
7 Reasons Identity and Access Management Is Important
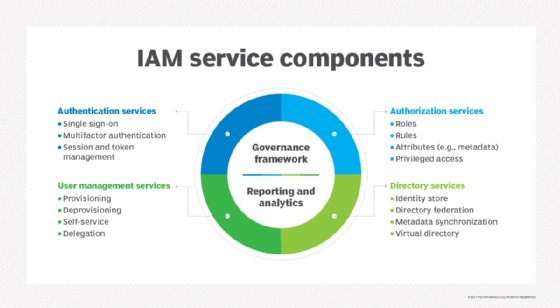
Identity and access management (IAM) is a framework of business processes, policies and technologies that makes it easier for organizations to manage electronic or digital identities. IAM frameworks enable IT managers to control user access to critical information within their companies.
IAM tools offer role-based access control to allow system administrators to regulate access to systems or networks based on the roles of individual users within the organization. Creating effective IAM policies, such as a privacy policy, protects data privacy by limiting user access to resources and protects against unauthorized access.
IAM technologies include password-management tools, single sign-on systems (SSO), two-factor authentication, multifactor authentication (MFA), privileged access management (PAM) and privileged identity management (PIM). These tools let organizations securely store identity and profile data, as well as data governance functions, to ensure that only necessary and relevant data is shared.
IAM ensures greater control of user access. By identifying, authenticating and authorizing users, as well as prohibiting unauthorized users, IAM security boosts the efficiency and effectiveness of access management across an organization.
Identity management systems can be deployed on premises, provided by a third-party identity provider through a cloud-based subscription model or deployed in a hybrid model.
Here are seven reasons why identity and access management is important:
1. Enhances Data Security
Controlling user access allows organizations to eliminate instances of identity theft, data breaches and illegal access to sensitive corporate information. IAM can prevent the dissemination of compromised login credentials, prevent unauthorized access to a company's network as well as protect against hacking, ransomware, phishing and other types of cyberattacks.
2. Streamlines IT Workload
When a security policy gets updated, all access privileges across an enterprise can be changed at one time. IAM can also help cut down on the number of tickets employees send to the IT helpdesk for password resets.
3. Helps in Regulatory Compliance
IAM can help organizations meet the requirements of industry regulations to ensure the security and privacy of customer data, such as the Health Insurance Portability and Accountability Act (HIPAA), Sarbanes-Oxley (SOX) and the Payment Card Industry Data Security Standard (PCI-DSS)
4. Reduces Human Error
With an identity and access management tool in place, companies can eliminate manual account and permission errors because the IT department no longer has to manually manage access rights to data. In addition, IT no longer has to deal with careless employees who may make mistakes that can result in costly fines.
5. More Effective Access to Resources
Users who receive access through a centralized platform benefit from using SSO technology as it limits the number of interactions they have with security systems and increases the probability that they will succeed in their legitimate attempts to access resources.
6. Confidentiality of Data
By restricting access for those who don't need to use certain apps or files, organizations can better secure sensitive data as well as enable project managers to have a clearer picture of which users are associated with which projects.
7. Helps Manage Access Across Browsers and Devices
One benefit of cloud applications is that users can access them from any device that's connected to the internet. However, the downside is that more applications means more URLs and passwords. In addition, the increase in mobile devices means that IT administrators must manage and support another access point.
Cloud-based IAM tools can provide browser-based SSO to all user application as well as enable access to those same services from users' mobile devices.
Technology That Supports IAM
A number of IAM tools support identity and access management, including:
Azure Active Directory (Microsoft)
Microsoft Azure Active Directory is an IAM cloud platform that companies can deploy to manage users and groups. It helps secure access to on-premises and cloud applications, including Microsoft web services, such as Office 365, and other non-Microsoft software as a service applications, including Box and Salesforce. Azure Active Directory works across multiple platforms and devices and integrates with on-premises Active Directory.
Oracle Identity Cloud Service
Oracle Identity Cloud Service provides identity management, SSO and identity governance for applications on-premises, in the cloud or for mobile devices. Oracle Identity Cloud Service enables employees and business partners to securely access applications at any time, from anywhere and on any device. The cloud-based identity management system works by associating specific rights and restrictions with the established identity of each user. Oracle Identity Cloud Service governs how employees, contractors, vendors, partners, customers and other stakeholders use IT resources and protects access to sensitive data.
RSA SecurID Access
The RSA SecurID Access is geared toward mitigating identity risk. It combines identity governance and user lifecycle management with access management and authentication in one suite. RSA's IAM suite aims to offer users secure, anywhere access from any device to the their on-premises or cloud applications. RSA SecurID Access protects resources with a broad range of authentication methods, including push notifications, biometrics, one-time passwords as well as traditional hardware and software tokens.
OneLogin Access
OneLogin Access offers a cloud-based identity and access management tool that provides simple single sign-on, making it easier for companies to secure and manage access to web applications in the cloud and behind their firewalls. OneLogin Access simplifies identity management with secure, one-click access for end users to all cloud and on-premises applications on any device. OneLogin Access immediately disables access to applications for employees who leave a company or change roles within the organization in real time by removing them from Active Directory (AD).
Issues with IAM
Despite the benefits of IAM, there are still some challenges associated with it.
For example, it's often difficult for companies to screen identities and approve access requests because the data lives in different locations and business units. People requesting access often hit roadblocks during the process, causing them to escalate their requests to upper management and bypass the proper vetting process.
Furthermore, the individuals who approve access requests often don't know which employees actually need access to confidential data.
Not having a centralized, authoritative identity repository for users can make identity reconciliation challenging. Additional problems may occur when privileges on systems exceed access levels or don't have access levels that had been granted and provisioned in the past.
Provisioning and deprovisioning identities can also be an issue in the face of ineffective manual provisioning processes. And companies that don't remove inaccurate IAM privileges, or have to clone access profiles, will also struggle.
Other issues include:
- Not developing rule-based access
- Outdated access management policies or access management policies that don't exist
- No support for centralized access management tools, such as single sign-on and directories
- Not automatically removing identities and access privileges when an employee is terminated or otherwise leaves the company.








