2018 prediction: Why that smart fish tank hack should have you swim to SIEM
Remember that story of the smart fish tank hack in July 2017? Cybercriminals used the connected device, which controlled and regulated temperature, salinity and feeding times (seems innocent, right?), to hack into a North American casino’s network. They were then able to send data to an external device in Finland.
It’s tempting to dismiss that story as “truth is stranger than fiction,” yet we’ve also witnessed distributed denial-of-service (DDoS) attacks powered by IoT botnets and zombie computers running rampant everywhere.
Cloud services, IoT and mobile workstyles are powering new ways of creating, working and connecting at enterprises globally. Yet, as companies leap ahead with new capabilities and processes, they also need to brace for a coming fusillade of cyberattacks. We should all learn from the fish tank hack, and swim quickly to security information and event management (SIEM) as a utility.
Consider, by coupling SIEM with IoT and branch location connectivity technology, like SD-WAN, SIEM will be able to reach every edge of the highly distributed enterprise. This is known as SIEM as a utility. Most companies are witnessing a 10x growth in the number of devices they have on their network. Traditional SIEM isn’t set up to handle managing connected devices at scale, because it requires extensive bandwidth, CPU and staff. A new approach is needed. Plus, any connected devices are low value, simple assets that can successfully be managed with automated SIEM services.
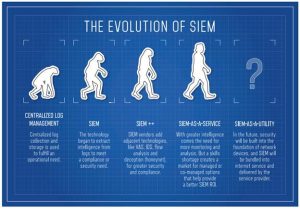
SIEM is rapidly evolving in functionality and ubiquity
SIEM’s ability to centralize and aggregate billions of event logs from devices makes it a natural choice to house advanced threat lifecycle management capabilities. SIEM has evolved to now include user and entity behavior analytics (UEBA), and security orchestration and automated response (SOAR).
UEBA triggers alerts when unusual user or entity behavior occurs. That’s especially critical because stolen or misused credentials are involved in three out of every four network attacks. It also analyzes behavior, such as users logging into nonstandard locations or mass downloads of data, issuing security alerts when they occur. SOAR consolidates data sources, uses threat intelligence feeds and automates a security response quickly and efficiently.
How SIEM will continue to develop
SIEM platforms are evolving to encompass machine learning concepts and orchestration capabilities, enabling companies to manage devices at the furthest ends of the digital enterprise. That’s good news indeed for enterprises that want to use IoT to automate processes, transform the customer experience and use the wealth of data for predictive analytics.
SIEM as a utility is the answer to enterprises’ questions about how to grow strategically at scale, while not compromising safety and soundness.
After all, when it comes to connected devices like one casino’s smart fish tanks, no one wants their data swimming away due to unmanaged IoT connections.
All IoT Agenda network contributors are responsible for the content and accuracy of their posts. Opinions are of the writers and do not necessarily convey the thoughts of IoT Agenda.