
JJ'Studio - Fotolia
Healthcare IoT security risks and what to do about them
Healthcare IT and security administrators must understand the evolving challenges of protecting healthcare IoT devices and data to keep patients safe.
Healthcare organizations must practice a careful balancing act to get the advantages of connected devices without adding too much risk to patient safety.
Healthcare providers and patients increasingly introduce devices into healthcare networks. Over the past five years, IoT technology has improved patient care and healthcare facilities, but its growth has also prompted an increase in cyberthreats. These devices are used for inpatient and outpatient monitoring, asset tracking to help healthcare workers more easily find equipment and automating HVAC systems or lighting to reduce the spread of infection and keep costs down. Each instance of connected medical devices can streamline workflows that improve the lives of patients and healthcare professionals, but they also provide a larger attack surface.
"Attacks are getting more sophisticated. [451 Research has] definitely seen a sharp uptick in attacks on medical devices during COVID-19," said Christian Renaud, research director of IoT with 451 Research, part of S&P Global Market Intelligence. "We've seen an increase in attacks on IoT devices in general, but especially in the healthcare sector."
Major events influence healthcare IoT security practices
Major breaches over the years depict the seriousness of growing medical cyberthreats and have forced manufacturers, regulatory bodies and healthcare organizations to put more emphasis on healthcare IoT security.
In 2016, security research organization MedSec and investment firm Muddy Waters Research identified a vulnerability in a St. Jude Medical cardiac device, where an attacker could send repeated messages to the device until it depleted the battery. Researchers claimed it would crash the St. Jude -- now owned by Abbott -- pacemakers and defibrillators. The controversial handling of the vulnerabilities led the U.S. Food and Drug Administration (FDA) to issue cybersecurity guidance and more general medical device guidance.
At Black Hat 2018, many researchers revealed significant insecurities in medical IoT devices. Among them, researchers Billy Rios, founder of WhiteScope security firm, and Jonathan Butts, CEO of QED Secure Solutions, demonstrated how attackers could access a Medtronic pacemaker remotely and administer or withhold shocks to patients.
WannaCry ransomware is one of the most well-known cyberattacks that targeted healthcare systems, starting in 2017. Hackers used WannaCry to target vulnerabilities in the Windows OS and prevented healthcare professionals from accessing affected devices.
Cyberattacks were not the only factor that forced manufacturers and security professionals to improve healthcare IoT security. In 2016 and 2018, the FDA issued post-market and premarket cybersecurity recommendations for manufacturers to design and maintain healthcare IoT security. Organizations that purchase medical devices for healthcare facilities, such as HealthTrust and Mayo Clinic, also established their own procurement requirements for medical device manufacturers. These requirements pushed manufacturers to build security into their design.
 Mike Nelson
Mike Nelson
"HealthTrust, [with their procurement guidelines], introduced potential pain for the manufacturers," said Mike Nelson, vice president of IoT Security at DigiCert, a security certification company located in Lehi, Utah. "Manufacturers spend money where there is significant pain or there's significant opportunity for them to make money. And the cost of recovering from the damage will be much more than preventing the damage."
Ensure patient safety is the top priority
Healthcare IoT security vulnerabilities represent a more significant threat than vulnerabilities in consumer devices because they could lead to physical harm. Healthcare professionals and patients rely on accurate data to make care decisions and administer treatment.
 Karl West
Karl West
"If a device is leveraged as an entrance to get into and alter information associated with a device that affects the delivery of care, then our biggest concern is a patient safety issue," said Karl West, chief information security officer at Intermountain Healthcare located in Salt Lake City.
Although West said he hasn't personally seen patient safety compromised by an attack, he said it's always a concern. Attackers can also plant a virus on an IoT device and use that as an entry point to other parts of a healthcare network as part of a ransomware or distributed denial-of-service attack.
Nelson said he knows firsthand the potential risk of medical IoT vulnerabilities. He uses a continuous glucose monitor and an insulin pump for his diabetes treatment. The glucose monitor collects a blood sample to determine what Nelson's glucose level is and alerts him on his phone via Bluetooth. A hacker could perform a man-in-the-middle attack and manipulate the value reported through his phone. This could lead him to inject a dangerous amount of insulin. If a piece of code is compromised on a device, the attacker can change the device's behavior, disable it or gain access to other devices.
IT/OT convergence and legacy devices present additional challenges
With IoT technology, new devices come online every day and IT admins might find it challenging to keep an updated inventory. Devices can enter a network as part of a business initiative without IT being involved, making device discovery critical for IoT security. Operational technology (OT) professionals don't always prioritize security best practices and IT professionals don't always know how security practices will impede operations.
 Christian Renaud
Christian Renaud
"A lot of what we would consider traditional IT approaches of just firewalling everything off might break the workflows that expedite a patient through a course of care in a very quick way," 451's Renaud said. "It's critical to have both IT and non-IT people at the table for the co-creation of these use cases or workloads."
The risk extends to any connected device brought onto the network, even patients' wearables or smart devices that connect to the guest network.
"Even if we've built all of the controls -- all the protections around the guest network -- if you're not looking, there are lots of illegal activities going on," West said. "[Patient devices] come in and there are [viruses or malware] that could spread into the healthcare network."
Legacy equipment also presents a security challenge when connected to the network. In healthcare organizations, many machines that are multimillion-dollar investments do not get replaced until they are fully depreciated, Renaud said. Connecting these legacy devices creates vulnerabilities. Legacy equipment might not follow consistent protocols, vary based on vendor and might not be able to receive over-the-air updates to maintain their security.
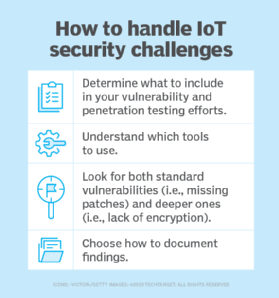
Ways to secure healthcare IoT devices
Cybersecurity experts can take many actions to bolster healthcare IoT security, including these five steps:
1. Inventory devices. Develop an exhaustive map of all assets, because healthcare organizations can't secure what they can't see, Renaud said. Many IoT devices are brought in without a risk assessment because they provide value. For example, a patient might bring in a Google Home or Alexa virtual assistant for music or entertainment. Some manufacturers offer tools to assist with inventory that can detect IoT devices on the network without disrupting their functionality, even if they don't have full OSes. IoT tools can also identify which OS is running on the device.
2. Follow standard best practices. Experts must follow general security best practices for healthcare IoT devices, such as eliminating hard coded passwords, firewalls and encryption. They must do a risk assessment before they deploy devices to understand what vulnerabilities exist and monitor network traffic for anything out of the norm using behavioral analytics profiling. Devices and software should be updated regularly.
3. Implement effective authentication. Deploying public key infrastructure and digital certificates can authenticate connections with the network, other devices and the electronic health record system, and ensure data packages are not manipulated while in transit from man-in-the-middle attacks.
4. Segment networks. Administrators must insulate devices that don't have built-in controls. If a device must be used for patient care, admins can turn off its capability to connect to the internet. If the device must connect, healthcare organizations can work with the vendor to identify where the device needs to connect and only allow those connections, creating an allowlist. Healthcare organizations can also denylist any known harmful sites from connecting to a device. System administrators must segment public networks from the rest of the network, restrict access to assets and events on a virtual LAN, or segregate traffic by department, Renaud said. Legacy devices can be wrapped with gateways to secure the physical connection to the device.
5. Use the right tools. Healthcare organizations can use tools that simplify IoT security. Some platforms automate the management of massive amounts of data and devices and can control authentication certificates. Manufacturers have also developed medical device tools that can identify what a device is, what data is collected from it and where it connects to the internet, Intermountain's West said. IoT analytics platforms can help administrators monitor network traffic and approve or deny connections.







