Risky business? How to manage IoT security in the enterprise
Nearly every week, we hear about a new cyberattack or security breach. In fact, more than 1.7 billion identities have been exposed in data breaches in the past eight years. As the world becomes increasingly interconnected, organizations become susceptible to more risk. While IoT presents new opportunities, it also creates new security risks that enterprises must address. Having a high number of new endpoints due to IoT requires an increased focus on security.
As organizations accelerate their digital transformation plans and processes, many companies will choose to stop updating or supporting old versions of their software, exposing themselves to cyberthreats, system failures, increased costs and future planning limitations.
On top of increased emphasis on advanced technology and systems, organizations are now accountable for protecting, structuring and identifying data, and complying with new regulations like GDPR. Preventing hacks and managing technology risk can be a challenge for organizations of any size. The consequences of technology hacks can be detrimental, with organizations facing legal liabilities, penalties, costs and fines, not to mention the impact on brand reputation. Luckily, there are easy steps organizations can follow to successfully manage IoT security and assess risk in the enterprise.
Avoid technology obsolescence
Actively assessing the technical fit of applications is one of the first lines of defense when taking steps to prevent risk in the enterprise. Technology obsolescence can be one of the biggest factors that leaves your organization exposed to hackers and outside threats. Unfortunately, many companies do not know the true lifecycle of their technology and software, and fail to run updates which leads to risk. Many enterprises run on complex, legacy technology and applications and ignore the risks of end-of-life technology. The technology risk for applications and business capabilities needs to be evaluated based on the underlying IT components. By identifying underlying IT components that are putting applications at risk, you can mitigate those threats to security. Regular and frequent software updates re-engage existing users, fix bugs or issues, and patch problems before hackers can exploit them. Using a dashboard to track and assess the risk of your organization’s application landscapes and IT components is an easy way to plan and manage lifecycle information and retire technology in the enterprise as needed.

Example of a heat map showing the technology risk of different applications due to underlying IT components.
Analyze impact
Up-to-date technology product information is a critical and efficient resource for enterprise architects to assess internal technology risks. Setting up a basis to manage and automate updates and application lifecycles through a standard catalog provides a single view of vendor and application information, which can help enterprise architects visualize and proactively update and prevent technology obsolescence. Using up-to-date and easy-to-read reports, enterprise architects can quickly analyze the business impact of each application and understand the severity of risk, should an outage or breach occur. Understanding the impact and dependencies of each application can help determine when and where risk lies.
Implement microservices
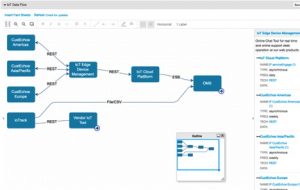
Determining how device networks will communicate, how data will be processed, which applications or systems to invest in, and which teams will oversee IoT endeavors will be vital to managing IoT risk in the enterprise. IoT generates massive amounts of data, and organizations must be prepared to maintain the high-volume influx. From devices to cloud platforms and analytics platforms, transparency throughout the infrastructure is critical to connect to all data, process it and deliver relevant pieces to the business owners. Microservices enable organizations to quickly deploy, maintain and account for the volumes of data that IoT brings, while breaking down silos.
The demands of IoT alone would slow any monolithic architecture to a snail’s pace, dealing with integrations of heterogeneous connections, devices, applications, sensors, protocols and servers necessary for an enterprise to digitize in the age of IoT. Not only are microservices a cost-effective solution for enterprises, but they enable agility and innovation separate from monolithic, legacy architecture. With applications being developed and deployed independently, enterprise architects can also easily maintain each lifecycle and the security of every application. Microservices help organizations better pinpoint internal bugs and areas of vulnerability, and quickly patch and revamp without shutting down the entire system of a monolithic architecture.
Firm up physical and digital security processes and standards
Ensuring end devices and physical technology are safely stored is a simple step to protecting your organization from curious minds who want to tamper or tinker with new hardware devoted to IoT endeavors.
On the digital side, there are several measures that should be taken to combat risk, including deploying firmware updates to every IoT device, as these updates may contain important security patches that protect your organization from unauthorized access. Assess the security and strength of your authentication process when it comes to accessing IoT devices in your network. Avoid using default logins and simple passwords that hackers can easily guess or steal to manipulate your IoT devices. Strengthening authentication processes and implementing firewalls in order to limit access and better monitor devices is an important layer of IT security and key to risk prevention.
From a network perspective, consider isolating your IoT devices using virtual LANs, routing or creating separate networks for devices to run on. Secure data by deploying end-to-end encryption, protecting it as it crosses the network and while it’s stored on the back-end server. If embedded IoT devices cannot perform natively, use infrastructure techniques such as encrypted tunnels to properly secure data.
Create a plan
Even with the most stringent security protocols in place, breaches may still happen. Creating a plan for how to respond is quite possibly the most important step of all when preparing for and being proactive when it comes to managing risk in the enterprise. Having a plan in place will ensure your team knows what to do in the event of an IoT security breach, and can ensure things don’t get worse in an emergency situation.
Such a plan requires transparency and accuracy about what you have regarding applications, processes and IT components, as well as their relation to each other and their context to projects, user groups, business capabilities and services offered by IT or any other department — and this is exactly what we bring to the table.
In a world where it’s nearly impossible to avoid digitization, IoT is uncovering opportunities and insights at an unprecedented pace. As organizations eagerly adopt new technology and applications, it’s important to ensure your enterprise architecture can handle the demands of IoT and that there are protocols in place to provide total data security. Being proactive and preparing can save organizations from paying the price — both financially and in loss of consumer trust — when it comes to security breaches.
All IoT Agenda network contributors are responsible for the content and accuracy of their posts. Opinions are of the writers and do not necessarily convey the thoughts of IoT Agenda.