
What is ransomware as a service (RaaS)?
Ransomware as a service (RaaS) is a subscription-based business model that enables threat actors, also called affiliates, to launch ransomware attacks by accessing and using predeveloped ransomware tools.
Ransomware is a type of malware that locks and encrypts a victim's data, files, devices or systems, rendering them inaccessible and unusable until the attacker receives a ransom payment.
In RaaS, the author of the ransomware makes the software or pay-for-use malware available to its affiliates, who use it to hold an organization's data hostage. The use of RaaS lets affiliates receive a percentage of each successful ransom payment, entering an area of extortion practices previously exclusive to ransomware authors or experienced hackers.
This business model enables the malware author to scale earnings from their software, incurring less personal risk than if using it themselves. Offering their software to others shields the malware author from the consequences of the final crime by having another person perform the actual act of ransom. RaaS is also useful for threat actors who do not have the technical skills to create the malicious software themselves.
Despite ransomware and RaaS being considered criminal exercises that are almost always illegal worldwide, these types of cybersecurity breaches have become more common.
How does ransomware as a service work?
RaaS is all about providing ransomware in a software as a service (SaaS) model. At the top of the organizational hierarchy is the RaaS operator who develops the ransomware payload that encrypts user data.
The ransomware operator also manages all back-end infrastructure to run the ransomware campaign. This involves the ransomware code, a portal that enables potential customers to sign up and use the service and customer service to support campaigns. Full-service RaaS operators also handle ransomware payments -- typically using a cryptocurrency, such as bitcoin -- and provide decryption keys to victims who pay the ransom. In addition, RaaS operators actively advertise their services on different underground forums across the dark web to recruit affiliates.
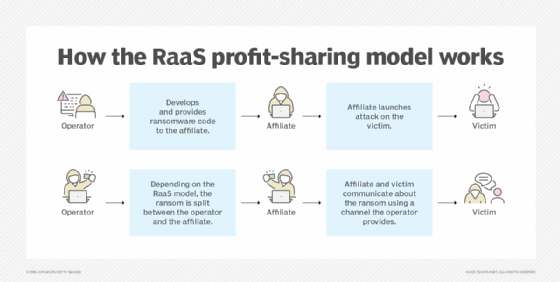
The affiliates are the parties that use the ransomware after agreeing to a service fee based on each collected ransom.
Types of RaaS models
There are several different business and revenue models for RaaS, including the following:
- Monthly subscription. As a SaaS model, RaaS is offered to potential users on a subscription basis. Users pay a monthly flat fee and receive a small percentage of each successful ransom.
- One-time license fee. The RaaS model is offered to users for a one-time fee. After they make a one-time payment, users gain indefinite access to services and do not have to share profits with the RaaS operators.
- Affiliate programs. An affiliate model has the underlying goal of increasing profits. The RaaS operator takes a predetermined percentage of every ransom payout made by victims.
- Pure profit sharing. In this business model, once the affiliate purchases a license, profits are split among users and operators according to predetermined percentages.
Ransomware vs. ransomware as a service
Ransomware as a service takes ransomware and turns it into a product for other potential malicious actors.
The ransomware itself is the actual malware payload that's used to encrypt the data of a victim's system. Once a system is infected with ransomware, a ransom demand is made to the victim to pay a ransom. When the victim pays the ransom, the attacker provides a decryption key to restore the encrypted data -- although the attacker might still decide to keep the data locked. Some ransomware might also be designed as double or triple extortion ransomware attacks, which provide more opportunities for the attacker to extort a ransom from the victim.
Ransomware developers provide RaaS to subscribers who pay to be affiliates of the program. RaaS expands the ransomware's accessibility and potential reach. Instead of a single group using ransomware code to attack victims, several groups of attackers can use RaaS to exploit victims with ransomware.
RaaS can also be more resilient than typical ransomware developed and deployed by a single threat actor. For example, RaaS operators are likely to have a professional infrastructure with the technical expertise to create new malware payloads while avoiding detection. Likewise, a specific RaaS operation can be more difficult to shut down, as catching an affiliate does not necessarily shut down the operators, and catching the operators does not necessarily shut down their affiliates. If an operator is caught, its respective affiliates can switch to another ransomware kit.
Examples of ransomware as a service
In recent years, ransomware authors have discovered the lucrative nature of running a RaaS operation. And there hasn't been any shortage of threat actor groups building out RaaS operations to spread ransomware across nearly every industry.
The following are some RaaS providers:
- RansomHub. Launched in February 2024, RansomHub RaaS is responsible for more than 210 attacks on water and wastewater facilities. It is believed to be the successor to Alphv, which has ties to Russian-affiliated countries.
- RTM Locker. Read the Manual (RTM) Locker emerged in early 2023. It evolved as a RaaS provider and is known to offer a standard affiliate-based business model. RTM affiliates are given a web interface to control their cybercrime operations along with a thorough explanation of the group's guidelines, goals and suggested offensive strategies.
- REvil. While there are multiple RaaS operators, REvil is one of the most active. It was implicated in the Kaseya attack, which affected at least 1,500 organizations in July 2021. The group was also allegedly responsible for an attack on meat producer JBS USA in June 2021, in which the victim paid an $11 million ransom. In March 2021, REvil was also identified as being behind a ransomware attack on cyber insurance carrier CNA Financial.
- DarkSide. Among the most notorious RaaS operators, this group is reported to be responsible for the Colonial Pipeline attack in May 2021. DarkSide is thought to have gotten its start in August 2020 and was particularly active in the first few months of 2021.
- DoppelPaymer. DoppelPaymer has been linked to several incidents, including one against a hospital in Germany in 2020 that resulted in the death of a patient.
- LockBit. LockBit first emerged in September 2019 as the ABCD virus, named for the file extension the group uses to encrypt victims' files. Among its attributes is its ability to automatically self-propagate in a target network, making it an attractive RaaS for would-be attackers.
- Maze. Maze appeared in 2019. Beyond encrypting user data, it also attempted to shame victims by threatening to share data publicly. The Maze RaaS officially shut down in November 2020. However, after their disbandment, cybercriminals have continued Maze's exploits using the name Egregor.
- Dharma. Dharma Ransomware first emerged in 2016 and was initially known as CrySis. There have been many Dharma Ransomware variants over the years, but in 2020, Dharma emerged in a RaaS model.
Many different instances of ransomware attacks have occurred through RaaS. Organizations should be vigilant and proactive about preventing these attacks.
How to prevent RaaS attacks
The following are some best practices to help mitigate the risk of ransomware:
- Ensure data backup and recovery. The first and arguably most critical step is to have a data backup and recovery plan in place. Ransomware encrypts data, rendering it inaccessible to users. If an organization has up-to-date backups that can be used in a recovery operation, this can reduce the effect of an attacker encrypting data.
- Update software. Ransomware often exploits known vulnerabilities in applications and operating systems. Updating software as patches and updates come out is necessary to help prevent ransomware and other cyberattacks.
- Use multifactor authentication. Some ransomware attackers use credential stuffing, where passwords stolen from one site are reused on another to access user accounts. Multifactor authentication reduces the effect of a single reused password, as a second factor is still needed to gain access.
- Implement phishing protection. A common attack vector for ransomware is email phishing. Having some form of anti-phishing email security in place can potentially prevent RaaS attacks.
- Use DNS filtering. Ransomware often communicates with a RaaS operator's platform using some form of command-and-control (C&C) server. Communications from an infected system to the C&C server almost always involve a Domain Name System (DNS) query. With a DNS filtering security service, organizations can identify when ransomware is attempting to communicate with the RaaS C&C and block the communications. This can help protect against infection.
- Implement XDR endpoint security. Another critical layer for ransomware protection is endpoint protection and threat-hunting technologies, such as extended detection and response (XDR) and antivirus software. These technologies provide capabilities that can limit ransomware risks.
- Manage third-party security. To avoid third-party breaches, businesses must monitor the security practices of all of their vendors.
- Restrict access. To avert security issues, companies should limit administrative and system access to people who genuinely require it.
- Educate staff. Regularly training employees on cybersecurity best practices and social engineering tactics can be an effective way for companies to prevent RaaS attacks and cyberthreats in general.
The future of RaaS
The frequency of targeted ransomware attacks is increasing as the adoption of RaaS services grows. For example, ransomware accounted for 44% of cybersecurity breaches in 2024.
Some current RaaS trends are likely to continue. Encryption algorithms and evasion techniques could improve, while operators design ransomware for more targeted and specific attacks. Multilayered ransomware, such as double and triple extortion attacks, is also becoming more common.
The cybersecurity threat landscape constantly witnesses the emergence of new ransomware variants, placing pressure on security teams to respond by enforcing patching programs and quickly addressing known vulnerabilities. One key area is generative AI, which has the potential to develop new custom ransomware variants and exploit vulnerabilities.
While it is difficult to determine the future trajectory of RaaS attacks with certainty, companies should proactively adopt measures to mitigate potential attacks.
Organizations across various industries face the risk of becoming targets of financially motivated cybercrime. Explore more about RaaS and other ransomware trends and statistics.