee also includes accommodation of remote proctoring services -- booking a slot needs to be completed three days prior the exam date -- and the CEH cyber range challenge exam.
Jobs held by CEH (Practical) holders
- Security officer.
- Auditor.
- Security professional.
- Site administrator.
- Network infrastructure manager.
CompTIA PenTest+
Students who have completed CompTIA Security+ and have three to four years of practical experience are good candidates for CompTIA PenTest+. This test assesses the most up-to-date penetration testing and vulnerability assessment and management skills required to determine the resiliency of the network against attacks. The test verifies students can plan and scope an assessment; understand legal and compliance requirements; perform vulnerability scanning and pen testing; analyze data; and effectively report and communicate results. The test has a maximum of 85 questions and takes 165 minutes. The passing score is 750 on a scale of 100-900.
Price
- Exam voucher: $392.
- Basic Bundle: $565 (includes exam voucher, one test retake and The Official CompTIA PenTest+ Study Guide e-book).
- Exam Prep Bundle: $720 (includes exam voucher, one test retake, The Official CompTIA PenTest+ Study Guide e-book and a 12-month individual license for CertMaster Practice for PenTest+, a knowledge assessment and certification training companion tool).
- E-learning Bundle: $977 (includes exam voucher, one test retake and a 12-month individual license for CertMaster Learn for PenTest+).
Jobs held by CompTIA PenTest+ holders
- Penetration tester.
- Security consultant.
- Cloud penetration tester.
- Web app penetration tester.
- Cloud security specialist.
- Network and security specialist.
Offensive Security Certified Professional (OSCP)
The OSCP exam and certification has been widely regarded as the "gold standard" for penetration testing career development. Students must prepare for the exam by going through an intensive prep course and practicing real-world skills in hands-on labs. The OSCP exam has a 23-hour, 45-minute time limit and consists of a simulated penetration test in one of Offensive Security's isolated VPN networks. Candidates receive the exam and connectivity instructions for an isolated network for which they have no prior knowledge of or exposure to. Points are awarded for each compromised host, based on its difficulty and level of access obtained.
Certified OSCPs can identify existing vulnerabilities and execute organized attacks in a controlled and focused manner. They can use or modify existing exploit code to their advantage, perform network pivoting and data exfiltration, and compromise systems that are poorly configured. By earning the OSCP certification, certification holders demonstrate persistence and critical thinking. The OSCP certification also shows certification holders can think outside the box while managing both time and resources.
Price
- Penetration Testing with Kali Linux (PWK) course with 90 days of lab access and OSCP exam certification: $1,499.
- Learn One Subscription: PWK course with 365 days lab access and two OSCP exam attempts: $2,499.
- OSCP certification exam retake fee: $249.
Jobs held by OSCPs
- Penetration tester.
- Security professional.
- Network administrator.
CSA Certificate of Cloud Security Knowledge (CCSK)
Released in 2011 by CSA, the CCSK course is roughly a 70-30 split between tactical (technical) and strategic (business-driven) subject matter around cloud security. Students must complete the open-book online exam in 90 minutes. The test consists of 60 multiple-choice questions selected randomly from the CCSK question pool, and students must score at least an 80% to pass. The subject matter covers the 14 domains of the CSA Security Guidance, the Cloud Controls Matrix and the ENISA Risk Assessment paper.
In completing the CCSK, students will gain the following benefits:
- Proven competency in key cloud security issues from an organization that specializes in cloud research.
- Increased employment opportunities by filling the skills gap for cloud-certified professionals.
- Demonstrated technical knowledge, skills and abilities to effectively use controls tailored to the cloud.
- Ability to establish a baseline of security best practices when dealing with a broad array of responsibilities, from cloud governance to configuring technical security controls.
The CCSK exam body of knowledge includes the CSA Security Guidance v4.0, CSA Cloud Controls Matrix and EU Agency for Cybersecurity Cloud Computing Risk Assessment reports.
Price
- Exam: $395 for first two attempts (eligible veterans can earn their CCSK for free).
- Training prices vary, as they are set by training partners.
Jobs held by CCSKs
- Cloud administrator.
- Cloud, security and enterprise architect.
- Cloud and system engineer.
- Security administrator.
- Cybersecurity analyst.
- Compliance manager.
- Security consultant.
- CISO.
CSA Certificate of Cloud Auditing Knowledge (CCAK)
The CCAK, released in 2021, is the industry's first global, vendor-neutral, technical credential for auditing in the cloud environment. Developed by CSA and ISACA, the CCAK credential builds on the body of knowledge covered in CSA's CCSK exam and complements ISACA's ANSI-accredited certifications, including the Certified Information Systems Auditor. The two-hour, online proctored exam consists of 76 multiple-choice questions. Students must score at least a 70% to pass. Prior experience in IT audit, security, risk or cloud computing is essential to pass the CCAK exam.
In completing the CCAK, students will accomplish the following:
- Understanding the difference in assessing and auditing cloud environments versus traditional IT infrastructure and services.
- Discovering how to use cloud security assessment methods and techniques to evaluate a cloud service prior to/during the provision of the service.
- Learning how existing governance policies and frameworks are affected by the introduction of cloud into the ecosystem.
- Understanding the unique requirements of compliance in the cloud due to shared responsibility between cloud providers and customers.
- Learning how to use a cloud-specific security controls framework to ensure security within the organization.
- Architecting in a way that enables a security pro to measure control effectiveness through metrics and ultimately leads to continuous monitoring.
Price
- Exam: $395 for CSA and ISACA members; $495 for nonmembers.
- Training prices vary, as they are set by training partners.
Jobs held by CCAKs
- Internal and external assessors and auditors.
- Third-party assessors and auditors.
- CISOs and information security officers.
- Chief privacy and data protection officers.
- Compliance managers.
- Vendor/partner program managers.
- Procurement officers.
- Security and privacy consultants.
- Sales and solution architects.
Demand for cybersecurity pros still outstrips supply
The ISC2 "2024 Cybersecurity Workforce Study" found that 67% of respondents concluded that their security had a staff shortage, and 58% of respondents believed the inability to find the right people for security positions had put their organizations at significant risk.
Those looking to advance their security careers or break into the field should be encouraged. The industry continues to need millions of good people who are not afraid of hard work, enjoy problem-solving and can handle the day-to-day pressures of working in a cybersecurity situation.
Vendor-specific security certifications
While many security vendors have training programs to comb through, it boils down to the products used by the organization, staff expertise and whether it makes sense to spend the time and money on the training.
Here's a list of 10 leading vendor security certifications with links to course details, pricing and information on the broad range of certifications many of these vendors offer:
- AWS Certification.
- Cisco Certified Network Associate.
- Fortinet Network Security Expert.
- Google Cloud certifications.
- IBM Cybersecurity Analyst Professional.
- Microsoft Certified: Azure Fundamentals.
- Okta Certified Professional.
- Oracle Cloud Infrastructure.
- Recorded Future Certified Analyst Lab.
- SonicWall Technical Certification Training.
Editor's note: This article was updated in January 2025 to reflect changes in the cybersecurity workforce.
Steve Zurier is an independent freelance technology writer covering IT security, networking and cloud computing.







