What is blockchain? Definition, examples and how it works
Blockchain is a distributed ledger technology (DLT) that's shared across a network of computers to keep a digital record of transactions. Blockchain is known for its role in cryptocurrency systems where it maintains a secure and decentralized record of transactions. However, its applications extend beyond cryptocurrencies to various fields, including supply chain management, healthcare and finance.
Each computer in a blockchain network maintains a copy of the ledger where transactions are recorded to prevent a single point of failure. All copies of the blockchain are updated and validated simultaneously.
Blockchain is also considered a type of database, but it differs from conventional databases in how it stores and manages information. Instead of storing data in rows, columns, tables and files as traditional databases do, a blockchain stores data in blocks that are digitally chained together. It's a decentralized database managed by computers belonging to a peer-to-peer network instead of a central computer such as in traditional databases.
Blockchains offer a secure, transparent and efficient way to manage and verify data across diverse industries. Bitcoin, launched in 2009 on the bitcoin blockchain, was the first cryptocurrency and popular application to successfully use blockchain. As a result, blockchain has been most often associated with bitcoin and alternatives such as dogecoin and bitcoin cash, both of which use their own public ledgers.
Types of blockchain
There are four main types of blockchain:
- Private blockchain. Private, or permissioned, blockchains restrict access to a select group of participants and require approval to access. These blockchains offer enhanced privacy and control over data, making them suitable for applications that require strict access controls and compliance with regulations. In a private, permissioned blockchain, such as multichain, every node might be able to perform transactions, but participation in the consensus process is restricted to a limited number of approved nodes.
- Public blockchain. Public, or permissionless, blockchains don't require permission to enter the blockchain network. In a public, permissionless blockchain like bitcoin, anyone can view the transactions and actively participate in the network. These blockchains are highly decentralized, with no single entity controlling the network. Every node in a public blockchain network conducts transactions and participates in the consensus process.
- Hybrid blockchain. A hybrid blockchain combines the characteristics of permissioned and permissionless blockchains. A hybrid blockchain is set up by a single organization and consists of one public system on top of a private system, giving the organization access control over sensitive data.
- Consortium blockchain. Consortium, or federated, blockchain is a type of hybrid blockchain in which a group of organizations governs the blockchain. Consortium blockchains combine the benefits of decentralization and privacy, making them suitable for industries that require collaboration and trust among a select group of participants. However, the breach of just one member node can compromise its security.

How blockchain and distributed ledger technology work
Blockchain uses a multistep process that includes the following five steps:
- An authorized participant inputs a transaction, which must be authenticated by the technology.
- That action creates a block that represents the specific transaction or data.
- The block is sent to every computer node in the network.
- Authorized nodes validate transactions and add the block to the existing blockchain.
- The update is distributed across the network, which finalizes the transaction.
These steps take place in near real time and involve a range of elements. Nodes in public blockchain networks are referred to as miners; they're typically paid for this task -- often in processes called proof of work (PoW) or proof of stake (PoS) -- usually in the form of cryptocurrency.
A blockchain ledger consists of two types of records: individual transactions and blocks. The first block has a header and data that pertain to transactions taking place within a set time period. The block's timestamp is used to help create an alphanumeric string called a hash. After the first block has been created, each subsequent block in the ledger uses the previous block's hash to calculate its own hash.
Before a new block can be added to the chain, its authenticity must be verified by a computational process called validation or consensus. At this point in the blockchain process, a majority of nodes in the network must agree the new block's hash has been calculated correctly. Consensus ensures that all copies of the blockchain distributed ledger share the same state.
Once a block has been added, it can be referenced in subsequent blocks, but it can't be changed. If someone attempts to swap out a block, the hashes for previous and subsequent blocks will also change and disrupt the ledger's shared state.
When consensus is no longer possible, other computers in the network are aware that a problem has occurred, and no new blocks are added to the chain until the problem is solved. Typically, the block causing the error will be discarded and the consensus process will be repeated. This eliminates a single point of failure.
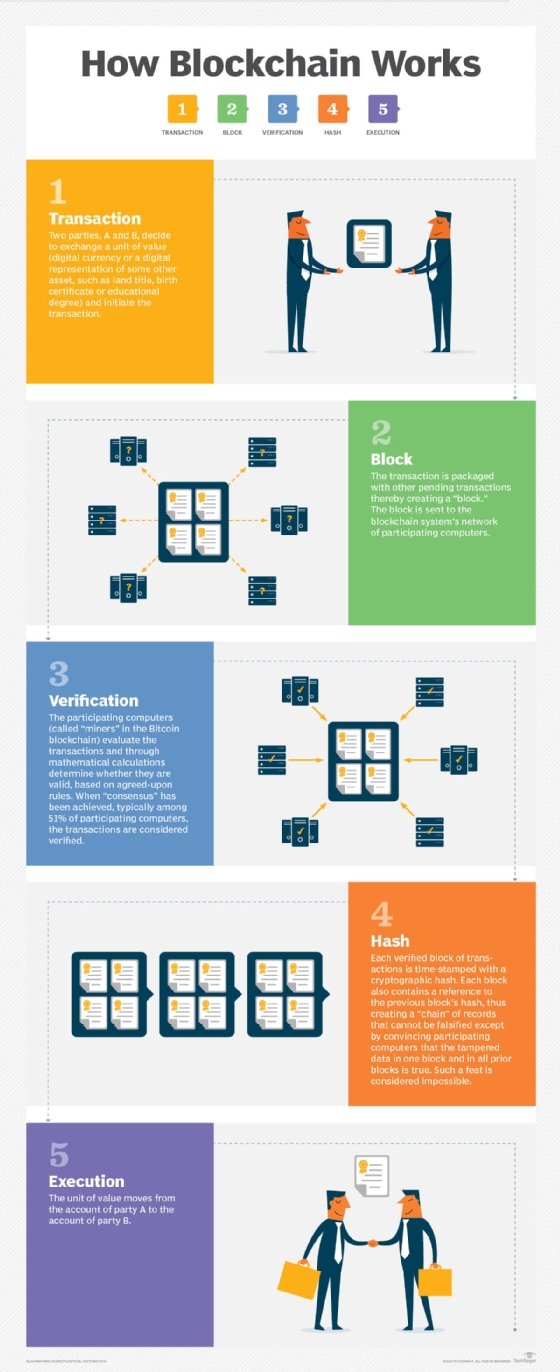
Key features of blockchain technology
Blockchain technology is built on a foundation of unique characteristics that differentiate it from traditional databases. The following are its most important and defining characteristics:
- Decentralization. Blockchain decentralization is one of the fundamental aspects of the technology. Unlike centralized databases where a central authority, such as a bank, controls and verifies transactions, blockchain operates on a distributed ledger. This means multiple transparent participants, known as nodes, maintain, verify and update the ledger. Each node is spread across a network and contains a copy of the whole blockchain.
- Immutability and security. Cryptographic algorithms are used in blockchain to provide strong security; they record transactions and make tampering nearly impossible. Information is stored in blocks that are linked together using cryptographic hashes. If someone tries to tamper or modify a block, they will have to change every subsequent block, making tampering computationally infeasible. This inherent blockchain security feature guarantees immutability of information and makes blockchain an ideal platform to store sensitive data and conduct secure transactions.
- Transparency and traceability. The inherent transparency of blockchain technology ensures every network participant has access to identical information. For instance, every transaction becomes part of a public ledger, visible to all participants. This transparency confirms trust and network accountability, because any inconsistency can be promptly recognized and resolved. Additionally, the blockchain's capacity to track the origin and trajectory of assets makes audits easier and decreases the likelihood of fraudulent activities.
- Smart contracts. These contracts are automated agreements that are encoded in software to automatically execute the stipulations of a contract. Smart contract codes are stored on the blockchain and carry out their functions once predetermined conditions are met. These contracts eliminate the need for intermediaries, streamline transactions, save money and speed up closing times. They're used in a range of diverse sectors, including supply chain management, insurance and finance.
- Consensus mechanisms. Blockchain networks employ consensus algorithms, including PoW and PoS, to verify transactions. These algorithms ensure all network nodes agree on the ledger's state, fostering trust and security among participants.
Blockchain, digital currency, cryptocurrency and Bitcoin explained
The terms blockchain, cryptocurrency and bitcoin are frequently lumped together, along with digital currency, and sometimes they're erroneously used interchangeably. Although they all fall under the umbrella of DLT, each is a distinct entity.
- Blockchain is the technology that digital currency, cryptocurrency and bitcoin are built on. More specifically, it's the underlying technology that constructs a decentralized digital ledger that enables exchanges among multiple parties in a secure, immutable manner.
- Digital currency refers to any form of currency available in digital or electronic form and shared without an intermediary. This includes digital money issued by governments and central banks, as well as cryptocurrency. Digital currency is sometimes called digital money, electronic money, electronic currency or cybercash.
- Cryptocurrency is a digital asset that can be exchanged on a blockchain network. It's a subset of digital currency that isn't issued by government entities. Think of cryptocurrency as tokens private entities or groups issue that can also pay for items sold by those who also operate in the blockchain network.
- Bitcoin is the first and most popular cryptocurrency. It was introduced by an anonymous person or group of people using the pseudonym Satoshi Nakamoto. Bitcoin operates on a decentralized network known as the bitcoin blockchain, which lets participants send and receive it without the need for intermediaries. New bitcoin is introduced to the supply through bitcoin mining, a process that requires significant computational power. Miners solve complex mathematical problems and the miner who solves the puzzle and validates the transaction is rewarded with new bitcoin.
Blockchain and smart contracts
Smart contracts are one of the most important features of blockchain technology. They are self-executing digital contracts written in code that operate automatically according to predefined rules and conditions. Smart contracts are designed to facilitate, verify and enforce the negotiation or performance of an agreement without the need for intermediaries, such as lawyers, banks or other third parties.
Once the smart contract's conditions are met, it automatically executes the agreed-upon actions or transactions in the contract. After the transaction is complete, the smart contract is permanently recorded on the blockchain, confirming its immutability so it can't be altered or deleted. Access to transaction details can be restricted so only authorized parties can view the results.
Smart contracts are typically deployed on blockchain platforms that provide the necessary security and transparency for their execution. Ethereum is a popular blockchain platform for smart contracts. It's used for a range of applications such as financial transactions, supply chain management, real estate deals and digital identity verification.
Smart contracts have several benefits. By eliminating intermediaries, smart contract technology reduces costs. It also cuts out complications and interference intermediaries can cause, speeding processes and enhancing security.
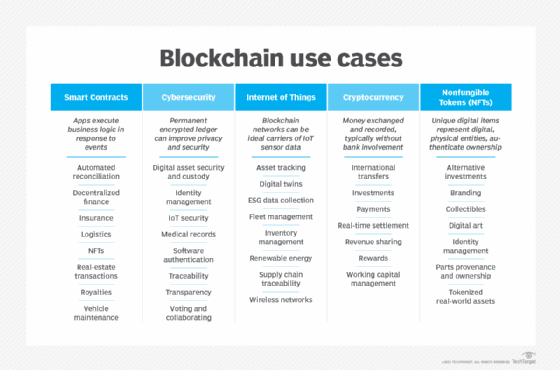
Additional blockchain examples and use cases
Blockchain continues to mature and gain acceptance as more companies across various industries learn to use it. Blockchain's use cases and industry applications have grown far outside its original cryptocurrency application to include smart contracts, cybersecurity, internet of things (IoT) and non-fungible tokens. NFTs are digital assets representing all or portions of real-world objects such as art or music. They're bought, sold and traded online, and they're a popular way to buy and sell digital artwork.
Some of blockchain technology's real-world applications include the following:
- Supply chain management. The end-to-end visibility, traceability and accountability of blockchain is useful in managing supply chains. Stakeholders can record, track and authenticate products, prevent counterfeit goods from getting into the supply chain and streamline logistics processes.
- Healthcare. Along with artificial intelligence (AI) and IoT, blockchain has emerged as an innovative healthcare technology. In healthcare, blockchain technology is used to securely store and share patient data. It lets patients control their medical records, granting access to healthcare providers only when necessary. This allows seamless and secure sharing of medical information, improving treatment outcomes and reducing administrative burdens.
- Identity management. Blockchain-based identity management systems enhance security, privacy and control over personal data. By storing identity information on the blockchain, users can have a portable and verifiable digital identity. This eliminates the need for multiple identity documents, reduces identity theft and simplifies identity verification processes.
- Voting systems. Blockchain technology can address the challenges of traditional voting systems by providing secure and transparent voting platforms. Voting systems based on the technology eliminate voter fraud, ensure the integrity of the electoral process and enable remote voting while maintaining anonymity and privacy.
- Finance and banking. Financial services use blockchain to accelerate transactions and speed up close times. Some banks also use blockchain for contract management and traceability purposes. For example, PayPal, the online payment platform, launched a blockchain-based service in 2020 that lets users buy, hold and sell cryptocurrency. R3, a global consortium of financial institutions, developed its Corda platform to record, manage and synchronize financial information using blockchain application programming interfaces for specific platforms.
- Media and entertainment. Blockchain technology expands royalty opportunities for companies and individuals. For instance, organizations can use blockchain to create digital tickets that allow them to collect royalties if the ticket is resold. In April 2021, Live Nation SAS, the France-based arm of the global entertainment company of the same name, launched TixTo.Me, powered in part by blockchain company Aventus Network.
- Property records. In property record management, blockchain provides a secure, transparent and immutable system for recording ownership and transactions. Property ownership data is stored on a blockchain, so that all transactions such as sales, transfers and liens are permanently recorded and accessible to authorized parties. This eliminates the need for physical documentation and guarantees records can't be altered without network consensus, reducing fraud. Blockchain also enables faster, more efficient transactions through smart contracts, automating processes such as title transfers and escrow.
- Logistics. Logistics companies use blockchain to track and trace goods as they move through the supply chain.
- Government central banks and global finance. Government central banks and the global finance community have transitioned to blockchain with the introduction of central bank digital currency (CBDC) as a foundation for currency exchange.
Organizations across various industries use blockchain-based applications as a secure and cost-effective way to create and manage a distributed database and to maintain records for all types of digital transactions. As a result, blockchain is increasingly viewed as a way of securely tracking and sharing data among multiple business entities.
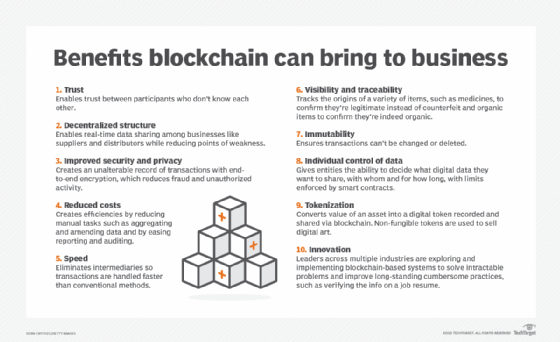
Advantages of blockchain
Experts cite several key benefits to using blockchain, including the following:
- Uncorruptible. It's almost impossible to corrupt a blockchain because millions of computers share and continually reconcile the information. Blockchain also has no single point of failure.
- Efficient. Transactions are often more efficient than in non-DLT-based transactional systems, though public blockchains can sometimes suffer from slow speed and inefficiency.
- Resilient. Blockchain is resilient; if one node goes down, all the other nodes have a copy of the ledger.
- Trustworthy. It provides trust among participants on a network. Confirmed blocks are difficult to reverse, which means data is difficult to remove or change.
- Cost-effective. It eliminates middlemen and third parties involved in transactions, reducing the costs associated with those transactions.
- Faster cross-border transactions. Blockchain technology expedites cross-border transactions through peer-to-peer transfers without intermediaries. In contrast, traditional methods often involve lengthy delays and complex procedures.
Disadvantages of blockchain
According to experts, blockchain also has the following potential drawbacks, risks and challenges:
- Ownership issues. Blockchain can raise questions about ownership and who's responsible when problems arise.
- Infrastructure issues. Questions also come up about whether organizations are willing and capable of investing in the infrastructure needed to build, participate and maintain a blockchain-based network.
- Data challenges. Changing data in a blockchain, should the need arise, would take a lot of work.
- Private keys. Users have to keep track of the private keys that give them access to their assets to avoid losing their money or other investments.
- Storage needs. The need for storage can grow to be very large over time, which risks the loss of nodes if the ledger becomes too large for users to download.
- Security vulnerabilities. Blockchain is susceptible to 51% attacks, which is a specific attack designed to overwhelm other participants in the network and change blocks. Other potential threats include phishing attacks, man-in-the-middle attacks and endpoint vulnerabilities.
- Slower performance. Blockchain typically isn't as fast as traditional databases because of the additional operations it performs. Factors such as cryptographic signature verification, reliance on consensus mechanisms and redundancy, where each node verifies and stores transactions, result in lower transaction throughput.
Leading blockchain platforms
According to Gartner reviews, examples of blockchain platforms include the following:
- Avalanche is a smart-contracts platform that lets users build decentralized apps, scale with minimal hardware and launch both private and public blockchains. The platform is also energy-efficient, offering CPU-optimal energy use that helps keep computers cool during operation.
- Chainalysis KYT is a compliance and risk management tool designed to help businesses and financial institutions monitor cryptocurrency transactions in real time. It uses advanced blockchain technology to spot risky and fraudulent activities, helping organizations stay compliant with regulations.
- Ethereum is a widely used, open source, custom-built blockchain platform. It's considered to be an industry-leading choice for enterprise applications. Ethereum enabled the development of smart contracts and decentralized applications, also known as dApps. It has gained significant popularity due to its range of features, flexibility and large developer community. Ethereum's native cryptocurrency, called ether, is used to compensate participants and power the platform.
- Hyperledger Fabric is used in industries such as finance and manufacturing. This open source blockchain platform is designed for permissioned networks, but it can also be used for decentralized hosting and storing applications that use smart contracts. It provides a modular framework to build private, permissionless blockchains tailored to specific business needs.
- IBM Blockchain is an enterprise tool built on the Hyperledger Fabric framework. It offers a secure and immutable ledger to record transactions and track assets. Restricting access and interaction with blockchain data to authorized users enhances the tool's efficiency and trust.
- OpenChain is an open source blockchain platform for organizations that want to manage and preserve digital assets. An administrator of an OpenChain blockchain defines the rules used in the ledger. Users can then exchange value on the ledger by adhering to the rules.
- Ripple is a digital payment network that enables fast and cost-effective cross-border transactions. Unlike traditional blockchains, it uses the Ripple Protocol Consensus Algorithm instead of mining; this lets designated servers validate transactions. Processing takes three to five seconds, and it handles up to 1,500 transactions per second, making it significantly faster than many cryptocurrencies.
Blockchain adoption considerations
Any enterprise considering whether to implement a blockchain application should first consider whether it needs blockchain to achieve its objectives. Blockchain has several significant benefits, particularly in security, but it doesn't cater to all database needs and there are other alternatives for businesses to consider.
Conventional, centralized databases are often the better option in many circumstances, especially when speed and performance are critical factors. They're also better when transactions only happen inside the enterprise or between a limited number of entities where trust has been fully established.
In choosing a blockchain platform, an organization should keep in mind which consensus algorithm to use. The consensus algorithm is a core piece of a blockchain network and one that can have a big effect on speed. It's the procedure through which the peers in a blockchain network reach agreement about the present state of the distributed ledger. This helps to establish trust among users of the blockchain.
There are a few standard methods that blockchain and other distributed database platforms use to arrive at a consensus. Common consensus algorithms include the following:
- PoW algorithms are used to select a miner for the next block generation.
- Practical Byzantine Fault Tolerance algorithms work in asynchronous systems.
- Delegated Byzantine Fault Tolerance algorithms provide security against fraud.
- PoS algorithms are commonly used as alternatives to PoW.
- Delegated PoS algorithms are used in voting and election processes. They protect against malicious use or centralization in the blockchain.
- Proof of authority algorithms are used in private consortium blockchains where trust is established among participants.
- Proof of elapsed time algorithms are used in permissioned blockchain networks. They rely on a trusted execution environment to ensure nodes wait for a random time before proposing a block. This promotes fairness in block creation.
When adopting blockchain technology, organizations should consider regulatory compliance requirements to ensure adherence to relevant laws and guidelines. Additionally, evaluating the costs of blockchain execution and maintenance, along with the user experience, is essential for encouraging adoption and maximizing its benefits.
Blockchain privacy and security
Privacy and security are major advantages of blockchain. Private data is stored in blocks. Blocks are always stored chronologically, and it's extremely difficult to change a block once it has been added to the end of the blockchain.
Each block has its own hash code that contains the hash code of the block that comes before it. If a hacker tries to edit a block or access its information, the block's hash will change, meaning the hacker would have to change every other block that comes after it, which would take a massive amount of computing power.
Blockchain technology is still susceptible to 51% attacks that can circumvent a consensus algorithm. With these attacks, an attacker has more than 50% control over all the computing power on a blockchain, giving them the ability to overwhelm the other participants on the network. This type of attack is unlikely, because it would take a large amount of effort and a lot of computing power to execute.
When adopting blockchain, organizations must weigh the pros and cons of choosing between public and private blockchains. Public blockchains such as bitcoin and ethereum offer transparency, but transactions are visible to anyone. Private blockchains provide more privacy, but the lack of transparency can raise trust issues among participants.
Protecting the data shared across the blockchain is also important because it involves distributing data across a decentralized network. Techniques including encryption and privacy-enhancing protocols help mitigate risks while ensuring compliance with data protection regulations.
Blockchain vs. centralized ledgers
Blockchain technology and centralized ledgers have several key differences, including the following:
- Control and ownership. Blockchain uses a shared and synchronized transaction record distributed across a network of computers. Its decentralized nature means no single entity controls the network. In contrast, a centralized ledger is a traditional system with a single source of truth stored in one location, such as on a desktop computer or in the cloud. A central authority, such as a bank or government agency, maintains control of the ledger.
- Trust and transparency. Blockchains, especially public ones, offer increased transparency by recording all transactions on a public ledger that's accessible to all participants. This transparency fosters trust among users because they can independently verify transactions without relying on a central authority. Centralized ledgers limit transparency, as users must trust the central authority to manage the data accurately. This reliance might lead to concerns about data integrity and potential misuse.
- Speed and efficiency. Blockchain transactions often take more time to process because consensus from multiple nodes is required. However, this tradeoff boosts security and reduces the risk of fraud. Centralized systems have streamlined control and fewer nodes involved in validation so they can process transactions faster, but this speed comes at the cost of security and trust.
- Use cases. Blockchain is commonly used in situations that demand high levels of transparency, security and decentralization, such as cryptocurrencies, supply chain management and identity verification. In contrast, centralized ledgers are used in traditional banking and business settings, where a trusted authority validates transactions and maintains records.
History of blockchain
The original idea for blockchain technology was considered decades ago. A protocol similar to blockchain was first proposed in a 1982 dissertation by David Chaum, an American computer scientist and cryptographer. In 1991, Stuart Haber and W. Scott Stornetta expanded on the original description of a chain of blocks secured through cryptography. From this point on, various individuals began working on developing digital currencies.
In 2008, a developer or group of developers working under the pseudonym Satoshi Nakamoto developed a white paper that established the model for blockchain, including the hash method used to timestamp blocks. In 2009, Satoshi Nakamoto implemented a blockchain using the bitcoin currency. To this day, no one knows for sure who Satoshi Nakamoto is.
Interest in enterprise applications of blockchain has grown as the technology evolved and blockchain-based software and peer-to-peer networks designed for the enterprise came to market. Around 2014, blockchain technology applications -- distinct from their use in cryptocurrencies -- began to emerge as experts identified potential uses of the technology for other types of financial and organizational transactions.
Some specific early examples of enterprise applications include the following:
- In 2016, the online retail company Overstock.com used blockchain to sell and distribute more than 126,000 company shares. That marked the first time a publicly traded company used blockchain to support stock transactions.
- In 2018, Ticketmaster, the entertainment ticketing software and services company, bought blockchain technology provider Upgraded, which converts traditional tickets into secure interactive digital assets.
- In early 2020, blockchain company Theta Labs partnered with Google Cloud. The partnership allows Google Cloud users to deploy and run nodes from Theta's blockchain network.
- In 2021, NFTs became mainstream, permitting digital assets to be bought, sold and traded on blockchain platforms.
In recent years, several blockchain technology trends have arisen, including decentralized finance (DeFi), a type of financial framework based on the ethereum blockchain network. DeFi is different from centralized finance models within cryptocurrency markets in that there's no centralized authority that controls or intercedes in transactions.
The future of blockchain
Technologies such as AI, IoT, NFTs and the metaverse are expected to be greatly influenced by blockchain. Blockchain is also driving advancements in virtual reality by facilitating seamless interoperability between metaverse platforms and games, enabling users to easily transfer assets and characters across different virtual worlds.
Sharding, a technique to improve blockchain scalability by dividing it into smaller chunks for parallel transaction processing, is also gaining wider adoption. Initially discussed in the ethereum community in 2013, blockchain platform Zilliqa first adopted the technique. While sharding addresses scalability issues, full-scale sharding is still being developed for major platforms, including ethereum, with plans for future upgrades like ethereum 2.0.
However, blockchain is also facing legal and regulatory challenges, as well as controversies surrounding fraudulent activities, such as the high-profile collapse of exchange service FTX. Despite this, enterprises continue to invest in blockchain and its applications, most notably through the rise of NFTs and the NFT marketplace.
Blockchain is a growing enterprise technology. Learn more about it in our ultimate enterprise guide to blockchain.
Alexander Gillis also contributed to this definition.






