
Getty Images/iStockphoto
Verizon DBIR: Vulnerability exploitation in breaches up 180%
Verizon said it examined approximately twice as many breaches for the 2024 Data Breach Investigations Report -- 10,626 out of 30,458 total tracked incidents.
Listen to this article. This audio was generated by AI.
Vulnerability exploitation in breaches is up 180%, almost triple that of the previous year, according to Verizon's "2024 Data Breach Investigations Report."
Verizon's DBIR, published on Wednesday, is the telecom giant's annual report on data breach trends and overall cybercrime activity. This year's 100-page report touches on key themes and observations based on data gained between Nov. 1, 2022, and Oct. 31, 2023, including vulnerability exploitation, data extortion and human error.
Verizon said its researchers "witnessed a substantial growth of attacks involving the exploitation of vulnerabilities as the critical path to initiate a breach when compared to previous years." Verizon wrote that this huge spike came in part from last year's enormous MoveIt Transfer campaign, which was perpetrated by an affiliate of the Clop ransomware gang, as well as other campaigns involving zero-day vulnerabilities.
According to the report, Verizon researchers tied 1,567 breach notifications to the exploitation of the MoveIt Transfer zero-day flaw. Cybersecurity vendors estimated that more than 2,000 customers worldwide might have been affected.
"This was the sort of result we were expecting in the 2023 DBIR when we analyzed the impact of the Log4j vulnerabilities. That anticipated worst case scenario discussed in the last report materialized this year with this lesser known—but widely deployed—product," the report read, citing the 2023 Verizon DBIR.
David Hylender, senior principal of threat intelligence at Verizon and DBIR team manager, told TechTarget Editorial that the spike reflected both the influence of a few key campaigns as well as a shift from ransomware gangs toward data extortion-only campaigns.
"Certainly, the number was skewed by MoveIt. There's no two ways about that. But I think the trend element is true as well, because Clop was named as responsible for MoveIt, and this vulnerability just gave them ready-made victims," Hylender said. "They don't even have to encrypt the data anymore. I would be surprised if we don't see this kind of thing continue, because it's very lucrative."
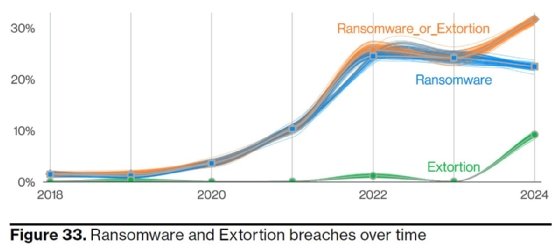
Verizon saw a slight decrease in the number of traditional ransomware attacks reported. However, when including the extortion-only, no-encryption data theft attacks, which are often conducted by ransomware actors, the number is up year-over-year. Ransomware and data extortion attacks were present in 32% of reported attacks, and 92% of industries experienced ransomware as a top threat targeting them.
Regardless of the type of attack perpetrated by ransomware gangs, Verizon researchers offered a warning to vendors like Progress Software that offer managed file transfer products. "As we gaze into our crystal ball, we wouldn't be surprised if we continue to see zero-day vulnerabilities being widely leveraged by ransomware groups," the report read. "If their preference for file transfer platforms continues, this should serve as a caution for those vendors to check their code very closely for common vulnerabilities."
Social engineering and silver linings
According to the Verizon DBIR, 68% of breaches involved a human element, such as human error, having credentials stolen or an individual falling for a social engineering attack. In addition, the median report time for phishing victims to click a link is less than 60 seconds, and more than 40% of social engineering attacks involved pretexting -- an attack type largely associated with business email compromise.
Although many organizations and individuals fall victim to social engineering attacks, some statistics are more promising. For example, the report said that security awareness exercise data contributed by Verizon partners, more than 20% of users identified and reported phishing attempts, including 11% of users who clicked on a phishing email. Hylender noted this was a notable increase year over year.
Taken as a whole, Hylender said the continued prominence of social engineering attacks as well as more positive statistics, such as higher reporting rates, reflect a kind of "arms race" between defenders and threat actors, with both parties constantly improving.
"Attackers are diversifying their portfolio. These ransomware groups are branching out into new things," he said. "And so the defenders are going to have to step up. And we talked about that -- a few ways they're doing that -- in the report, such as choosing some of security vendors more wisely. Look at how they do security inside their organization, how they own their product and make that a factor."
This year's DBIR represented the largest number of tracked breaches seen in the history of Verizon's report by far, Hylender said. Verizon examined 10,626 confirmed breaches of 30,458 incidents, which represents about twice the previous report. He chalked it up partially to new contributors joining the report this year. But he said many of the MoveIt Transfer attacks were publicly disclosed, which also contributed to the number.
Suzanne Widup, distinguished engineer of threat intelligence at Verizon Business, told TechTarget Editorial that in any case, the number of breaches represents merely "the tip of the iceberg."
"In our report, we know it's a sample -- a representative sample from what we've been able to tell. But we do know that there's a whole lot more that doesn't come to light. And whether that's because attacks are not publicly available for us to find or whether an organization is even reporting an attack based on what the laws are," she said. "We know that there are a lot of countries that don't require any kind of disclosure. It's obvious that this is the tip of the iceberg."
Alexander Culafi is a senior information security news writer and podcast host for TechTarget Editorial.






