What is a unique identifier (UID)?
A unique identifier (UID) is a numeric or alphanumeric string that is associated with a single entity within a given system. UIDs make it possible to select that entity so that it can be accessed, updated and interacted with.
Unique identifiers can be assigned to anything that needs to be distinguished from other entities, such as individual users, companies, machines, database entries or websites. These distinctive values are usually assigned depending on the needs of the specific application but can either be randomly auto generated with an algorithm, allocated incrementally or chosen by the user.
Examples of UIDs
While UIDs can take a variety of forms depending on the application, the following are a few examples:
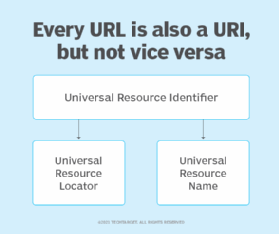
- A Uniform Resource Identifier (URI) is a text string identifier that makes content addressable on the internet or other networks by uniquely targeting items such as text, video, images and applications.
- A Uniform Resource Locator (URL) is a particular type of URI that targets webpages so that, when a browser requests them, they can be found and served to users.
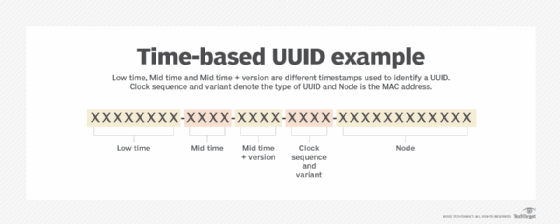
- A Universally Unique Identifier (UUID) is a 128-bit hexadecimal number used to uniquely identify data objects or entities on the internet. There is no central UUID issuing authority, but the possible space is large enough to encompass the vast number of internet-connected resources.
- A Globally Unique Identifier (GUID) is a form of UUID that Microsoft products generate. These can identify an entity such as a Word document or Active Directory user or group.
- A Bank Identifier Code is a unique identifier for a specific financial institution that participates in international bank exchanges.
- A Unique Device Identifier is a 24-character string assigned to all Apple devices, including iPhones, iPads and macOS computers.
- A service set identifier is a sequence of characters that uniquely names a wireless local area network (LAN).
- A National Provider Identifier is a unique 10-digit identification number required by the Health Insurance Portability and Accountability Act for all healthcare providers in the United States.
- A media access control address is a computer's unique hardware number in a LAN. In a MAC address, the first half is issued by a central authority to each device manufacturer, and the manufacturer is responsible for the second half.
Other, more basic ways to uniquely identify an entity or user include by Social Security number, email address, username and phone number.
How to create a UID
The defining characteristic of a UID is that it is unique; no other object can share the exact same UID. So, when creating a new UID, some mechanism is required to ensure its uniqueness. It's also vital that the potential size of the UID is large enough to encompass the potential number of objects to be identified. For systems with only a few objects, a simple system may suffice; for large systems with many objects that have multiple agents issuing UIDs, a complex system may be needed.
If two objects share the same UID due to a breakdown in the system, it is often called a collision.

In a sequential or serial numbering system, a single number is incremented each time a new UID is issued. These are often the simplest to implement, but it is important that a central authority enforces that each UID is only used once to prevent collisions.
Some systems allow for user entry, such as a username or email address. A central database enforces the uniqueness of these entries.
In a random numbering system, a number is randomly picked to identify each object. If the possible number space is much larger than the number of potential objects, you can be reasonably sure that it is unique.
In a hash system, a cryptographic one-way hash function is used to create a UID. With a hash function, no central authority is needed to enforce uniqueness. While it is possible for a hash to not be unique, it is quite unlikely. For extremely large databases, this tradeoff of potential for collisions versus decentralization may be worth it.
Some systems may use a combination of these approaches -- for example, a sequential date code prefix combined with a random suffix.
Uses of UIDs
The most widely known use of unique identifiers occurs when users register for a website or service. Customers are often provided with a username or user ID that enables the company they are registering with to differentiate them within their system. Quite often, these UIDs are simply a user's email address or phone number. These identifiers are then used for security and login purposes.
In a database or spreadsheet, unique identifiers may be designated as a specific column or field to help make sorting and filtering through information easier. In a database, the UID of a row is often called the key, and it is used to ensure that the correct data is accessed when doing a read or write.
Another popular application of UIDs is in a physical supply chain. Manufacturers often mark individual pieces of a larger component, such as computer parts, or an entire product with a serial number. This enables users to trace back the origin of the product in case of a malfunction, defect or recall.
Most countries also assign a UID to each citizen to help with taxation and government benefits identification. Since many people may share the same name, relying solely on a name quickly proves infeasible in any reasonably large country. The combination of name, date of birth and a country-specific UID reasonably identifies an individual for a government's purposes.
Unique identifiers are also commonly used within the healthcare industry. Instead of reporting medical information with a patient's name, a personal code is created. This code combats issues of patient privacy, as well as eliminates the possibility of duplicate reports.
UID vs. IUID vs. UII
Within the Department of Defense (DOD), there are three related acronyms associated with the standard of government property. The first is the Item Unique Identification (IUID) Registry. This registry stores information for the DOD about how to track, maintain and deploy government assets. Items are added to the IUID Registry if their acquisition cost is over $5,000, they are mission-critical or they are high risk.
The second and third acronyms are connected with each item in the registry. An item's UID is the physical marking on the item, typically in the form of a barcode, that distinguishes it from other items. An item's unique item identifier (UII) refers to its entry value in a database. UIIs are usually machine-readable and help contractors track each item digitally through all stages of its lifecycle.
Learn how GUIDs are used in designing a custom Hyper-V Integration Services component. Also, explore how to use a public and private key to handle electronic documents using digital signatures, see how to ensure security for three types of digital identity and discover if long URLs are better than short URLs.






