
How to use security as code to achieve DevSecOps
Security as code helps organizations achieve DevSecOps and shift-left security. Learn about SaC's benefits, challenges and implementation best practices.
Traditional application development methods have rapidly become outdated -- especially when it comes to application security. The growing threats of software vulnerabilities and coding errors mean developers can no longer create applications and not include security throughout the stages of the software development lifecycle.
Security used to be checked at the end of the development process, which often increased workloads on security and development teams and slowed go-to-market efforts.
Today, security as code (SaC) is becoming key to implementing a DevSecOps methodology. Whereas DevOps represents collaboration between developers and IT operations teams, DevSecOps takes it a step further to also include security teams.
What is security as code?
SaC is an approach that integrates automatic security checks, tests and controls throughout the software development lifecycle (SDLC). The goal is to identify and mitigate application security threats without affecting development time or creating bottlenecks. SaC keeps security top of mind throughout every phase of development, from inception to deployment. This is referred to as shift-left security.
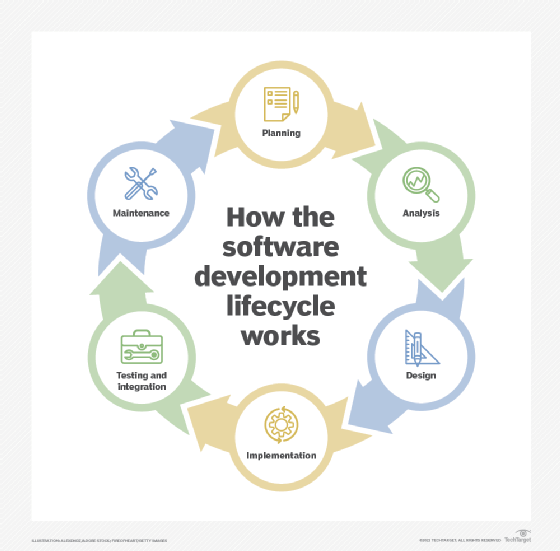
By shifting security left, security flaws are discovered earlier in the development cycle, enabling teams to solve issues as they arise.
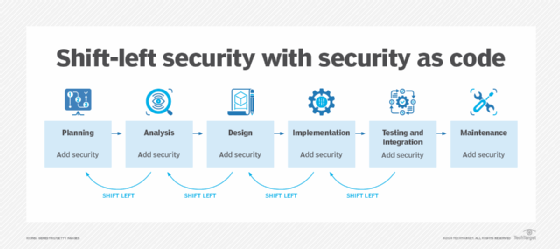
SaC involves the following components, which run automatically in the continuous integration/continuous delivery (CI/CD) pipeline:
- Access control ensures only those who are authorized to use the system receive access.
- Policy management determines what security practices are required. It is essential for governance, risk and compliance because they define the key attributes of the software.
- Vulnerability scanning automatically detects vulnerabilities and weaknesses in software code at each SDLC stage.
- Security testing and validation identify flaws in code that could affect the confidentiality, integrity and availability of the software and data.
Although SaC is primarily the province of cybersecurity teams, it is also an important activity for developers and operations teams. DevSecOps and SaC enable the three teams to work under a common umbrella, boosting collaboration.
SaC is related to infrastructure as code (IaC), which automates the addition and update of infrastructure components, such as databases, servers and storage.
No single tool exists that enables SaC. Rather, a combination of the following tools, processes and technologies helps organizations deploy SaC:
- Static application security testing. Checks code line by line for misconfigurations and security vulnerabilities.
- Dynamic application security testing. Runs an application at each development stage to find operational security weaknesses and vulnerabilities.
- Software bills of materials. Document all code, licenses and libraries in use to enable DevSecOps teams to stay on top of third-party and dependency vulnerabilities.
- Vulnerability scanners. Automatically discover and mitigate common misconfigurations and vulnerabilities.
- Access control and policy management. Limit who and what can view or use software code to prevent unauthorized access.
What are the benefits and challenges of security as code?
SaC provides organizations with numerous benefits but also presents some challenges.
Benefits of SaC include the following:
- Identifies and fixes security issues preproduction.
- Facilitates collaboration among development, security and operations teams as part of DevSecOps.
- Enables implementation of effective security configurations at all stages of the SDLC.
- Automates the development process across CI/CD, reducing the likelihood of human error.
- Helps speed development using automated security reviews.
- Helps achieve compliance with applicable security standards and regulations.
- Keeps software aligned with company policies and standards for performance and functionality.
- Enables organizations to reduce costs because vulnerabilities are found earlier in the SDLC.
- Improves postrelease maintenance by identifying and fixing issues before production.
- Provides a security audit trail for future analysis.
- Helps prevent data breaches, which can financially and reputationally harm a company.
Challenges of SaC include the following:
- Initial costs. While SaC can help organizations save money in the long run, expect high investment costs when implementing new tools and training teams.
- Redefinition of management roles. Organizations must establish who is responsible for SaC activities to ensure a chain of command.
- Corporate culture. Teams might need to make adjustments based on new workflows or other activities if security and development teams aren't used to collaborating.
- Development delays. Expect delays when implementing SaC. Teaching users how to deploy new tools could slow the development process, as can added security tests and checks.
Security-as-code best practices
The following best practices can ensure SaC adoption results in applications that are secure, compliant and ready for production:
- Establish a project team that includes representatives of the business unit(s), software developers and security team members.
- Develop a SaC project plan that includes how to automate key processes and code implementation.
- Determine security issues that might arise during the different SDLC stages.
- Collect application user stories to identify feature requirements from an end-user perspective.
- Evaluate and select tools that facilitate the SaC project.
- Ensure compliance with required standards and regulations through automated tools.
- Use the testing stage to validate and optimize embedded security measures.
- Schedule regular progress meetings, and keep senior management updated.
- Establish postdeployment maintenance activities to ensure the application and its security measures are performing as designed.
Paul Kirvan, FBCI, CISA, is an independent consultant and technical writer with more than 35 years of experience in business continuity, disaster recovery, resilience, cybersecurity, GRC, telecom and technical writing.







